The astute reader will have noted that secure data sharing is actually part of an organization’s approach to data loss prevention (DLP). Read Part 1 here.
Editor’s note: This chapter is excerpted from chapter 9 of Identity Management: A Business Perspective.
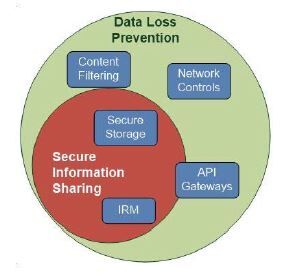
Data Loss Prevention
Unfortunately, the term DLP has been hijacked by networking types and typically refers to network edge devices that monitor data leaving an organization’s network and stop any file or document that contains data deemed to be sensitive. Content filtering is an increasingly popular technology whereby real-time monitoring of data leaving the network seeks to identify potential exfiltration of protected information. API gateways seek to manage the network edge by controlling the communication to controlled files. This means that users will be required
Figure 9.2: Data loss prevention
For instance, if a policy is established that any file containing a credit card number is embargoed and must not be sent outside the company network, DLP infrastructure will stop any documents with identifiable credit card detail. While this is commendable, and there are bona fide reasons for DLP installations to block such detail, there are a few problems. What if the file is being sent to your acquiring bank to process a transaction? The file will be stopped. Hopefully a notification will be generated, but then a manual process will need to be invoked to release the file.
Or what if a policy is established that prohibits documents on a sensitive project to be sent outside the company? Team members who want to send a file to an external lawyer for a legal review will have to manually intervene, or find another way to get the file to the lawyer. File encryption is also a problem. If a sensitive file is encrypted, the network device, which depends on content inspection, will not be able to detect that sensitive information is potentially leaving the organization.
Other DLP methods for securing data include firewalls and other network-level devices, and API gateways that can provide very sophisticated communication controls, even to the point of supporting policies that determine the attributes of users with specific access entitlements.
Strategic Approach
As with most pieces of the IT puzzle, a strategic approach is recommended. This will avoid the deployment of point solutions that, while solving one pain point, do not neatly fit under the IT strategic management umbrella. Deployment of secure sharing technology should be part of an organization’s DLP solution, which in turn is part of the IT governance framework.
Another component of the strategy is a change management program to develop a security culture within the organization. Security necessarily limits access to files and documents. Although, in a perfect world no one should need to access a document to which they have been denied access, in reality it will be necessary for staff to request access to a protected document from time to time. When this happens, it should be in the full knowledge that this is to be expected and should not be accompanied by a resentful comment about “those guys in IT.” In fact, invoking a document/file classification mechanism to heighten staff appreciation for information protection is generally a good idea.
Principles
In developing secure information sharing, it is important that a governance approach is adopted to ensure consistency across the organization, or at least across business units within the organization.
- Under the “least rights” principle, staff are only given access to the least amount of sensitive documentation that is required for them to perform their jobs. Many organizations don’t do this. For example, when a new staff member joins the organization, they are given access to the same systems and file shares as someone else in their work unit. If that person has at some time been given elevated privileges, which were not revoked, the new staff member will receive the same elevated Identity management systems these days all include approval workflows. Staff should be provisioned independently, and access rights should be approved appropriately for each new staff member.
- A classification approach should be mandated that will either allow users the freedom to classify their own documents or force machine classification. In the former, the system can “suggest” a classification based on content inspection for keywords in the document or file, or it can automatically classify. Some form of machine classification is typically required at commencement of the deployment of a secure information-sharing environment because existing documents will need to be classified.
A Data-Centric Approach
A useful methodology when selecting a secure data sharing solution is to consider the requirements of the company as data is used within the organization.
Data at Rest
Protecting data at rest is most appropriate for organizations that have repositories of protected information, such as documents pertaining to the company’s intellectual property (e.g., product development plan and business strategy documents). These files will typically be encrypted, so management of keys will be important. Such protected repositories will often sit behind network firewalls; if this is the case, access through the firewall should be based on a user’s identity attributes. Users with access rights should have the decryption keys to allow them to read the documents. The cloud has complicated this scenario with the need to secure data at rest even if it is stored in the cloud repository. The identity store is critical for these access control requirements since an identity provider service will typically supply a SAML assertion to guide the cloud-based access control decision (see chapter 4 for more information).
Data in Motion
A secure data repository is not much use if the data is decrypted and then transmitted in clear text between the server and the client device. A comprehensive secure information-sharing environment will ensure that an appropriate method of secure communication is in place. This might be as simple as using an SSL connection for HTTP sessions, or it might be as complex as deploying virtual private networks (VPNs) for any external access to sensitive data.
The classic solution is to use SSL, which means the use of encryption keys (which need to be managed) for the sender who encrypts the message and the receiver who decrypts the message.
Other solutions include the use of rights management, in which case there may be no need to encrypt files because IRM will provide the necessary protection, or encrypted files from the data repository, again obviating the need for SSL. If a file is only decrypted by keys on the user’s PC, there’s no need for SSL because the transmitted file will already be encrypted.
Data in Use
Analysis of how application data is used by endpoint clients will identify situations in which the organization is being unnecessary exposed to risk. There are basically two ways to manage control over files in use: IRM can be used, which will control what a user can do with the file to which they are provided access, or a special client can be used that manages the permissions of document recipients. If the receiver is given read-only rights to a document, that’s all they will be able to do with it. If access to applications is coming from mobile devices, external to the organization, organizations should be concerned that sensitive data is being displayed in situations that might compromise security. A possible solution is to deploy a risk management score when granting access to a protected resource. Access from an external mobile device outside of business hours would be scored differently from an access request from within a corporate network during business hours.
For access by a mobile device, there are a number of ways to improve the security level of access to corporate resources. Developing a native app that can incorporate an authentication mechanism such as OpenID connect with OAuth tokens can positively identify the device or user. Two-factor authentication, using the device as “something they have,” can readily be implemented, too.
Next time: Classification. Want to learn more now? Buy Graham's book today at the MC Press Bookstore.















 Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online