BackTrack is a network security project that combines two open-source software projects, WHAX and Auditor. BackTrack offers the best of both of these Knoppix-based distributions in one fully featured Slackware (SLAX) operating system, ready to install or boot directly off a CD that you carry with you. Installing the distribution means you can easily customize the utility to add your own scripts or install your own software as you see fit.
Before you get started with this utility, I offer a word of advice. Network security is a serious concern among network administrators these days. Although BackTrack serves as wonderful security testing distribution to complement your tool set, don't rely solely on this suite as a means of penetration testing your network topology. If you have serious concerns about network security in your environment, consult professionals in regard to complete penetration tests.
Download and Installation
To get started, download the ISO image from remote-exploit.org. Once it's downloaded, you can verify the image with the md5sum file and then burn to a CD. If you don't wish to install BackTrack, you can simply boot the CD from any system with at least 144 MB of memory. If you decide to install BackTrack directly to a hard drive or onto a VMware instance, a step-by-step guide with easy-to-follow instructions is located on the Web site's FAQ section .
Whether you choose the CD or installation method, you'll be presented with a login screen. The user name and password are presented to you, so type these in accordingly and you'll be logged into a root session. From there, you can access the GUI or run at the root shell. To start networking, type dhcpcd, and to start the GUI, type startx to initiate a KDE graphical session.
Inside the GUI
Once inside the GUI, you'll find yourself right at home as with any other normal Linux KDE environment. BackTrack comes standard with Internet-related applications, such as the Firefox Web browser and Gaim instant messaging programs. It also packs a few multimedia applications, such as XMMS player and the well-known K3B burning utility. These packages are all grouped under the Internet and Multimedia categories of the menu.
The Reporting Suite
The software suite that BackTrack comes equipped with can be located under the Backtrack menu. A brief breakdown of the category list under this menu is as follows: Enumeration, Scanners, Password Attacks, Spoofing, Sniffers, Wireless Tools, Blue Tooth, Cisco Tools, Database Tools, Forensic Tools, and so much more.
Many of the tools offer nothing more than pieces of information about the network you are on, which boils down to great reporting features. Some of the informational software includes tools such as snmpcheck, which will report on a host running SNMP and print out a nicely formatted list about the system and software found. This is located at Menu -> Backtrack -> Enumeration -> SNMP -> SNMP Check.
Also under this informational category, you can find tools for routing and networking, DNS, LDAP, SMB, SMTP, and WWW services on a network. There are several tools for almost every service mentioned. Basically, you can consider these tools as exploratory, but don't be fooled by simplicity; you can cough up a lot of information about a network by simply exploring a little bit with these tools.
The Security Suite
Next, we get to the fun stuff. As mentioned, BackTrack offers a lot of great tools for exploring networks, but it also offers a lot for tracking down possible security holes in your systems. You'll find many useful port scanners, such as AutoScan. AutoScan offers a very nice GUI for network discovery of hosts, network services, and ports that are open on that specific host as well. The tool is even smart enough to figure out if a host is a Windows client, a Linux server, or a printer. As you can see in Figure 1, the host that has been highlighted has open TCP ports running on SSH, and rpcbind has been identified as listening.
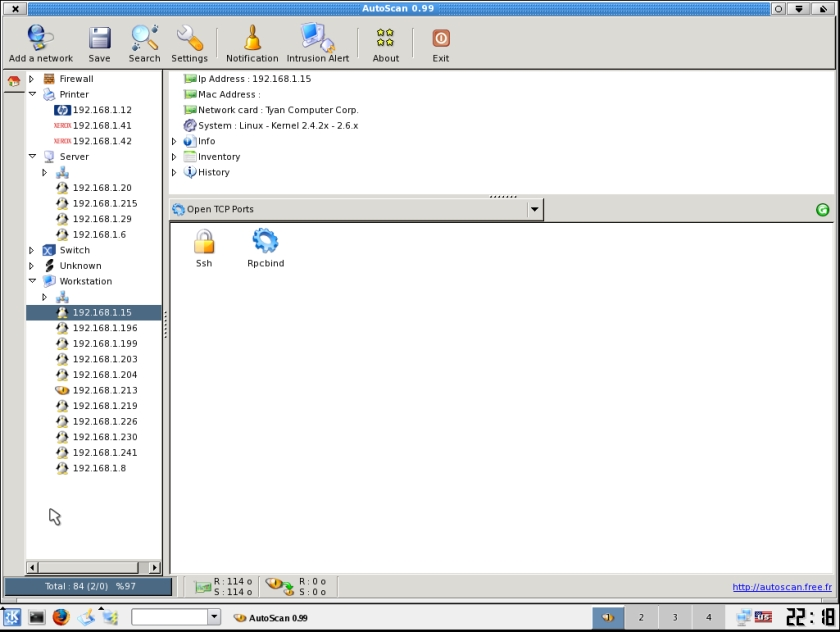
Figure 1: BackTrack will tell you what all your hosts, network services, and ports are up to. (Click image to enlarge.)
You can acquire a lot of information about a network in a short amount of time with a tool like this one. It took roughly a minute to scan and find 84 hosts and all known open ports on the network, plus locate all information from clients running SNMP. For those who prefer non-GUI tools, you'll find similar programs that run on the command line but yield the same results, such as nmap and UnicornScan.
Also under the Scanners menu, you'll find scanning tools that locate VPN and VNC connections across the network.
There's Just Too Much...
Each category under the menu system is logically split into sections. Under the Password Attacks menu, you'll find online and offline password-attacking packages such as WebCrack and the well-known password cracker named John. Under the Spoofing menu, many utilities exist for spoofing Ethernet packets or even attempting to spoof DNS names across the network. You can locate tons of programs—such as AIM Sniffer, the popular Ethereal (now known as Wireshark), Mailsnarf, and XSpy—under the Sniffer menu.
BackTrack offers many wireless tools in the form of analyzers, cracking tools, and packet forgers to investigate security concerns across wireless connections. Blue Tooth devices can be audited with tools such as PSM and RFcomm Scan under the Blue Tooth menu.
Database investigations can be completed using the many SQL injection tools covering everything from generic SQL databases to MySQL, Oracle, and MS-SQL.
Lastly, there are tools geared toward Cisco hardware, such as Cisco Exploiter, Cisco Torch, and Copy Router Config.
Investigate Away
I'll reiterate: If you have major concerns about security on your LAN, I suggest hiring a professional to perform an in-depth penetration test on your network. However, BackTrack adds a very complete set of tools in one location to perform many investigatory functions that network administrators might want to take a gander at. If you use it for nothing more than a means of reporting on remote machines, make sure to tuck BackTrack away with your other network-related software.
Max Hetrick is a PC Support Analyst/Specialist who holds a certification as an MCSA. He also has experience with installation and maintenance of Linux operating systems from the PC to server levels. Max can be reached at


















 More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment.
More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment. TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now.
TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now. Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works.
Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works. Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include:
Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include: Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online