And Now a Word on Dependency...
Q: Would you explain functional dependency as it pertains to database design?
— Sean White
A: Functional dependency means that the value of one field can be determined from the value of another. For example, suppose a customer master file has the following fields:
• Customer number (key)
• Customer name
• Street address
• City
• State abbreviation
• State name This file has an undesirable functional dependency. State name is functionally dependent on state abbreviation. For example, any record with state abbreviation TX must have state name Texas. All other fields are functionally dependent on customer number, but that’s OK and desirable because customer number is the key.
A file is normalized when all fields are functionally dependent only on the key. To normalize this file, you should divide it into two files:
File 1:
• Customer master file
• Customer number (key)
• Customer name
• Street address
• City
• State abbreviation
File 2:
• State master file
• State abbreviation (key)
• State name
The state name is no longer stored in the customer master file but is stored in a state master file. Now, if you want to know the name of the state in which a customer lives, take
the state abbreviation in the customer master file and find the matching state abbreviation in the state master file. This process is called joining. I have given you only a brief explanation. You can use a search engine on the Web to find more information.
— Ted Holt Senior Technical Editor
Midrange Computing
Show Me What You’ve Got!
If you’re used to using Retrieve CL Source (RTVCLSRC) to retrieve the source for Original Program Model (OPM) CL programs and you’ve tried it on ILE CL modules, you’ve found that it doesn’t work for this new object type. It’s true that RTVCLSRC works only with OPM CL programs. However, you can get the source for ILE CL modules. If you have created the module with the DBGVIEW parameter value of *ALL or *LIST, you can retrieve the source by starting a debug and manually copying the lines.
— David Morris
Editor’s Note: This technique works for all ILE languages, not just CL.
Can a Leopard Change Its Spots?
Q: I used FTP to transfer a save file from one AS/400 to another, but I forgot to create the save file on the receiving AS/400 first. Now, I have a physical file. Can I convert this physical file back to a save file?
— Dale Monti
A: You cannot take the physical file and create a save file from it, but you can re-FTP the file from your PC. Use the following commands to re-create your save file without losing the data in it. Assume, for example, that you inadvertently created a physical file named DATA1 on your AS/400. It should have been a save file, but you forgot to create the save file first. To transfer the data from DATA1 into a new save file in library QGPL, do the following:
1. From an AS/400 command line, create a save file named NEWSAVF in a library (in this example, I’ll use library QGPL):
CRTSAVF QGPL/NEWSAVF
2. Now, start the FTP on the AS/400 and use the following FTP commands to move the data from your physical file (that should have been a save file) into the new save file in QGPL:
• ftp system name
• user Your User ID
• pass Your Password
• binary
• put DATA1 QGPL/NEWSAVF
• quit
— Chuck Pence
Jobs, Jobs, Everywhere Jobs!
Programmers and operators need to review the status of interactive and batch jobs daily. The commands often used for this are Work with Active Jobs (WRKACTJOB) for interactive jobs and a combination of Work with Job Queues (WRKJOBQ) and either Work
with Subsystem Jobs (WRKSBSJOB) or Work with Submitted Jobs (WRKSBMJOB) for batch jobs.
WRKACTJOB uses a great deal of resources, gives me more information and power than I usually need, and is not sequenced in a way that is useful for me. In addition, although WRKJOBQ, WRKSBSJOB, and WRKSBMJOB do give useful information, it would be more convenient just to combine the information into a single display so I could see for each subsystem which jobs are waiting to run with the jobs already activated.
Using the Work with User Jobs (WRKUSRJOB) command solves both of these problems by allowing me to display interactive jobs in a more meaningful way and, for batch jobs, combining waiting and active jobs into a single display. However, the command parameters for WRKUSRJOB can be confusing. For that reason, I have created a new command that uses WRKUSRJOB but simplifies the parameter options. I call this command Work with Users (WRKUSERS), shown in Figure 1. The command processing program (CPP) for this command is WRKUSERC (Figure 2).
WRKUSERS has just two parameters: User and Type. For User, you can specify *ALL (the default) for all users, * for the current user, or a user name. In this way, you can indicate whose jobs you want to see. Type parameter has only two options: *BATCH (the default) for batch jobs or *INTER for interactive users. When executed, the command runs WRKUSERC, which examines the value specified for Type and fills in the appropriate parameters to execute WRKUSRJOB. When *BATCH is specified, you can see all the batch jobs waiting or running for all users, the current user, or the user indicated. These jobs are grouped by subsystem, so you can see the sequence in which jobs are processed. If *INTER is keyed in, for example, you get a list of users currently logged on, sorted initially by user ID.
Once a list is displayed, look at the command keys available, and you will see options for changing the sort sequence, the information being displayed, or even the user value from what was initially requested. Be aware that, as written, I have selected the *BASIC level of information to be displayed because I like the way this option displays information. *BASIC is the most restrictive as far as user options are concerned, so you may not have the same level of job manipulation as you are accustomed to having. Consequently, you may want to try experimenting with WRKUSRJOB parameters and choose values different from those I have provided if you want a higher level of job control and are less concerned with the actual sort sequence.
