When the Internet first blossomed from an academic exercise into a commercial enterprise, companies used it primarily to promote their images, products, and services through TCP/IP access to their Web sites. Today, the focus has shifted to e-business. Companies are leveraging the global reach of the Internet and its easy and inexpensive access to extend their private networks cost-effectively. By using the Internet for intracompany and intercompany communications, you can save on communication costs and also outsource network management and operations to an ISP. In this environment, security becomes a prime concern, and that’s where virtual private networks (VPNs) come in. The Internet may make connections inexpensive, but VPNs make them more secure.
VPNs: OS/400’s Stealth Technology
A VPN is the extension of a company’s private intranet across a public network infrastructure such as the Internet. It is based on creating virtual secure tunnels between hosts connected to the public network. To participate in a secure tunnel or VPN connection, VPN partners (tunnel endpoints) must implement a compatible suite of VPN protocols.
Since IBM introduced the AS/400e series in August 1997 with V4R1, the company’s focus on e-business has led to continual enhancements of OS/400’s Internet security infrastructure. These enhancements include Secure Sockets Layer (SSL) support, the Digital Certificate Manager (DCM), native IP filtering, Network Address Translation (NAT), OS/400 SOCKS client support, and proxy server support on the IBM HTTP Server for AS/400.
IBM introduced VPN support on Version 4 Release 3 of its Firewall for AS/400 product (5769-FW1). (For a description of the VPN implementation on this product, see the Redbook IBM Firewall for AS/400 V4R3: VPN and NAT Support.) With V4R4, IBM added native VPN support to OS/400. The industry-standard IP Security (IPSec) protocols on which the VPN implementations for Firewall for AS/400 and OS/400 are based have rapidly evolved over the last couple of years. (See “Technology Spotlight: IP Security Protocol Today and Tomorrow,” D. Ellis Green, MC, September 1998.) IBM Firewall for AS/400 implements an older version of these protocols, and for this reason, the VPN implementations for Firewall for AS/400 and OS/400 V4R4 do not interoperate. Later in
this article, I discuss scenarios in which both VPN implementations can complement each other.
With V4R4, It’s Virtual but Real
IBM makes native VPN support available to AS/400 customers in V4R4 at no extra charge. However, you must have the following software installed on your AS/400 to be able to configure an OS/400 VPN:
• OS/400 V4R4 (5769-SS1)
• DCM (5769-SS1, option 34)
• AS/400 Client Access Express for Windows (5769-XE1)
• Cryptographic Access Provider (5769-AC2 or 5769-AC3). Note: Cryptographic Access Provider comes in three versions:
• 5769-AC1 (40-bit encryption, exportable, not supported by VPN)
• 5769-AC2 (56-bit encryption, exportable)
• 5769-AC3 (128-bit encryption, available in the United States and Canada)
You must order this product, as it doesn’t automatically ship with V4R4. OS/400 implements the latest versions of the IPSec protocols (AH, ESP, and IKE—for more information, see the Internet Engineering Task Force IP Security Protocol Web page at www.ietf.org/ids.by.wg/ipsec.html) and supports authentication through preshared keys. OS/400 VPN also supports the manual tunnels that you need to configure if the remote VPN partner doesn’t support IKE. In addition, OS/400 supports the Layer 2 Tunneling Protocol (L2TP). You use L2TP primarily (but not exclusively) in remote-access scenarios to extend corporate network address space over the Internet to remote dial-in clients. L2TP tunnels Point-to-Point Protocol (PPP) traffic and can be considered a successor to the Point-to-Point Tunneling Protocol (PPTP) and Layer 2 Forwarding (L2F). To achieve robust security, L2TP must be used in combination with IPSec. The Point-to- Point Connection Profiles configuration GUI in Operations Navigator (OpsNav) has been enhanced to include L2TP. (See Shannon O’Donnell’s “Get to the Point with PPP” in this issue of MC for a hands-on tutorial.)
