In V5R3, IBM enhanced DB2 UDB implementation of SQL by adding 25 new BIFs. In Part 1 of this series, we explored new functions used for data partitioning. In Part 2, we'll explore six new data encryption functions that allow us to make our data more secure.
SQL Data Encryption
In V5R3, DB2 SQL includes a set of functions for encrypting and decrypting data. The ENCRYPT_RC2 function uses the RC2 encryption algorithm to encrypt the data supplied on its first parameter. RC2 is a widely used variable key-size block cipher encryption algorithm developed by RSA Security. The ENCRYPT_RC2 function supports two additional parameters that define a password, which is required to decrypt the data, and a hint value to assist in retrieving a lost password. A password can also be specified using the SET ENCRYPTION PASSWORD statement. The following statement is an example of using the ENCRYPT_RC2 function to insert encrypted account number values into a table.
VALUES("Doe", "John", ENCRYPT_RC2('123-45-6789', 'EAGLES', 'TALON'))
When executed, this statement will insert a row containing the encrypted value 123-45-6789 with a password of EAGLES and a hint value of TALON.
It's important to mention that the field containing the encrypted data must be large enough to support the encrypted data, the password, and the optional password hint value. This length is calculated by taking the length of the data to be encrypted, adding 8 bytes, and then rounding that number up to the closest multiple of 8. If a hint is included, you also have to add the length of the hint. In the example above, our data field is 11 bytes, and we add 8 to arrive at 19. The next multiple of 8 is 24, so we round up to 24. Since our password hint is 5 bytes, we add 5 to 24 to come up with a minimum field length of 29 bytes. Figure 1 illustrates this calculation.
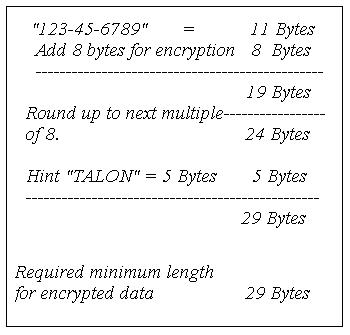
Figure 1: Calculate the field length for the encrypted data field. (Click image to enlarge.)
When data has been encrypted with the ENCRYPT_RC2 function, the field data will be unreadable unless it is decrypted using one of the following decryption functions:
- DECRYPT_BIT decrypts bit data.
- DECRYPT_BINARY decrypts binary data.
- DECRYPT_CHAR decrypts single-byte character data.
- DECRYPT_DB decrypts double-byte character data.
The first parameter for each of these functions represents the field containing the encrypted data. The second parameter contains the encryption password or the special value DEFAULT, which identifies that the password defined using SET ENCRYPTION PASSWORD statement should be used. The optional third parameter can be used with single- and double-byte character fields to define the code page. The statement below illustrates using the DECRYPT_CHAR function to decrypt the value inserted in the previous example.
FROM EMPLOYEES
When this statement is executed, the value '123456' is returned. If an invalid password is supplied to any of the DECRYPT functions, an error message is generated.
The GETHINT function retrieves the hint text for the provided encryption field. The statement below illustrates using this function.
FROM EMPLOYEES
When executed, this statement returns the hint value we defined using the ENCRYPT_RC2 statement. Using our earlier example, this returns a value of 'TALON'.
For more information about SQL BIFs, check out SQL Built-in Functions and Stored Procedures (new from MC Press).
Mike Faust is an application programmer for Fidelity Integrated Financial Solutions in Maitland, Florida. Mike is also the author of the books The iSeries and AS/400 Programmer's Guide to Cool Things, Active Server Pages Primer, and SQL Built-in Functions and Stored Procedures. You can contact Mike at
















 Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online