I use this command many times each day to find out why one of my batch jobs hasn’t started, to see if a remote user is currently logged on, and to gather many other pieces of useful information about batch and interactive jobs. In addition, operations doesn’t complain about system response time slowing down because I no longer need to use WRKACTJOB.
Try it. I think you’ll find it as useful as I have.
— Bruce Guetzkow
/*===============================================================*/
/* To compile: */
/* */
/* CRTCMD CMD(XXX/WRKUSERS) PGM(XXX/WRKUSERC) */
/* */
/*===============================================================*/
CMD PROMPT('Work with Users')
PARM KWD(USER) TYPE(*NAME) LEN(10) DFT(*ALL) +
SPCVAL((*) (*ALL)) PROMPT('User')
PARM KWD(TYPE) TYPE(*CHAR) LEN(6) RSTD(*YES) +
DFT(*BATCH) SPCVAL((*BATCH) (*INTER)) +
PROMPT('Type')
Figure 1: Use WRKUSERS to see instantaneously what your users are doing on the system.
/**************************************************************************/
/* To Create: */
/* Crtclpgm Pgm(xxx/WrkUserc) Srcfil(xxx/Qclsrc) */
/**************************************************************************/
PGM PARM(&USER &TYPE)
DCL VAR(&USER) TYPE(*CHAR) LEN(10)
DCL VAR(&TYPE) TYPE(*CHAR) LEN(6)
/*********************************************************************/
/* When "Batch", display Batch Jobs for User Specified. */
/*********************************************************************/
IF COND(&TYPE = '*BATCH') THEN(DO)
WRKUSRJOB USER(&USER) JOBTYPE(*BATCH) ASTLVL(*BASIC)
GOTO CMDLBL(ENDPGM)
ENDDO
/*********************************************************************/
/* When "Inter", display Interactive Jobs for User Specified. */
/*********************************************************************/
IF COND(&TYPE = '*INTER') THEN(DO)
WRKUSRJOB USER(&USER) STATUS(*ACTIVE) +
JOBTYPE(*INTERACT) ASTLVL(*BASIC)
GOTO CMDLBL(ENDPGM)
ENDDO
ENDPGM: ENDPGM
Figure 2: Here’s the WRKUSERS command processing program.
Time for a Change
Q: Is there a way to change the timeout interval for FTP? Currently, when I start an FTP session, I receive a message that says my FTP session connection will end after 5 minutes. Once I have an FTP session active, is there a command that can extend or change this timeout feature?
— Mike Essig
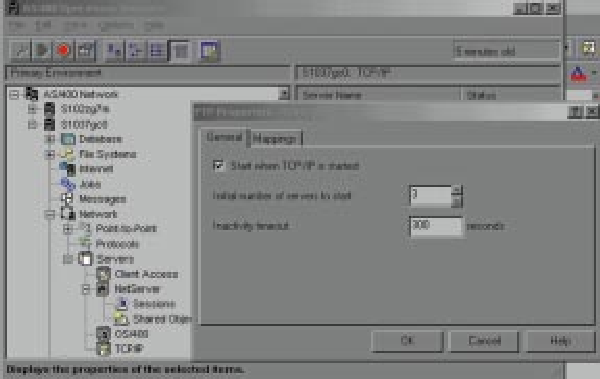
A: There are two ways to change the disconnect time interval on FTP sessions. The first way is to use the Change FTP Attributes (CHGFTPA) command. Using this command, which you can also reach by keying in the Configure TCP/IP (CFGTCP) command and option 3, you would specify, on the Inactivity Time Out (INACTTIMO) par-ameter, the number of seconds an FTP session can remain inactive before it times out. The default is 300 seconds, or 5 minutes.
Your other option is to use the Client Access/400 Operations Navigator (OpsNav). To use OpsNav, open an OpsNav session and double-click on the Network icon. Double- click on the Servers icon, and you will see an icon for TCP/IP. Right-click on this and select Explore. In the right pane, you will see all the TCP/IP servers listed. Right-click on the FTP icon and select Properties. You will see a panel like the one shown in Figure 3. Type in the number of seconds you want your FTP session to remain active and click OK. That’s all there is to it!
— Jeff Importico
— Shannon O’Donnell Associate Technical Editor
Midrange Computing
 |
implementation. I found that EDP (Electronic Data Processing) auditors prefer shops to use source compare utilities to allow an MIS supervisor to catch unauthorized modifications. CMPPFM has options to exclude comment lines or comment areas for source code comparisons. These options help to focus your attention on logic changes and eliminate the clutter of lines of code that have been commented out. CMPPFM has several options to suppress comment lines to support various AS/400 programming languages.