Configuring VPN on Your AS/400
After you configure a VPN connection, you must configure IP Packet Security (IP filtering) on your AS/400, which is configured separately through an option under the Network node in OpsNav. You can accomplish OS/400 VPN configuration through the AS/400 OpsNav VPN configuration GUI. OpsNav includes a new VPN Connection Wizard that guides you through a simple step-by-step process for configuring a connection. Figure 1 shows all the OpsNav mouse clicks you need to perform to get started using the VPN Connection wizard. Inside the wizard, you input minimal information about your VPN environment, and the wizard performs the complex VPN configuration tasks for you.
The International Computer Security Association (ICSA) has certified OS/400 VPN support. Products that become ICSA-certified have met a definably quantitative level of risk reduction against a known set of threats. The ICSA IPSec certification is primarily focused on testing compliance with the specifications, which also implies interoperability with other compliant solutions (For more information about ICSA certification, visit www.icsa.net.)
Taking Control of the Internet
Let’s explore scenarios in which VPNs are used, including those that may be more attractive to AS/400 customers. As Figure 2 shows, VPNs are a convenient and more secure way to communicate with your branch offices, business partners, and remote users over the Internet. AS/400 VPN implementation supports all these environments.
Remote Access VPNs
For remote access, VPNs provide an alternative to traditional dial-up access for connecting telecommuters or traveling employees. Remote-access VPNs reduce communication costs: Remote users merely dial into the local ISP, providing significant savings compared to the cost of long-distance calls or toll-free numbers. VPNs also reduce the cost of managing and operating remote-access equipment.
The AS/400 supports remote-access VPN scenarios with dynamic IP users. The ISP randomly assigns IP addresses to remote dial-in clients. AS/400 VPN configuration includes two options to support the remote dial-in clients scenario. Use the Host to Dynamic IP Users option in Figure 1 if the remote clients will access only this AS/400 system through the VPN. Use the Gateway to Dynamic IP Users option (see Figure 1) if this AS/400 is acting as a gateway between the remote client on the Internet and other hosts in the internal network. In addition, if you want to extend your corporate IP address space to your remote clients by assigning internal IP addresses to them to make the clients appear as if they were directly connected to the internal network, you can use the AS/400’s L2TP support in the role of an L2TP Network Server (LNS).
The PC Windows clients in a remote-access VPN environment must support IPSec and, optionally, L2TP. Currently, some commercial VPN Windows clients, such as SafeNet/Soft-PK by IRE (www.ire.com/products/vpn/soft_pk.htm), support IPSec protocols. Other Windows products, such as WinVPN Client by Wind River Systems (www.wrs.com/ivasion/html/vpnclient_overview.html), support L2TP in combination with IPSec.
If the ISP provides L2TP Access Concentrator (LAC) services, the client does need not support for L2TP. However, very few ISPs provide LAC services at the present time. Check with your ISP for LAC service availability.
It’s important to note that the Microsoft VPN Adapter, which is part of Microsoft’s Dial-Up Networking (DUN) 1.3 protocol, supports only PPTP. DUN 1.3 can be installed on Windows 95 and comes standard on Windows 98 and NT, but it is not compatible with the AS/400 L2TP and IPSec implementations. Therefore, you need to install a compatible VPN Windows client, such as the aforementioned SafeNet/Soft-PK or WinVPN Client.
Branch Office VPNs
You can also use a VPN to connect branch offices and remote sites. Although it is unlikely that companies will replace existing private connections to remote offices with VPNs in the short term, a VPN could enable you to extend secure connectivity over the Internet to remote sites that would otherwise be too costly to connect to. A VPN is also a good choice if you are replacing remote controllers with AS/400 LANs.
Use a gateway-to-gateway VPN to connect two networks that belong to the same company. In a gateway-to-gateway VPN, the secure tunnel is established between the two gateway systems. Other hosts in the networks use the tunnel, but they don’t need to support VPN functions. Data flows in the clear in internal networks behind the gateways, but this is acceptable in a branch office scenario where the partners fully trust each other.
