- First, a three-letter abbreviation for a verb, such as create, remove, print, or send. See the table below.
- Last, a series of abbreviations for modifiers, such as file, program, job queue, or user profile. These abbreviations are usually three letters long, but there are many exceptions.
| Example Abbreviations | |||
| Verbs | Modifiers | ||
| CRT | Create | F | File |
| CHG | Change | PF | Physical File |
| DLT | Delete | LF | Logical File |
| ADD | Add | SRCF | Source File |
| RMV | Remove | CLPGM | CL Program |
| DSP | Display | RPGPGM | RPG Program |
| WRK | Work with | MSGQ | Message Queue |
| STR | Start | OUTQ | Output Queue |
| END | End | JOBQ | Job Queue |
| DTAQ | Data Queue | ||
| DTAARA | Data Area | ||
| SBS | Subsystem | ||
i5/OS includes a very few commands that do not follow this convention. These are commands that are widely used in the Internet world, such as PING, FTP, CD, and MD. All of these commands have counterparts that do follow the i5/OS convention. See the following table for some examples.
| Commands That Do Not Conform to i5 Conventions | ||
| Command | Alternate Name | Description |
| APING | VFYAPPCCNN | Verify APPC Connection |
| AREXEC | RUNRMTCMD | Run Remote Command |
| CD | CHGCURDIR | Change Current Directory |
| CHDIR | CHGCURDIR | Change Current Directory |
| COPY | CPY | Copy Object |
| DEL | RMVLNK | Remove Link |
| ERASE | RMVLNK | Remove Link |
| FTP | STRTCPFTP | Start TCP/IP File Transfer Protocol |
| JAVA | RUNJVA | Run Java Program |
| LPR | SNDTCPSPLF | Send TCP/IP Spooled File |
| MD | CRTDIR | Create Directory |
| MKDIR | CRTDIR | Create Directory |
| MOV | MOVOBJ | Move Object |
| MOVE | MOVOBJ | Move Object |
| PING | VFYTCPCNN | Verify TCP/IP Connection |
| QSH | STRQSH | Start Qshell |
| RD | RMVDIR | Remove Directory |
| RMDIR | RMVDIR | Remove Directory |
| REN | RNM | Rename Object |
| STATFS | DSPMFSINF | Display Mounted File System Information |
| TELNET | STRTCPTELN | Start TCP/IP TELNET |
Commands are not case-sensitive, except for quoted parameter values. The following are all acceptable versions of the Display User Profile command:
- DSPUSRPRF
- dspusrprf
- DspUsrPrf
- Dspusrprf
- dSPusrpRf
A Few Examples
Suppose you need to create a new message queue. What command would you use? If you look at the list of verbs, you will see that the verb create is abbreviated as CRT. In the list of modifiers, message queue is abbreviated as MSGQ. Put them together and you obtain CRTMSGQ, which is correct. Now, suppose you want to display a data area. Display is DSP, and data area is DTAARA. The command, then, is DSPDTAARA. Correct again.
Suppose you want to delete a CL program. You might think you'd need the DLTCLPGM command, but you would be wrong. That command does not exist. You run the DLTPGM command. The system doesn't care what language you used to create the program when you are going to delete it. Although you use CRTPF to create a physical file, you use DLTF (Delete File) to delete it. It makes no difference to the system what kind of file it is.
Finding a Command
Sometimes you need to execute a command but you cannot remember what command you need, and the naming system doesn't really help if you do not know what you are looking for. I5/OS provides two ways to look up unknown commands: the Select Command (SLTCMD) command and the menus.
The SLTCMD Command
The SLTCMD command presents a list of commands as they are found in a particular library. You need to specify *all, a generic name, or a specific name, as well as the name of the library where you want to search for the command.
For example, suppose you want to delete an RPG program. You try DLTRPGPGM (which seems logical), but there is no such command. To find the command, do the following:
SLTCMD CMD(QSYS/DLT*)
This command will show you a list of all the QSYS commands that begin with the letters DLT. There will be dozens of them, so you need to go through the list, rolling forward if necessary, until you find the command that seems likely. It turns out that the command you needed is DLTPGM.
