In previous TechTips, I presented SCS2PDF , SCS2ITEXT and AFP2PDF, three utilities that allow you to easily convert spooled files into PDF documents. Maybe you just archive these documents to replace the printed forms. But maybe you distribute them electronically and you want give your recipients a way to make sure that the document they receive actually comes from the person who claims to be the sender and that the content has not been read or altered in transit. This can be achieved with encryption and digital signature.
The Encryption
Encryption is the process of transforming plaintext into a form (known as ciphertext) that cannot be read by anyone other than the intended recipient. The document is ciphered with a key, and at arrival it can be decrypted back to the original plaintext again with the same key (called a symmetric key).
The Digital Signature
A digital signature plays two roles: authentication and non-repudiation. The first proves that you are who you claim to be and makes the recipient relatively sure that the document has not been altered after it was signed. Because this signature is attached to the document by the signer, non-repudiation prevents him from denying any responsibility at a later time. However, because anyone could pretend to be the signer with a phony self-signature, the recipient needs a way to be able to trust the signature. That's where Certification Authority (CA) comes in. With CA, a trusted third party issues a certificate containing a variety of data, including the identity of the issuing CA, how much the CA trusts the user, and an expiration date for the certificate. This certificate is used to supply a digital signature that can be verified by the recipient. To provide greater digital trust, the digital signature is packaged with the certificate of the CA, and the recipient can inspect this too for validity and expiration.
To get a certificate, you must send a certificate request to the CA. The certificate request indicates for whom the certificate is being requested, the name, the public key, and the digital signature. The CA verifies the signature with the public key in the request to ensure that the request is intact and authentic and then authenticates the owner and issues the certificate, which includes the following:
The distinguished name (DN) of the owner. A DN is a unique identifier, a fully qualified name including not only the common name (CN) of the owner, but also the owner's organization and other distinguishing information.
- The public key of the owner
- The date on which the certificate was issued
- The date on which the certificate expires
- The DN of the issuing CA
- The digital signature of the issuing CA
How to Get and Install a Certificate
If you don't already have a valid certificate, before you can use the PDFSIGN utility that accompanies this TechTip and sign your PDF document, you must create a self-certificate or get one from a CA. I will explain how to perform the second choice. However, because a real certificate costs money, you can get a test certificate, issued at no cost by a CA, with a limited validity and then keep it for an annual fee of about $200, perhaps less.
I will use two utilities for managing certificates and keys: a graphical tool called ikeyman, the IBM Key Management tool, and the standard Java command line tool, keytool.
First, you must create a keystore, a private and a public key.
In your iSeries, start Qshell (STRQSH) and type in the following code. This statement creates the keystore myKeyStore.jks in your iSeries home directory.
-dname "cn=MyCommonName, ou=myOrgUnit, o=myOrg, c=IT"
-alias myAlias -keypass myPass -keystore myKeyStore.jks
-storepass myPass -validity 180
(Of course, you would put in your real common name, organization unit, country code, and password. Use the same password for keypass and keystore, and remember that the password is case-sensitive).
Now, you have to prepare the request of the certificate:
-alias myAlias -keypass myPass -keystore myKeyStore.jks
-storepass myPass -file myCertReq.csr
Then, visit a CA. I will use a free test certificate issued by Thawte, which can be requested here. Open the myCertReq.csr you created in the previous step and copy and paste the content into the Thawte textbox. Don't forget to check the box beside PKCS #7 Format. Press Next to get the certificate that you will copy and paste into a text file in your iSeries. I called this file myCertReply.arm, but you can call it whatever you want.
Before importing the certificate, you have to add the CA's root certificate yourself to create a certificate chain. The Test CA Root Certificate is available in text format here. Copy the text data into a text file called ThawteTestCA.arm and import it into your keystore by typing the following:
-alias "Thawte Test CA Root"
-file ThawteTestCA.arm -keystore myKeyStore.jks
-storepass myPass
Now, import the certificate issued from the CA that you saved into myCertReply.arm:
-alias myAlias
-file myCertReply.arm -keystore myKeyStore.jks -trustcacerts
-storepass myPass -keypass myPass
The last step consists of exporting the certificate in a format (PKCS12) that can be used by the PDFSIGN utility. In your PC, start ikeiman, open the keystore myKeyStore.jks in your iSeries home directory, and select the certificate myalias. Export the certificate in PKCS12 format and call the exported file myCertificate.p12.
Remember that you can delete all things created so far with the following commands:
-keystore myKeyStore.jks -storepass myStorePass –alias myAlias
keytool -delete
-keystore myKeyStore.jks -storepass myStorePass –alias "thawte test ca root"
del myCertificate.p12
del ThawteTestCA.arm
del myCertReply.arm
del myCertReq.csr
del myKeyStore.jks
How to Sign a PDF
You are ready to sign your PDF. Download the PDFSIGN utility and move the PdfSigner.class into the /pdf directory that you already created for SCS2ITEXT and optimize at level 40 with the CRTJVAPGM command. Move the CMD and the CLLE into a source file and compile as usual. Note that this utility relies on the iText APIs introduced in Part 3. Paulo Soares, one of the authors of iText APIs, explains here various methods of signing a PDF.
At this point, you can sign the PDF that was included in the Part 3 download with the following command:
FROMPDF('/home/costagliol/QSYSPRT.pdf')
TOPDF('/home/costagliol/Signed.pdf')
CERTNAME('myCertificate.p12') CERTPASS('myPass')
REASON('PTF detail') LOCATION('Turin-Italy') CONTACT(
VISIBLE(*YES) IMAGE('mySignature.gif') SIGSCALE(50) SIGRECT(300 55 480 125)
Open the created Signed.pdf with Acrobat Reader. This is what you should see:
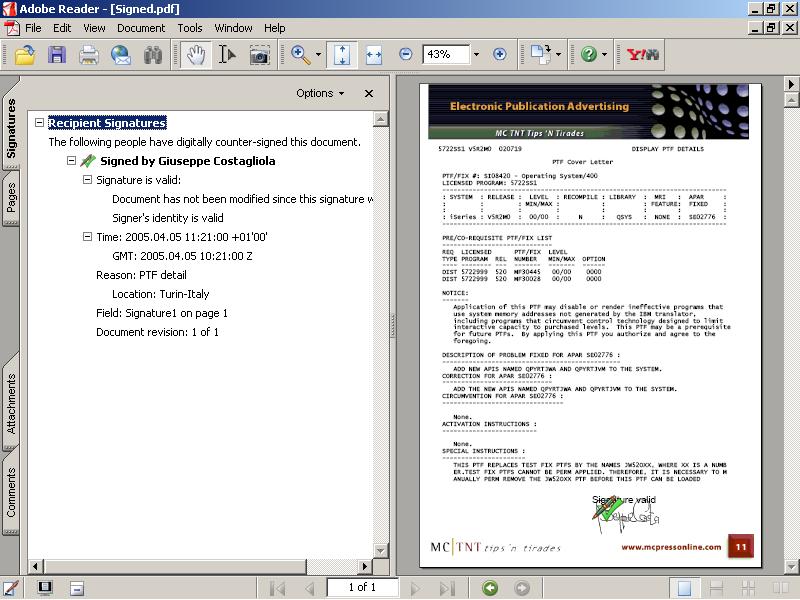
Then, click on the signature to examine the certificate.
Happy signing!
Giuseppe Costagliola is a programmer in Turin, Italy. You can reach him at


















 More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment.
More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment. TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now.
TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now. Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works.
Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works. Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include:
Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include: Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online