Think of your business as residing within a Gothic fortress, the towering walls completely surrounded by a wide, entrenched moat. The only way into or out of the fortress is across a drawbridge that falls from the face of the fortress wall, extending across the moat and connecting the outer wall to the fortified guard post residing on the moat’s outer bank. Entrance to the fortress courtyard can be obtained only through a passageway tunneled through the granite walls, connecting the wiles of the outside world to the secure environment of the fortress’s inner sanctuary, and a fortified gate resides at either end. The drawbridge acts as a barrier protecting against attack, and the moat is a no-man’s-land deterring intruders from sending probes against the face of the exterior wall. In addition, access through the gates at the exterior and interior walls is governed by rules and enforced by filtering sentries.
Cyber-fortress Adventure
Your cyber-fortress adventure begins on the outer bank of the moat. Guarding the perimeter of the cyber-fortress is a fortified guard post implemented using an IBM 2210 or 2216 Nways Multiprotocol Router (www.networking.ibm.com/220/220prod.html). The perimeter between the exterior Nways Router guard post and the exterior port of the firewall is a security buffer area commonly referred to as a demilitarized zone (DMZ). The Nways Router is the first line of defense against attack; undesirable protocol traffic can be denied before ever traversing the DMZ perimeter. Access to the public FTP server, public Web server, and mail relay server can be tightened and controlled based on inbound, outbound, IP address, and port filter rules. When maintenance or redesign of either the DMZ structure or the firewall is required, the guard post can be configured so no Internet traffic is allowed to even enter the cyber-fortress DMZ perimeter.
The beauty of the AS/400 is that it functions as the cornerstone of the second tier of security within the cyber-fortress. The AS/400e’s architectural design and secure software integration allow the AS/400 to act as a dual-homed gateway firewall (www.as400.ibm.com/firewall). A dual-homed gateway firewall consists of two separate interfaces: one connected to a private, secure intranet LAN and another that functions as the single point of passage to and from the DMZ perimeter. IP forwarding is never allowed between the two interfaces. Domain Name Service (DNS) is completely split in two such that no way exists for DNS queries from the Internet to traverse the second tier of security.
A Simple Mail Transfer Protocol (SMTP) conversation is always broken at the AS/400 firewall and handled by special email code residing on the AS/400 firewall. External email hosts are not allowed to open conversations with hosts residing behind the AS/400 firewall; communication from the privately secured intranet LAN to the Internet is permitted only using either an AS/400 firewall proxy or SOCKS server.
Now the question arises as to why two tiers of security are implemented in the design of a cyber-fortress. Many techniques exist that facilitate different levels of security for an intranet LAN. A less secure model of implementing security for an intranet LAN would be simply to use a single tier, implementing just a filtering router to protect your internal secure LAN, but issues exist with this model. If an attacker successfully circumvented the filtering router, a second tier of security would not exist to prevent the attacker from attempting to probe or infiltrate production machines.
A cyber-fortress should contain two levels of security, and a DMZ should reside between the two layers. If an attack succeeds in penetrating the router acting as a filtering firewall, the intruder has gained access only to the perimeter DMZ where the public FTP and Web servers reside. The intruder would then have two options:
• The intruder could attempt to conduct probes and scans through the first-tier filter firewall, which requires opening holes in the firewall. Opening holes in the filtering router is difficult if access to the console is restricted only to administration via Telnet proxy within the second tier of security. More precisely, the console on the router has filters built so proxy communication only from the DMZ port side of the AS/400 firewall is allowed.
• The intruder could attempt to attack from either the public FTP server or the public Web server. To mount an attack against the second tier of security, the intruder may attempt to gain administration or root access to either the public FTP server or the Web server. Careful planning of system security and services on the public FTP and Web servers should be conducted to secure services provided.
The purpose of the DMZ is to provide a controlled buffer zone against possible attack. To monitor for attacks against a cyber-fortress, intrusion detection software should be used.
Confusion sometimes exists as to how DNS is handled in a dual-homed gateway firewall environment. The confusion stems from the fact that the firewall can act as an authoritative name server, but never for the internal secure LAN. The firewall can act as an authoritative name server for a DNS zone residing in the DMZ perimeter where the public FTP server and public Web server reside. If a client residing on the Internet attempts to access the public Web server residing within the DMZ, the AS/400 firewall DNS will act as the authority for name resolution within the DMZ. In a two-tier security environment, the dual-homed gateway firewall protecting the face of the second tier can provide DNS resolution for nodes residing within the DMZ.