The L2TP protocol can be used in this environment in combination with IPSec if you need to extend your corporate address space to the remote branch office. (For details on these protocols, see “Technology Spotlight: Technology Standards: Who Makes the Rules?” D. Ellis Green, MC, February 1999.) You can configure your AS/400 at the central site as an LNS and configure the AS/400 at the remote site as the L2TP initiator.
The LNS can assign internal IP addresses to the L2TP initiator, making the remote L2TP initiator appear as if it were directly attached to the corporate network.
You have a few alternatives for implementing this site-to-site VPN scenario by using AS/400 VPN support:
• Use IBM Firewall for AS/400 as a VPN gateway. IBM Firewall for AS/400 has been able to serve as a VPN server since V4R3. If both of the sites you want to connect have Firewall for AS/400 installed, you can establish a secure tunnel between them. But watch out for interoperability issues. Firewall for AS/400 was one of the first IBM VPN implementations, and since its introduction, IPSec standards have evolved, making the Firewall for AS/400 VPN incompatible with newer implementations, such as the OS/400 VPN.
• Use OS/400 as a VPN gateway protected by a firewall. You can use your V4R4 AS/400 system as a VPN server behind a firewall (for example, Firewall for AS/400). This solves the potential interoperability problems mentioned previously. However, you must configure the firewall to allow the IPSec protocols IKE, AH, and ESP to flow through it. Since V4R3, Firewall for AS/400 filters have been able to be configured to permit these protocols.
• Use OS/400 as a VPN gateway within your private intranet to protect the traffic between two subnets that have high confidentiality requirements.
Business-to-Business VPNs
A VPN provides an excellent solution to connect business partners and suppliers securely anywhere in the world over the Internet. In this scenario, however, the partners don’t fully trust each other. Host-to-host VPNs help to ensure that secure traffic starts and ends on the intended partner’s host, and traffic doesn’t flow in the clear in the partner’s network. Often, this scenario is implemented as nested (iterated) tunnels: a gateway-to-gateway tunnel using AH for authentication between the firewalls that protect access to both partners’ networks and, inside it, a host-to-host tunnel between the specific hosts (as shown in Figure 2). Usually, the gateway-to-gateway tunnel provides authentication while the host-to-host tunnel provides end-to-end authentication, encryption, integrity, and replay protection. Unlike the branch office scenario, in which it is acceptable for the data to flow in the clear in the remote partner’s network (because both partners belong to the same company), the partners in a business-to-business scenario don’t trust each other’s networks. They want to have their traffic protected right to the data endpoint of the VPN connection.
You can also limit the applications allowed in the secure tunnel. For example, you can configure the VPN to allow Telnet from A to B only; no other TCP/IP application, such as FTP, could use the tunnel. Even B could not Telnet to A. You can configure your AS/400 system to be a host in a host-to-host or host-to-gateway VPN, which is very suitable for an extranet environment.
VPN vs. SSL
SSL provides authentication, integrity, and encryption. It is implemented in the transport layer (TCP/User Datagram Packet [UDP]) and requires modification of the applications that use it. Only those TCP/IP server and client applications that are SSL-enabled can use this protocol. For example, AS/400 Telnet server was enhanced to support SSL in V4R4. Services that are not SSL-enabled include FTP, Simple Mail Transfer Protocol (SMTP), POP3, and so on.
In contrast, secure tunneling protocols, such as IPSec (on which AS/400 VPN support is based), are implemented in the network layer (IP) of the TCP/IP stack. Network-layer security protocols provide blanket protection for upper-layer applications
without requiring modification of the applications that use the secure tunnel. Once a host supports IPSec, all TCP/IP applications are protected without any changes to the application. This provides the virtual network view of the interconnected VPN hosts. You can securely use FTP in a VPN between two AS/400 systems, but you cannot protect FTP with SSL because neither the FTP server nor the FTP client are SSL-enabled in V4R4.