There is one danger you should be aware of. If you accidentally type a "D" instead of an "S" on SLTCMD, you will run the Delete Command (DLTCMD) command instead. Depending on the authority settings of the user profile you're using, you could delete system commands.
SLTCMD has a shortcut form that is not only quicker to type but avoids the danger of accidental deletion. To use the shortcut form, type part of the command followed by an asterisk and press Enter:
DLT*
Like the full-size version, the shortcut version shows you a list of deletion commands.
Command Menus
Another feature of i5/OS is its hundreds of menus. The GO command is used to display a particular menu. The main menu is called main. You can display this menu by executing the GO MAIN command. Figure 1 shows the results of keying GO MAIN.
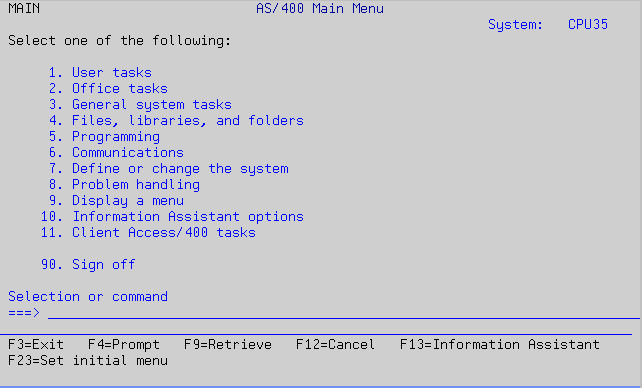
Figure 1: View the main menu by executing GO MAIN. (Click images to enlarge.)
From the main menu, you can select options by keying in the appropriate number and pressing Enter. Or you can execute a command or program. Try the following command and see the resulting panel in Figure 2.
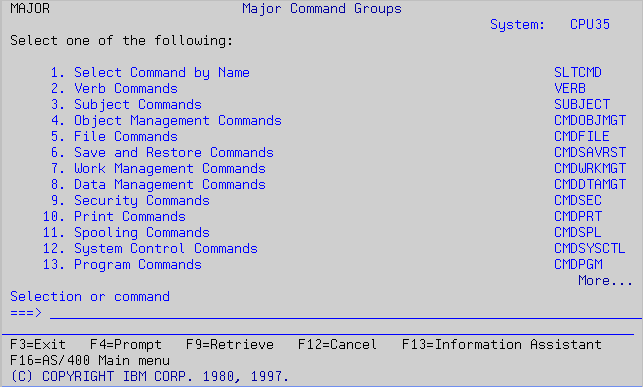
Figure 2: This menu shows the major command groups.
From here, you can go to other menus, such as Verb, which lists all the verbs (such as create, print, submit, and receive). Each option in the verb menu (shown in Figure 3) takes you to another menu, called CMDxxx (where xxx is the verb's abbreviation). From this menu, you can find a command. For example, the CMDDSP menu shows all CL commands that perform some kind of displaying action.
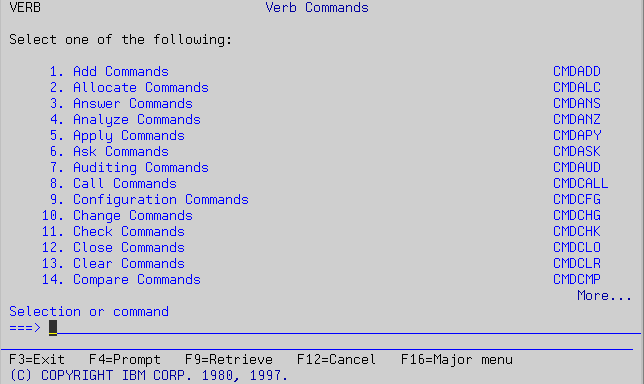
Figure 3: The Verb Commands menu lists all the verbs.
Subject lists all the modifiers, such as output queue and file. Again, each option in the subject menu (shown in Figure 4) takes you to another menu, called CMDxxx (where xxx is the modifier's abbreviation), from which you can find a command. For example, the CMDOUTQ menu lists all commands that relate to output queues, such as create, delete, and work with.