Many times, mention is made about the firewall’s DNS. The key to understanding the AS/400’s firewall DNS design is understanding that the firewall should not answer DNS requests for DNS information residing on the private secure network. The only requests that the AS/400 firewall should answer are those made with the AS/400 firewall DNS set up to act as the authority for answering DNS queries for public FTP or Web servers residing within the DMZ perimeter. Figure 1 illustrates where DMZ host configuration is performed within the AS/400 firewall administrator.
Mail viruses have become a hot topic in the Internet community. The key to email virus protection is to scan email prior to its arrival at the internal secure LAN. In a two-tier security model, place within the DMZ a mail relay server whose sole function is simply to provide virus scanning. In addition, a mail relay server allows Internet SMTP traffic first to contact a server that actually does nothing more than act as a relay. Basically, on the Nways Router can be built a permit rule that allows only SMTP traffic inbound from the Internet to
go to the interface of the mail relay server, where the virus-scanning software resides. If an attacker attempts to gain access through SMTP port 25, the worst-case scenario would be that the attacker infiltrates a machine whose sole purpose is to scan for viruses. (You can find more information on virus-scanning software on the IBM Antivirus Online Web site at www.av.ibm.com and on the Symantec Web site at www.symantec.com/solutions.
)
Doubling Up
Recall that the Nways Router is being used as a filtering firewall and that the AS/400 firewall is being used as a dual-homed gateway firewall. Why choose two different types of firewall implementations, and why use two separate hardware and software platforms? The answer is quite simple: An attacker being familiar with two separate security platforms equally well is far less likely than if both the first security tier and the second security tier contained the same firewall hardware and software. The attacker would have to be fluent with the Nways Router, OS/400, and Windows NT/2000 as well as Linux DMZ servers hosting public Web and FTP services, the DMZ mail relay server performing virus checking, and the AS/400. This complicated setup will help to deter attack.
Traffic from the Internet through the DMZ to the AS/400 firewall occurs only in a very controlled manner. All inbound and outbound SMTP traffic is funneled through the virus-checking mail relay. An FTP of data from a user on the Internet requires a two-step process. First, the Internet client would need to place the data on the public FTP server residing within the DMZ. Second, a user on the secure internal LAN residing behind the AS/400 firewall would need to use SOCKS or proxy services to access the public FTP server residing within the DMZ. Internet users browsing public Web data have access only to the public Web server residing on the DMZ. If credit card transactions are required, Secure Sockets Layer (SSL) can be used to encrypt the connection to the public Web server.
Remember that, within the DMZ perimeter between the Nways filtering router and the AS/400 firewall, no Internet Control Message Protocol (ICMP) traffic is allowed. Only User Datagram Protocol (UDP) traffic would be allowed for the DNS, and only if the AS/400 firewall DNS were acting as the authority for the name space within the DMZ. (For more information on ICMP and DNS, see the sidebar “Protocols of the Cyber-fortress” on MC Web at www.midrangecomputing. com/mc.) Figures 1 and 2 show the DNS configuration of the AS/400 firewall. (For illustrative purposes, nonroutable IP addresses were used, but, in production, routable IP addresses would be used.)
An additional key to providing security for your internal secure LAN is to use private Internet addresses reserved by the Internet Assigned Numbers Authority (IANA) only for secure intranet LAN use. These private Class A, Class B, and Class C Internet addresses work just fine on a private intranet LAN but become nonroutable if they somehow manage to get to an Internet router. The Class A, Class B, and Class C address ranges are as follows:
• Class A—10.0.0.0 through 10.255.255.255
• Class B—172.16.0.0 through 172.31.255.255
• Class C—192.168.0.0 through 192.168.255.255
For additional information, refer to RFC 1918, “Address Allocation for Private Internets,” at www.ietf.org/rfc/rfc1918.txt.
Security Schematic
A major aspect of understanding Internet security is understanding protocols, ports, and Sockets as they relate to TCP/IP communications over the Internet. The TCP/IP
architectural model consists of four layers: the application layer, transport layer, network layer, and physical layer. SMTP, Telnet, FTP, HTTP, Lightweight Directory Access Protocol (LDAP), etc. reside within the application layer. The transport layer provides either reliable communication using TCP or unreliable communication using UDP between hosts. IP, ICMP, Address Resolution Protocol (ARP), and Reverse Address Resolution Protocol (RARP) reside at the network layer, providing routing and redirection functionality. (IP is called a connectionless protocol because it does not rely on communication from the physical layer as being reliable. Communication security over the Internet and intranets is based on controlling how the protocols are allowed to communicate within any environment.) Finally, the physical layer contains conversation at the Ethernet and Token-Ring levels. A key to intranet security is understanding that communication connections are established using Sockets. When Socket connections are controlled between hosts by denying unwanted traffic and allowing only permitted traffic, e-business can be conducted in a safe and secure manner.