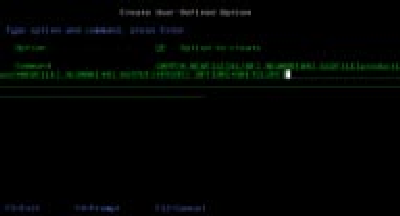
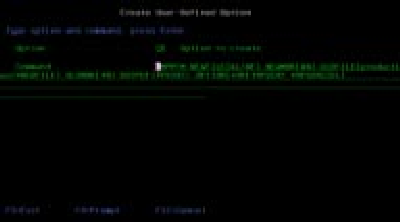
I have set up PDM options for doing source comparisons of CL with RPG III source members but ignoring comments, but you can do the same with Work with User- Defined Options in PDM, as shown in Figures 4 and 5. Normally, you would compare a test version of a source member with a production version. Therefore, I suggest putting the production program library name in the OLDFILE parameter as a default. From PDM, you can prompt the CP or CR option and override the defaults. Remember to replace production in the examples with your production source library name. When you run this PDM option over a source member, CMPPFM produces a completion message at the bottom of the screen, indicating whether the source members are identical (that is, identical except for comment lines). CMPPFM also produces a spool file of three or more pages. (The spool file is three pages if there are no differences and more than three if there are differences, with the differences listed.)
— Richard Leitch
Figure 4: Use this PDM option to compare CL source members.
Figure 5: Use this PDM option to compare RPG source members.
A + B = ...Say What?
Everyone knows how to use RPG to add two numbers together to get the next number in a sequence. Piece of cake, right? But what if you had to add two letters together to get the next letter in a sequence? That’s a bit tougher, but not to worry! There is a way to accomplish this.
Adding one to B to get C, for example, is achieved through the XLATE op code, which enables the (surprise!) translation of a character string on a byte-by-byte basis from one value to another. Laying out the numbering sequence in the “from” argument and offsetting it by one in the “to” argument turns one into two and A into B. Just as in addition
 |
 |
done by hand, the procedure increments from right to left, controlling any carriers that may result.
For this to work, every byte in the source string must be processed individually. Unfortunately, the XLATE op code does not yet have a %Xlate built-in function counterpart that allows translation to take place as part of an expression. To bypass this limitation and avoid the necessity of array processing, I’ve wrapped the XLATE op code in a subprocedure (see Figure 6).
All parameters are declared using the Varying keyword to make the compiler keep track of the actual length and reduce the number of bytes passed through the parameter stack. The Value keyword indicates that the actual parameter value, not its pointer, is passed to the procedure, protecting the source value from possibly unwanted modification.
If overflow occurs, the result is all zeros. Using the source debugger on the sample program shown in Figure 7, you can see the effect of various source strings.
— Carsten Flensberg
***********************************************************************
** To Create:
**
** CrtRpgMod Module(FNC001MR)
** CrtSrvPgm Srvpgm(FNC001S) Module(FNC001MR) Export(*ALL)
**
** CrtBndDir BndDir(FNC001B) Text('General Functions Directory')
** AddBndDirE BndDir(FNC001B) Obj((FNC001S *SRVPGM))
**
***********************************************************************
H NoMain Option( *SrcStmt )
**-- Alfa indexer: -----------------------------------------------------**
D AlfIdx Pr 64a Varying
D String 64a Varying Value
**-- Translate: --------------------------------------------------------**
D Xlate Pr 64a Varying
D String 64a Varying Value
D Xfrom 64a Varying Const
D Xto 64a Varying Const
**-- Alfa indexer: -----------------------------------------------------**
P AlfIdx B Export
D Pi 64a Varying
D String 64a Varying Value
**
D Len S 5u 0
D Ofs S 5u 0
**
D Cur C ' 0123456789ABCDEFGHIJKLMNOPQR-
D STUVWXYZ'
D Nxt C '0123456789ABCDEFGHIJKLMNOPQRSD TUVWXYZ0'
**
C Eval Len = %Len( String )
C Eval Ofs = Len
**
C Do Len
C Eval %Subst( String: Ofs : 1 ) =
C Xlate( %Subst( String: Ofs: 1 ): Cur: Nxt )
**
C If %Subst( String: Ofs: 1 ) <> '0'
C Leave
C EndIf
**
C Eval Ofs = Ofs - 1
C EndDo
**
C Return String
**
P AlfIdx E
**-- Translate: --------------------------------------------------------**
P Xlate B
D Pi 64a Varying
D Xstring 64a Varying Value
D Xfrom 64a Varying Const
D Xto 64a Varying Const
**
C Xfrom:Xto Xlate Xstring Xstring
**
C Return Xstring
**
P Xlate E
Figure 6: This RPG IV module automatically indexes alpha characters.
***********************************************************************
** To Create:
**
**
** CrtRpgMod Module(FNC002MR) DbgView(*LIST)
** CrtPgm Pgm(FNC002I) Module(FNC002MR) ActGrp(QILE)
**
***********************************************************************
H BndDir( 'FNC001B' ) Option( *SrcStmt )
**-- Global variables: -------------------------------------------------**
D Field S 7a Inz
**-- Functions: --------------------------------------------------------**
D AlfIdx Pr 64a Varying
D String 64a Varying Value
**-- Main routine: -----------------------------------------------------**
**
C Do 100
C Eval Field = AlfIdx( Field )
C EndDo
**
C Return
Figure 7: This program shows you how to use the Alpha Indexer shown in Figure 6.











 Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online