One technology that has a place in some secure information sharing environments is PKI. Read Part 1, Part 2 and Part 3
Editor’s note: This chapter is excerpted from chapter 9 of Identity Management: A Business Perspective.
Public Key Infrastructure
PKI is a mechanism to add a layer of security to a user’s activity that makes it virtually impossible to circumvent, provided the mechanism for creating and distributing keys is strong enough. A PKI validation of a user’s identity can be trusted to a very high level. Man-in-the-middle attacks are not possible, and communication is secure.
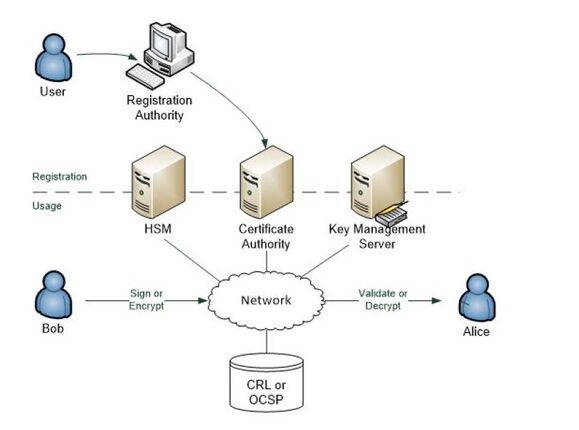
Figure 9.4 depicts the major components of a PKI environment.
Figure 9.4: PKI environment
Participants must first be enrolled in the scheme. The registration authority (RA) validates an applicant’s credentials and requests the generation of a certificate from the CA. The CA generates a key pair, or requests their generation from a Hardware Security Module (HSM), and creates a certificate. It writes the public key to a repository such as a certificate store and/or key management service and provides the private key to the user via a secure method. In a secure information- sharing environment, there will likely be a need to manage keys, including expired keys, for document decryption purposes.
Note: Classic PKI uses a certificate revocation list (CRL) of all compromised certificates that can be checked at any time. If a certificate is not in the CRL, it’s deemed to be valid (provided its expiry date has not been reached). A variant of the PKI standard allows for a certificate server to be made available via the OCSP protocol, which provides a positive assurance of a certificate’s validity.
The operation of a PKI environment is quite simple, and consists of two “actions”:
- Registration—Users register their participation in the PKI by accessing the RA, completing the necessary identity validation process, and requesting a certificate. The RA will then contact the CA, which will generate a key pair, usually via the HSM. The CA will then send the public key to the key management or certificate server and the private key to the user via a hardware token such as a smart card, or by emailing a link to a secure API to download the key to the private key store of the user’s system.
- Usage—There are two use cases:
- User digitally signs a document—The signing system uses the user’s private key to create a piece of code that’s attached to the document. When the recipient wants to verify the signature, they access the user’s public key to verify the signature.
- User encrypts a document—The encrypting system uses the recipient’s public key and creates a hash of the The recipient then uses their private key to decrypt the document.
The RA process has a direct bearing on the strength of the PKI. The RA’s process of verifying identities of applicants must be “vetted” to ensure it meets the required level of identity assurance. The methodology of generating keys and the way in which private keys are provided to users combine to indicate the robustness of the PKI. A very strong key-generation process can be compromised if private keys can be intercepted during their transmittal to the applicant.
The CA process must also be evaluated to ensure that the generation of keys is robust and that the management of the key store is appropriate. For instance, if a CRL is being used, the frequency of update must match the requirement for the PKI environment. In some cases, CRLs are updated as soon as a compromised certificate is identified—for example, when a staff member leaves the company’s employ. Sometimes the CRLs are updated nightly, but in other cases, CRL updates are only performed weekly. Given that a requirement of most PKIs is that the CRL or OCSP server should be contacted whenever a transaction is undertaken, the frequency of CRL or OCSP update must be fit-for-purpose.
Key management is another important consideration for a PKI deployment. Only trusted individuals should have access to the encryption keys, be they PKI certificate keys, database encryption keys, or even SSL session keys. Key management is an important activity and should require a four-eyes process for any key creation or rotation task.
The use of an HSM to secure keys and the use of corporately generated keys, rather than vendor-supplied keys, should be considered. For a PKI establishment,
a “key ceremony” should be undertaken whereby key managers are commissioned.
A related issue is the selection of the CA. At one end of the spectrum are highly secure CAs, typically military, with robust registration processes. At the other end are self-signed certificates that use exactly the same technology, but the level of security provided depends upon the RA procedures and the certificate generation process. One consideration is the selection of a root CA. If a seamless enrollment process is required, a public CA supported under the Windows environment will be required, but this will require the purchase of certificates. If self-signed certificates are used, this cost is eliminated, but users will need to import the company’s certificate into their browsers.
Benefits
It’s worthwhile reflecting on the benefits of deploying a well-thought-out, secure information-sharing environment. There are at least four benefits that should be balanced against the cost of deploying a solution. Part of the strategy planning should include a risk management exercise to evaluate their “expected values”:
- Reduced litigation costs—In the event of a security breach, there will likely be related, and probably expensive, litigation. It’s far better to avoid the breach in the first place.
- Reduced reputational-damage costs—Increasingly, as organizations know more about their customers, the need to protect this information increases. While members of the public will entrust organizations with their details, some quite sensitive, they equally expect that it will be adequately The reputational damage that a compromise might cause is significant and potentially disastrous.
- Reduced administration costs—The cost of administering corporate security is significant and, more often than not, inadequately captured. When a policy violation is identified, it is expensive to investigate the violation manually. Tools to reduce false positives represent a cost reduction, and management processes that automate investigations have short payback time frames.
