Security reporting should be an integral part of every organization's security strategy.
I recently spoke with a number of attendees at COMMON's fall conference in Columbus who were facing regulatory mandates including PCI, Sarbanes-Oxley, and HIPAA. For these organizations, tremendous resources are often consumed in order to generate the variety of information deemed necessary to prove compliance. Other session attendees indicated that, despite having no formal regulatory requirement, they wanted to learn more about security reporting on IBM i.
My suggestion was to start by using the GO SECTOOLS menu to run some critical reports. Beneficial information available via this menu includes profiles with default passwords and job descriptions with named users. In addition, I suggest printing and reviewing user profiles using the PRTUSRPRF command, and system values via the DSPSYSVAL command. This should be done for all partitions. Then a process should be defined to compare the current systems against an accepted baseline. Reports should then be archived for later retrieval if necessary. Unfortunately, it doesn’t take long to realize that this can quickly become a burdensome task, exacerbated by the current trend toward virtualized workloads deployed across numerous partitions. When you include reporting of the security event data that IBM i is able to record, many organizations turn to the audit experts at PowerTech to help streamline the entire audit lifecycle process.
Compliance Monitor effectively eliminates the burden of configuration and event reporting. Hundreds of report options provide visibility to static configuration elements, including user profiles and system values, as well as all 70+ event types that can be recorded into the security audit journal, QAUDJRN. Batch scheduling and distribution features eliminate the traditional burden of running, gathering, and disseminating the information to the interested parties. Global organizations can report against every instance of the operating environment—regardless of whether they run on numerous servers and partitions—as quickly and efficiently as an organization with a single partition system.
Recent enhancements in browser technology have eliminated the requirement for client software, further simplifying the highly efficient infrastructure. After installation of the host component, authorized users simply point their browser at a URL and sign in to select which systems to interrogate and which reports are desired. Even this simple step can be eliminated by initiating the desired reports using any IBM scheduler (there's also a scheduler built in to the software along with integration with Robot/SCHEDULE) and selecting to distribute the results via email as shown in Figure 1.
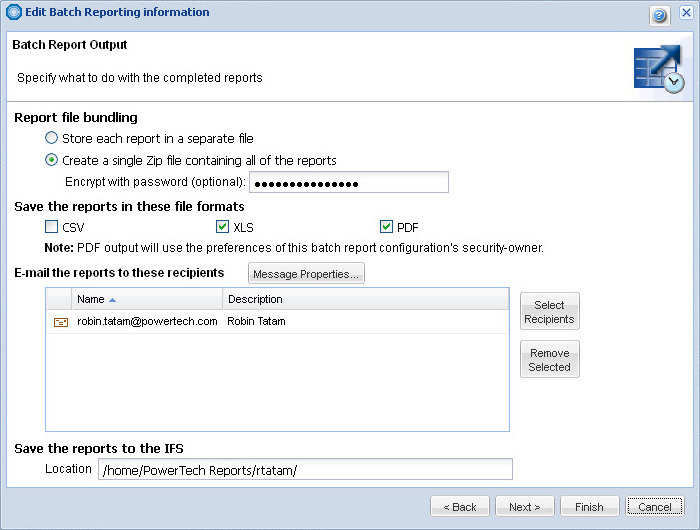
Figure 1: Compliance Monitor now includes batch scheduling and e-mail distribution of audit reports.
If SECTOOLS falls short of the flexibility, scalability, and automation that your organization demands, Compliance Monitor is the missing link—with features that include these:
- Consolidated reporting against many partitions
- Centralized storage of audit journal data, with upward of 90% compression
- Scorecard reports for executive summary of the state of compliance
- Scheduling and distribution of reports via email
One of the most powerful features of Compliance Monitor can be found within its baseline comparison. System value policies can be defined and used to rapidly determine regulatory and policy non-compliance. Filters can sequester compliant values, focusing attention exclusively on issues, regardless of the number of servers or partitions that are included in the report.
Once reports have been run, Compliance Monitor also helps with the interpretation of the findings. An integrated compliance guide provides explanations and best-practice recommendations. Alignment and mapping to common regulatory frameworks, such as COBiT and ISO, help the audit and IT community converse using a common language.
Compliance Monitor is a game-changer for organizations wishing to perform compliance or forensic reporting. Even those without formal regulatory mandates will benefit from the increased awareness of server configuration—an awareness that inevitably results in better security. Automating this important but time-consuming business function alleviates the need to manually generate, extract, consolidate, and disseminate security reports so that you can spend more time with your family this holiday season.
For more information on how Compliance Monitor can work for you—or to sign up for a free 30-day trial—visit www.powertech.com.












 Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online