The concept of the named constant is closely associated with the concept of a literal. Miss the introduction to using declarations? Read it here: Part 1
By Brian Meyers and Jim Buck
Editor's Note: This article is excerpted from chapter 4 of Programming in ILE RPG, Fifth Edition.
A literal is a means of noting a fixed value (e.g., a number, a character string, or a date). For example, the number 789 is a literal, as is the character string ‘September’. ILE RPG lets you associate a data name with a literal so that you can reference the literal by its name throughout your program. The resulting data item is a named constant.
Once you’ve defined a named constant, you can use it with any processing appropriate to its type. The value of a named constant is fixed. You cannot change it during the course of program execution.
Named constants let you define constants in one place near the beginning of your program rather than coding them as literals throughout your calculations. This practice is a standard of good programming because it facilitates maintenance programming. If a programmer needs to change a value, such as Taxrate, it is much easier and less error-prone to locate the named constant and change its value in that one place rather than having to search through an entire program looking for and examining the purpose of every calculation in which the literal value .0765 occurs.
Before we examine how to declare named constants, let’s dig a little deeper into literals.
Numeric Literals
A numeric literal is a number, and its value remains fixed throughout the program (unlike a variable, whose value can change throughout the program). A literal can contain a radix character or a sign, or both. If the numeric literal includes a sign, the sign must be the leftmost character of the literal. If the numeric literal does not include a sign, the computer assumes that the literal represents a positive number.
Other than a radix character and a sign, a literal can contain only the digits 0 through 9. Never use blanks, currency symbols, percent signs, or thousands separators in numeric literals, and do not enclose them in apostrophes ('). The numeric value can be as long as 63 digits, with up to 63 decimal positions. Some examples of valid numeric literals follow:
Character Literals
Often, you will want to work with character values as well with as numeric values. RPG lets you use character literals for that purpose. Character literals are character strings. Like numeric literals, character literals maintain a constant value during the execution of the program. To indicate that a value is a character literal (and not a variable name),
simply enclose it within apostrophes. No restriction applies on what characters can make up the literal. Any character that you can represent via the keyboard—including a blank— is acceptable. If the literal is to include an apostrophe character, use two apostrophes to represent it. Character literals can be up to 16,380 bytes. Some examples of character literals follow:
Tip
You cannot use a character literal enclosed in apostrophes with an arithmetic operation even if all the characters of the literal are digits. Numeric literals are not enclosed within apostrophes.
Typed Literals
In addition to numeric and character literals, you can express other data values, such as dates and times, by using typed literals. To code a typed literal, enclose the value within apostrophes and precede it with a data type code to indicate which data type the literal represents. To refer to a value of January 1, 2018, for example, you’d code D'2018-01-01' as the literal. Other common data type codes for literals are T (for times), Z (for timestamps), and X (for hexadecimal literals). Here are more examples of typed literals:
|
Data Type |
Typed Literal |
|
Date |
D’2008-03-15’ |
|
Time |
T’08.56.20’ |
|
Timestamp |
Z’2008-03-15-08.56.20.000000’ |
|
Hexadecimal |
X’F0F0F0’ |
Defining Constants
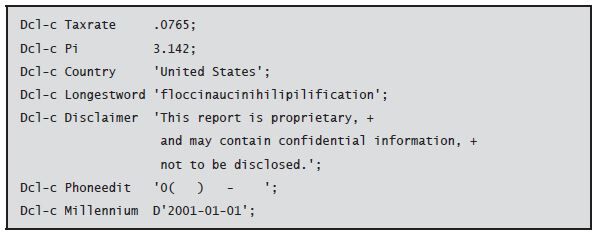
A named constant assigns a name to a literal so that you can reference the literal by its name throughout your program. The named constant’s value never changes during processing. The Dcl-c (Declare Constant) instruction defines the named constant:
The Dcl-c instruction requires only the name of the constant and its value. The constant is defined with no specific length or type; those attributes are implicit in the value. The data item name must begin with an alphabetic character or the special character $, #, or @. The remaining characters can be alphabetic characters, numbers, or any of the four special characters _, #, $, and @. A data item name cannot contain blanks embedded within the permissible characters.
You enter the literal value of the constant following the name. Enter numeric constant values with a radix character or sign if appropriate, but never with thousands separators. Enclose character constant values within apostrophes. Constants of other data types should follow the rules indicated earlier for typed literals. Here are some valid constants:
You might occasionally see the value for a named constant coded within parentheses following the Const keyword. This notation is valid but optional, and most programmers prefer simply to code the value without the Const keyword. The following two constant declarations are equivalent:
A character constant can be at most 16,380 bytes, and a numeric constant can contain up to 63 digits, with up to 63 decimal positions. To enter a named constant too long to fit on a single line, continue the value onto the next line, using a plus sign (+) to signal that the constant resumes with the first nonblank character on the next line.
Tip
Always use a named constant instead of a literal in your program, unless the use of the literal is obvious. Using named constants makes your programs much easier to read, understand, and maintain than if you use literals. For example, it’s easier to immediately understand the use of the term Taxrate than the literal .0765. It’s also easier to change the program later if the rate changes.
One exception to this rule might be the use of the literals '1' and '0', which have generally accepted meanings of *On and *Off, respectively.
Using Figurative Constants
ILE RPG includes a special set of reserved words called figurative constants, which are implied literals that can be used without a specified length. Figurative constants assume the length and decimal positions of the variables with which they are associated. Some of RPG’s figurative constants are as follows:
- *Blank (or *Blanks)
- *Zero (or *Zeros)
- *Off
- *On
- *Hival
- *Loval
- *All
- *Null
RPG lets you assign *Blank or *Blanks to cause a character variable to be filled with blanks. Assigning *Zero or *Zeros to both numeric and character variables fills the variables with 0s.
Figurative constants *Off and *On represent '0' and '1' character values. *Off is the equivalent of '0', and *On equates to '1'. Although you can use *Off and *On with any character variable of any length, programmers most often use *Off and *On to either change or compare an indicator’s value.
Assigning *Hival fills a variable with the highest possible collating value appropriate to its data type. Setting a character variable to *Hival sets all the bytes to hexadecimal FF (all bits on). For a numeric variable, *Hival is the maximum positive value allowed for the data representation, usually all 9s and a plus sign (+). Assigning *Loval fills a variable with the lowest possible collating value appropriate to its data type—for example, hexadecimal 00 (all bits off) for character variables and the minimum negative value for numeric variables. Programmers often assign *Hival or *Loval to a variable to ensure that the variable’s value is the maximum or minimum possible.
Assigning figurative constant *All immediately followed by one or more characters within apostrophes repeats the string within the apostrophes cyclically through the entire length of the result variable. For example, assigning *All'Z' to a character variable fills the variable with Zs, and assigning *All'7' to a numeric variable fills the variable with 7s.
The constant *Null represents a null value. You generally use *Null to represent the absence of any value—which is not the same as using blanks or zeros. Usually, ILE RPG uses *Null only in unusual situations, which we examine later.
Next time: Defining Standalone Variables. What to learn more now? Buy Programming in ILE RPG, Fifth Edition at the MC Press Bookstore today!





















 Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online