A tuple is a data structure that contains terms separated by commas. A Socket consists of a three-tuple data structure: {IP address, port number, protocol}. Likewise, a connection between a local host and a remote host can be defined by a five-tuple structure: {local IP address, local port, common protocol, remote IP address, remote port}. For example, the conversation between a POP client and an SMTP server would consist of a five-tuple structure: {192.168.2.1, 4478, TCP, 192.168.100.2, 25}. In this structure,
192.168.2.1 is the IP address of the POP client, 4478 is the ephemeral port of the client, and 192.168.100.2 is the IP address of the SMTP server listening on port 25 for SMTP traffic. Remember the key: For Internet communications to occur between nodes on the Internet or on your intranet, a connection between the originating host and the destination host must be created and defined by the five-tuple association {local IP address, local port, common protocol, remote IP address, remote port}.
TCP applications communicate using well-known and ephemeral ports. Well- known ports range in value from 1 to 1023 and are assigned by the IANA. Examples of well-known ports include SMTP port 25, HTTP port 80, FTP data port 20, FTP control port 21, Telnet port 23, and DNS port 53. Typically, however, clients initiating conversations select ephemeral ports. Ephemeral ports typically reside above port 1023. Since TCP applications listen on well-known ports, filters can be established in routers and in the firewall to assist in construction of a cyber-fortress. Filters can be used either to permit or to deny specific Socket connections. (For a list of protocols and their associated ports, refer to RFC 1700, “Assigned Numbers,” at www.ietf.org/rfc/rfc1700.txt.
)
Recognizing Threats
Email bombs are typically used by attackers to fill recipients’ mailboxes or inhibit workflow. One issue with email bombs is that network bandwidth, disk storage, and CPU cycles are wasted. If an email bomb is delivered to users, a mailbox could be filled up and made inoperable, thus allowing users to experience denial of service.
A second issue concerns Spam mail. Spam mail consists of email bounced off a mail relay or firewall. If enough mail is bounced, the mail relay could potentially spend all its time redirecting Spam mail and making the system CPU unavailable for other services.
Yet another threat pertains to viruses. A virus has different ways of affecting your environment. A server either can be directly infected by a virus or may just hold infected data and pass it to a client when the client requests the data. Refer to Symantec’s Web site for information on protecting your environment from viruses.
Designing and implementing a cyber-fortress requires advanced in-house or outsourced technical skills, and intranet security is extremely important. If you’re unsure of or uneasy about implementation of a cyber-fortress, seek professional consultation.
References and Related Materials
• AS/400 Internet Security: IBM Firewall for AS/400, Redbook (SG24-2162-00)
• IBM AS/400 Security Web site: www.as400.ibm.com/tstudio/secure1/secdex.htm
• IBM SecureWay Software Services Web site: www-
4.ibm.com/software/secureway/services
• IBM Security: Trusted Solutions for e-Business Web site: www.ibm.com/security
• IBM Security Planning Web site: www.as400.ibm.com/tstudio/secure1/workshop/iprep.htm
• TCP/IP Tutorial and Technical Overview, Redbook (GG24-3376-05)
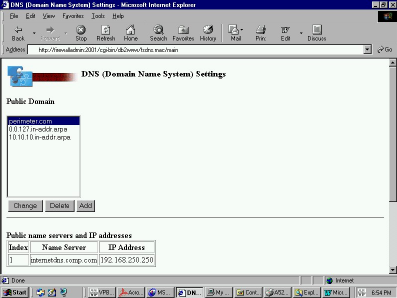
Figure 1: The AS/400 firewall administrator allows you to configure your DMZ host through a Web browser.
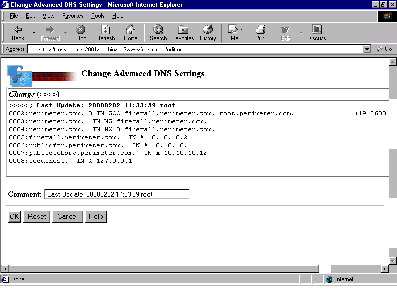
Figure 2: An AS/400 firewall allows you to modify your DNS configuration from your Web browser.


















 More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment.
More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment. TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now.
TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now. Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works.
Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works. Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include:
Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include: Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online