Authority Broker 4's new Screen Capture feature represents a Quantum Leap in user auditing!
A popular new TV crime drama called Person of Interest tells of an advanced computer that can predict crimes by monitoring the actions and conversations of New Yorkers for signs that they are planning something nefarious. Although the idea of "Big Brother" monitoring public places elicits heated debate regarding personal privacy, most of us acknowledge that monitoring user activities in the modern workplace has become a necessity.
Fortunately, IBM i contains comprehensive auditing capabilities, including the ability to record the actions of a command-line user. These events are stored in the security audit journal (QAUDJRN), a tamper-proof repository designed specifically for audit information. Activating the operating system's audit functions is straightforward (for more information, see the article "Auditing in the Real World" available for download at www.powertech.com).
Unfortunately, while the command-auditing process is easy to activate, the forensics of reporting on those actions is not. There can be hundreds of related entries in the audit journal, and these have to be identified and parsed—a task that often requires custom code to be written and maintained. In addition, there are numerous "black hole" commands, which is a term I coined for commands that place the user into an environment that itself is not easily audited. Examples of these environments include Interactive SQL, System Service Tools (SST), QShell, DFU, and even user applications. Traditionally, when even an audited user issues the command to invoke one of these environments, visibility is lost until they exit the environment and resume entering commands.
Transparency of user actions in powerful environments such as those mentioned above represents a serious vulnerability. Data could be extracted, modified, or even deleted; password traces could be started, and disk units or other critical hardware could be manipulated—all without a clear record! It's no surprise that organizations are now demanding the deployment of an audit strategy that includes the ability to report on all user actions—and PowerTech has the solution.
Authority Broker 4 represents the latest generation of an award-winning user privilege and auditing solution. In a nod to auditor demands for access to be granted on an as-needed basis only, users can be tightly restricted until authorities are elevated on-the-fly. Notifications can be sent to interested parties when an approved elevation occurs, and all subsequent actions by that user are securely logged. Unlike the command auditing that is configurable in the operating system, Authority Broker contains a powerful reporting facility that collates and isolates tasks performed by each individual user, and, more importantly, there are no "black hole" commands!
How have we addressed this serious operating system audit deficiency? When the user is operating in audited mode—which can be done with or without the user's knowledge—you now have the choice to record a "screen cam" of their session in addition to the normal command log. Upon conclusion of the audited action, the screen images are indexed into a PDF and emailed to the interested parties. Screen images are time-stamped and indicate which command or function key transitioned the user to their next screen.
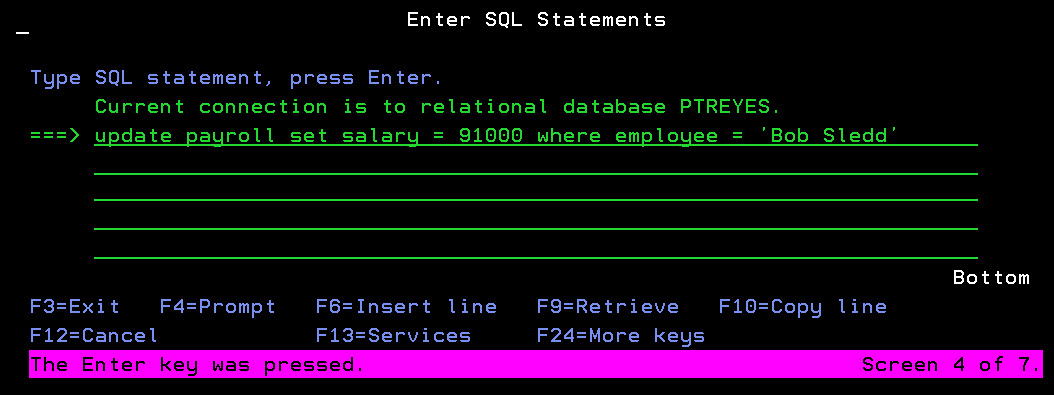
Figure 1: View user activities as they occur using an amazing LIVE VIEW mode.