- Better cultural awareness—The development of a security culture within an organization is fraught with It can easily go off the rails and cause frustration within the organization when staff experience constraints on their ability to do things with documents. For example, if someone who used to be able to send documents to an external business partner is now prevented from doing so, they need to appreciate why.
Conclusion
Secure information sharing is a seminal activity for organizations. Sharing information securely enables business to be conducted while protecting intellectual property and commercial-in-confidence information. Organizations should take a strategic approach to designing, commissioning, and operating their IT environments to provide the requisite protection.
A company’s identity and access management (IAM) environment must support secure information sharing by providing the necessary information to determine whether a requesting user has the necessary entitlements for access; this will allow the system to determine their specific rights to the requested resource. For a secure repository solution, this means providing access to the user ID of the requesting user so that it can be checked against the access control list. For a rights management sharing system, the IdP will typically need to provide more detail, such as the user’s department or workgroup membership, to allow a determination of the access rights they should be granted. For AD group-based systems, the IAM must ensure that the UID of the user is in the appropriate group. For certificate-based systems, this means that the certificate should be available from the data store.
Use Case: PharmaCo
|
Scenario |
PharmaCo is a pharmaceutical company that develops medicine for human consumption and application. The company has an active research and development group that is continually bringing new products to the marketplace. PharmaCo works with a large number of researchers employed at several different universities and research establishments nationally and internationally. Legal representation is external to the company, as is their marketing/advertising agency. PharmaCo is conducting clinical trials on a new drug to inhibit the progress of type 2 diabetes. It uses new university research that shows promise in the animal trials that have just been completed. |
|
Strategy |
In light of recent incidents of loss-of-IP at some of its competitors, PharmaCo has decided to institute a data-loss prevention environment that will reduce the likelihood of loss of sensitive documents, such as research findings, marketing campaign details, contract documents, and business plans. |
|
Solution |
A rights management system was selected for the product development. It was determined that the file store would be on a public cloud service that would allow project team members to share documents with external project team members. This requires all external team members to be provisioned into the corporate identity access environment and added to the appropriate AD groups. A self-service tool will be deployed on the corporate website for authorized users to request changes to their access rights. would allow project team members to share documents with external project team members. This requires all external team members to be provisioned into the corporate identity access environment and added to the appropriate AD groups. A self-service tool will be deployed on the corporate website for authorized users to request changes to their access rights. A classification tool is also required that continually monitors documents and file stores. An assisted classification scheme has been selected whereby the tool recommends a classification category for newly created or modified documents. An email solution that ensures restrictions are placed on email sent within, and external to, the project team is part of the solution. A data-loss protection product that monitors for unusual behavior, such as out-of-pattern document access, out-of-hours access, and abnormal quantity access, is also part of the solution. In some cases, it will be configured to embargo a document activity pending review by a security authority; in some cases, it will issue a notification for analysis. In addition, a secure project repository for project archives is included. Cloud storage is to be used for the document store, and enrollment in the appropriate AD group is required to obtain access to the archive file share. |
Q & A
Q. With the accelerating rate of change occurring in technology (e.g., cloud service, BYOD, IoT), is it not inevitable that data loss will occur and that only cursory protection therefore needs to be provided?
A. No. Although the task of protecting data is becoming more complex, solutions are becoming increasingly more powerful. An important aspect of security is to not reach a state of inevitability that precludes a well-thought-out strategy from being developed. A strategic approach will accommodate the risks that are important to mitigate and will identify those issues that are going to happen. Only then is it possible to craft a secure information-sharing approach that is optimized for the specific situation in which an organization operates.
To deploy a DLP network edge device without considering the organization’s full requirements, or deploying a rights management solution without a change management initiative to modify the security culture within the company, should be avoided.
Q. PKI is often discounted because it is too costly and is considered “overkill” for most companies. Is there any point in considering PKI for an information security application?
A. While many organizations have decided against deploying PKI for cost reasons, that is no reason to discount its use. Anecdotal evidence suggests that in some cases, PKI deployments do not proceed because of adverse advice from legal counsel that fails to take a risk-management approach to deployment options. Such advice only considers high-security, and therefore costly, deployment options rather than accepting a solution that is eminently satisfactory for an organization.
On the IT side, the complexity and cost of key management has been known to “kill” a PKI deployment. Rather than craft a solution to accommodate the specific requirements of the business, IT managers have been known to put key management in the “too hard” basket, thereby losing the benefit of a mature and effective technology.
PKI is a bona fide technology and well suits the document security task. It provides a level of user management that other technologies cannot approach. It should be included in the list of technologies to be considered when forming a secure information-sharing strategy.
Q. Our network operations staff have selected an edge DLP device that monitors documents leaving the organization’s network. Isn’t this sufficient?
A. Maybe. It’s hard to know until a strategic review of the organization’s requirement has been conducted and the options evaluated. A DLP device at an exfiltration point can be very beneficial in identifying documents and files being sent externally to the company’s network. These devices employ content filtering looking for matches to keywords and templates that suggest a specific classification level. For instance, if “Project Hyperion” has been deemed “restricted,” when a document with the word “Hyperion” is identified by the DLP device in a file transfer or as an email attachment, the device can either let the action finish but send a notification to security, quarantine the document until it is manually investigated and either permitted or denied, or embargo the document and prohibit the transfer.
The main issue is the manual effort, and associated cost, of managing such an environment. If a rights management system is employed, such DLP devices become less of a benefit, and costs might be reduced by de-commissioning the device or only using it to flag those abuses that are considered major.
Want to learn more now? Buy Graham's book today at the MC Press Bookstore.



















 More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment.
More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment. TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now.
TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now. Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works.
Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works. Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include:
Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include: Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online