Do you really know that your security is what it should and could be?
Editor's Note: This article is an excerpt from the white paper "The State of System i (AS/400) Security," which can be downloaded free from the MC White Paper Center.
How good is the security on your IBM i (System i, iSeries, AS/400)? Are you confident about the controls you have put in place? Can you demonstrate that you're compliant with regulatory requirements that affect your industry? Do you know whether your system is better secured than the average System i?
This article is intended to give you a sense of what the most common security vulnerabilities are and provide you with a method of measuring your security settings against other System i installations.
In 2004, PowerTech launched the first "State of the iSeries Security" study, and for the last five years, we have been the only organization that studies i5/OS and OS/400 security and reports on it for the marketplace. Now in its fifth year, the renamed State of System i Security study has become the preeminent gauge used to measure the health of security on the IBM midrange platform.
And for good reason too. Every year, PowerTech samples approximately 200 systems and includes the results in the study. These systems are located all over the world and represent both large and small businesses in every industry sector. The purpose of the study is to track the progression of security on the System i and spot both common vulnerabilities as well as trends in security.
Executives, IT managers, auditors, and many others find the study to be an invaluable tool when evaluating their own security configurations. The study helps to focus attention on common mistakes that not only are found in many organizations, but also are most likely to be exploited because of their ubiquity.
I'll provide some examples of common vulnerabilities from the study in just a moment, but first let's look at some baseline numbers. In the 2008 study, PowerTech reviewed 217 systems located in 200 companies. The average system had 751 user profiles on it and 370 distinct libraries. Please keep these numbers in mind because they will help frame the scope of the problems as we review the study data.
Powerful Users
The first area the study looks at is how many powerful users exist on a given System i. A powerful user can be defined many ways, but for simplicity we will narrow the definition down to just users who have one or more OS/400 special authorities, paying special attention to the *ALLOBJ special authority because it is so powerful. In the 2008 study, the average number of user profiles with *ALLOBJ authority was 67, or 9 percent (see Figure 1). That is an extraordinarily high number of security officers!
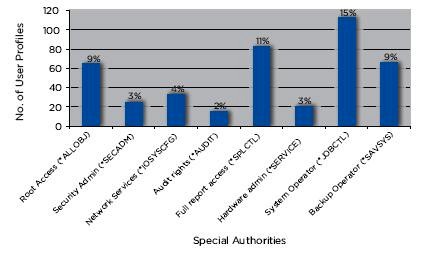
What is further disconcerting is that when we ask people how many security officers they have on their system, we typically receive answers such as "four" or "seven" or other responses indicating that the system administrator thinks the number is in the single digits. But in fact, of the 217 systems that we evaluated, only seven systems had fewer than 10 users with *ALLOBJ. Study data shows us that there is a serious disconnect between the number of *ALLOBJ users that system administrators think they have and the operating system report.
Who's Minding the Store?
Another area of deep concern is the ability to audit security events on the System i. Here the news is much better. Seven in 10 of the systems in the study had the native IBM security auditing capability (QAUDJRN) turned on as it should be. But the flip side of that number is quite disconcerting. Thirty percent of the systems in this year's study do not have the ability to detect security breaches and cannot report on inappropriate activity simply because they have not enabled this free tool that comes with the operating system! (See Figure 2.)
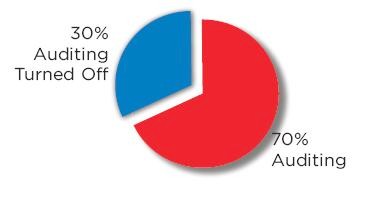
Shops that do not have the operating system's security audit journal turned on will not be able to do any kind of forensic investigation in the event of a security breach because they won't have the data available; in fact, because the security event data is not available, many times they won't even know that a breach happened. You can't claim you've never been hacked if you don't have a method of detecting attacks.
Protecting the Data
On every computer system, it is the data that carries all of the value. Protecting the data is the most important of all security tasks. Unfortunately, when we look at the average System i, we see a disturbing trend: the data is not well-protected at all. Figure 3 details the library-level security on the average machine, and it's not pretty.
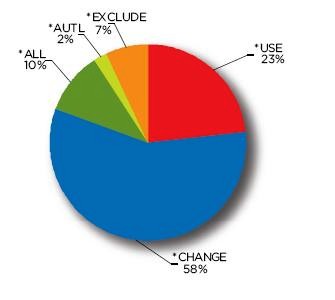
Remember that in this study the average system had 370 libraries. The figure above shows that 10 percent (37) of those libraries allow *PUBLIC to have *ALL (read, change, and delete) access, and 58 percent (215) of libraries allow every user to read or change. There are many reasons that i5/OS library security is so loose, and most of those reasons trace back to the software's original authors, but the fact remains that on the average system, every user will have change rights over two-thirds of the libraries.
In traditional AS/400 shops, this wide-open access to data was not considered a problem because users were locked into menu systems that controlled users' access. But this is not your father's AS/400, and users now have remote access capabilities via network interfaces such as FTP, ODBC, Remote Command, and many others. If you couple the availability of network data transfer tools with the wide-open authorization schemes, the potential for disaster looms large.
To counter this risk, an increasing number of organizations have deployed exit programs. Exit programs monitor network services such as FTP and ODBC and can be tuned to prevent inappropriate access to under-secured data. Figure 4 from the study shows that just under 20 percent of systems measured this year have put these protections in place.
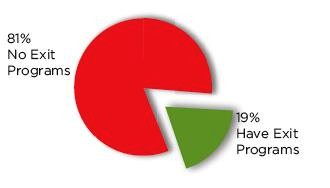
The result is that too many people in the average shop have too much access to too much data, and system administration does not have the tools to monitor or stop that access.
These are just a few of the findings in the fifth annual State of Sytem i Security study. There is much more that is interesting and informative, and I encourage you to download the white paper "The State of System i (AS/400) Security" from the MC Press White Paper Center and review it for yourself.
And if you want to know how your system stacks up against the averages, you can download our Compliance Assessment tool at www.powertech.com. This tool runs in about 5 to10 minutes and provides immediate results that you can compare to the 2008 study to see how well your system is secured. You also have the option of participating in the 2009 study by choosing to anonymously share your data with PowerTech for purposes of inclusion in the study.
My last piece of advice comes from a seasoned IT auditor. He told me that you can't just assume you are secure; you have to actually prove it. Take a few minutes to download and run the Compliance Assessment tool right now and find out where your security strengths and weaknesses are.
To find out more about the previous studies, download the white paper "The State of System i (AS/400) Security" free from the MC White Paper Center.


















 More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment.
More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment. TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now.
TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now. Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works.
Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works. Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include:
Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include: Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online