It is important to note that both server and client must be SSL-enabled to participate in an SSL session. For example, in OS/400 V4R4, the Telnet server is SSL-enabled, but the Telnet client is not. Therefore, you cannot use a Telnet green-screen session to access the Telnet server running over SSL; you need to use an SSL-enabled 5250 emulator, such as PC5250, from Client Access/400 Express. However, if you configure a VPN between two AS/400 systems, you can securely use all available TCP/IP clients and servers, such as Telnet and FTP. To participate in a VPN connection, either the host or the intervening security gateway must support compatible VPN protocols.
SSL offers more granularity for authentication, which is provided for each application independently of the other applications. SSL authenticates users based on a client digital certificate, while VPN authenticates hosts. (Note: The application must support client authentication to authenticate users with SSL.) It is also easier to turn SSL on and off as needed to save on the performance costs of encryption.
On the AS/400, SSL performs better than VPN in V4R4, but you can expect significant performance improvements in the next release of VPN. (For more information about SSL and VPN performance, refer to the IBM manual AS/400 Performance Capabilities Reference—Version 4, Release 4 (SC41-0607-02).
Extending the Power of the Internet to Your Private Network
In combination with VPNs, the Internet enables you to provide a more secure, low-cost electronic network for your company. IPSec protocols help to defend your traffic from hackers by providing the following: data origin authentication so that a hacker cannot pose as a valid partner; data integrity so that the data cannot be altered in transit; confidentiality so that if hackers sniff your connection, the encrypted data will be meaningless to them; and replay protection so that a hacker can’t hijack valid datagrams and resend them to you to fool you or get additional information to break the key. I have described the VPN support available on the AS/400 and shown you some typical scenarios that you can implement in your organization. (For more information on AS/400 VPN support and step- by-step configuration examples, refer to the Redbook AS/400 Internet Security: Implementing AS/400 VPNs.)
REFERENCES AND RELATED MATERIALS
• AS/400 Internet Security: Implementing AS/400 VPNs, Redbook (SG24-5404-00)
• AS/400 Performance Capabilities Reference—Version 4, Release 4 (SC41-0607-02, CDROM AS4PPCP2)
• IBM AS/400 Information Center Web page: publib.boulder.ibm.com/pubs/html/ as400/v4r4/ic2924/info/infocent.htm. (Select Internet and Secure Networks/ Virtual private networking.)
• IBM AS/400 Virtual Private Networking Web page: www.as400.ibm.com/vpn
• IBM Firewall for AS/400 V4R3: VPN and NAT Support, Redbook (SG24-5367-00)
• Internet Engineering Task Force IP Security Protocol Web page: www.ietf.org/ ids.by.wg/ipsec.html
• ”Technology Spotlight: IP Security Patrol Today and Tomorrow,” D. Ellis Green, MC, September 1998
• ”Technology Spotlight: Technology Standards: Who Makes The Rules?” D. Ellis Green, MC, February 1999
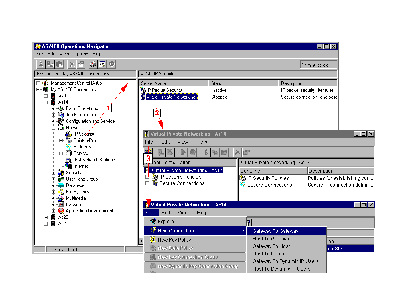
Figure 1: These are all the OpsNav mouse clicks you need to start using the VPN Connection Wizard.
Remote Access VPN Branch Office VPN
Corporate Intranet Company A Company B
VPN Client VPN Server
LNS
ISP
ISP ISP
Internet
L2TP Tunnel
IPSec Tunnel ISP ISP
Corporate Network
AS/400 VPN Server Firewall Firewall Firewall
AS/400 VPN Server Firewall
ISP
Internet Internet
Branch Office Intranet
AS/400 VPN Server
Gateway-to-Gateway VPN Gateway-to-Gateway Tunnel
Business-to-Business VPN
Host-to-Host VPN
AS/400 VPN Server
Figure 2: VPNs are a secure way to communicate with branch offices, business partners, and remote users over the Internet.





















 More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment.
More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment. TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now.
TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now. Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works.
Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works. Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include:
Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include: Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online