Imagine the unethical programmer who accesses a production partition. You're now able to receive a bookmarked document showing every damaging UPDATE statement run through SQL, the data records that were illegally viewed in DFU, and the program modification and recompilation that was performed outside of the lifecycle management solution. You will even see movement within the application that they're supposed to be fixing. Of course, this documentation can also be used as irrefutable proof that a task was completed on time and in compliance with policy and procedures.
Authority Broker 4 with Screen Capture ushers in a new generation of user auditing. No longer will IT have to confess that they don't know what the consultant or vendor really did on the production system. Like a referee with the luxury of instant replay, audit staff can now review every move and prove it—even viewing the audited user's screen in a game-changing LIVE VIEW mode!
For more information on how Authority Broker can silently watch over your user community—or for a free 30-day trial—visit www.powertech.com.
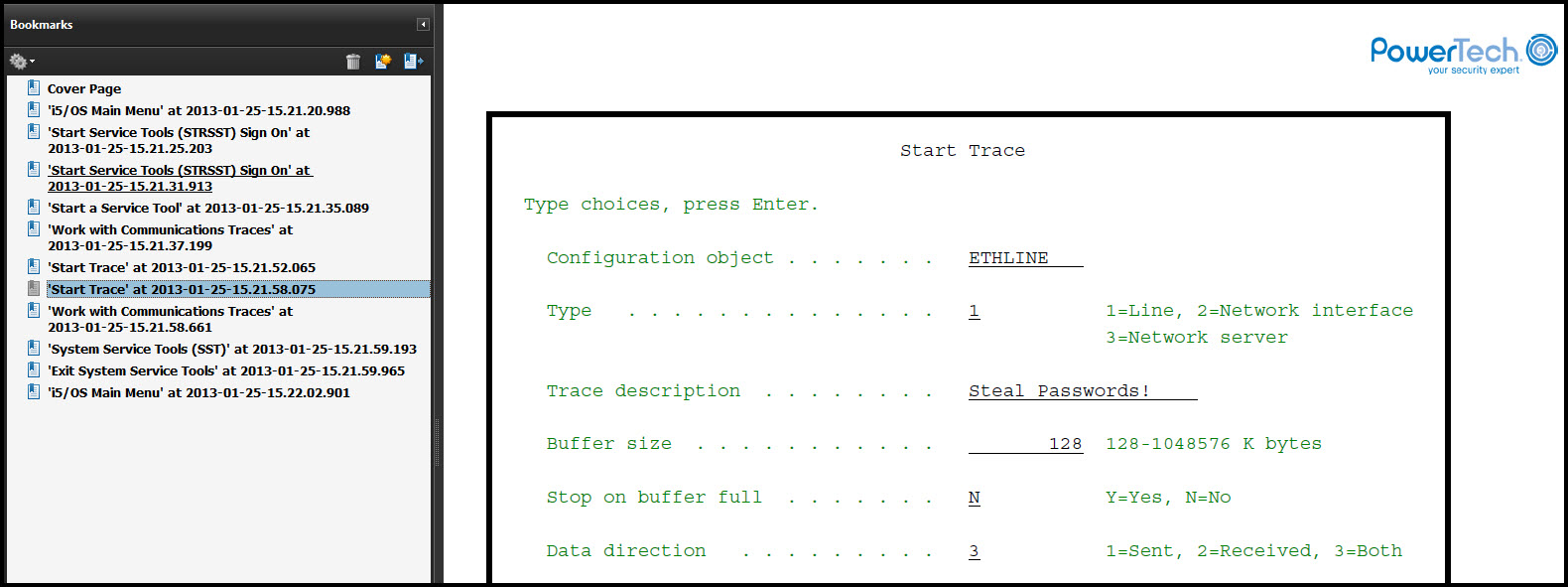
Figure 2: Authority Broker provides proof of user activity, even within "black hole" environments such as STRSST and STRSQL.












 Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online