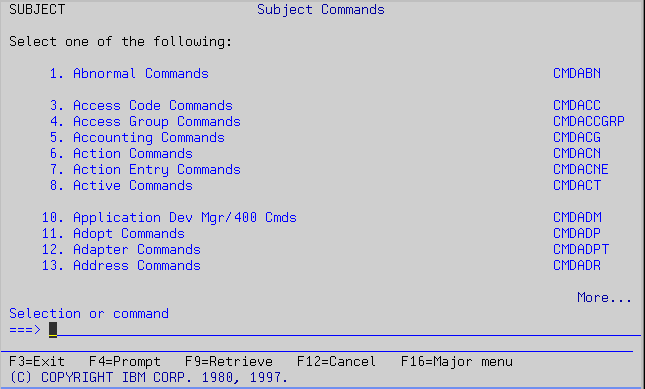
Figure 4: The Subject Commands menu lists all modifiers.
Remember that the GO command can be used with any menu. For example, you have seen that there is a menu named CMDOUTQ (shown in Figure 5). You can go there directly by executing GO CMDOUTQ.
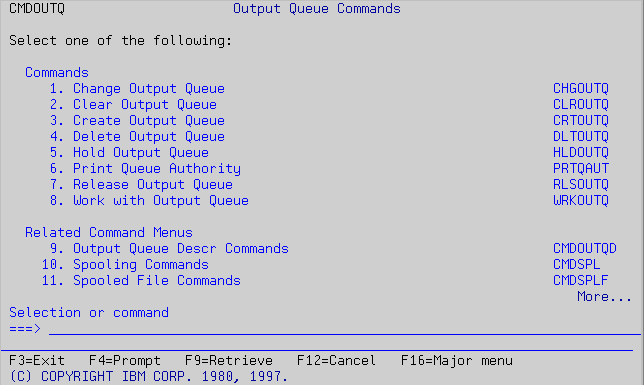
Figure 5: You can go to the Output Queue Commands menu by executing GO CMDOUTQ.
Command Parameters
IBM-supplied commands have many parameters that can accept a wide variety of values. This design allows you to operate and program the system with a fraction of the total number of commands you would need if each individual task required a separate command.
A few commands have no parameters because they do not need any additional information to do their jobs. A good example is Change Password (CHGPWD). When you run the CHGPWD command, the system responds with a panel that allows you to type current and new passwords. No parameters are needed for CHGPWD to know how to do its job.
Most commands, however, do require additional information. The Display Data Area (DSPDTAARA) command, for example, needs to know which data area you want to display. If you run DSPDTAARA without supplying a parameter, expect the system to respond with a message telling you that more information is required.
Every command parameter has a name, also called a keyword. Keywords follow a convention much like the one commands follow. That is, keywords are made up of standard abbreviations. The Change System Value (CHGSYSVAL) command has two parameters, identified by the keywords SYSVAL and VALUE. The SYSVAL parameter identifies the system value to be changed. The VALUE keyword indicates the new value to be given to the system value.
CHGSYSVAL SYSVAL(QSTRUPPGM) VALUE('IPLPGM MYLIB')
Notice the convention that CL uses. The keyword is immediately followed by an open parenthesis. After the open parenthesis, key the parameter value and a close parenthesis. You may leave spaces after the open parenthesis and the parameter value.
Some parameters can be entered positionally. That is, you do not have to type the keywords, but you must enter them in the correct order:
CHGSYSVAL QSTRUPPGM 'IPLPGM MYLIB'
Customizing IBM Commands
Many parameters have default values. If you do not specify a parameter in a command, the command will run as if you had specified the default value. The Display Job (DSPJOB) command provides information about a job. If you do not specify which job you want to know about, DSPJOB assumes you want to display your current job.
Although IBM's choice for default values is sensible, the designers of CL cannot possibly foresee all the environments in which the i5 is used. The result is that, in some cases, the default parameters are not what you would want them to be. Fortunately, you can change the default value for any parameter in any command if the parameter is not a list parameter (a parameter that accepts two or more values) and if the parameter already has a default value. You cannot assign a default value to a parameter that is defined as mandatory, nor to one that shows no parameter at all when you invoke the command prompter. To change the default value of a parameter, run the Change Command Default (CHGCMDDFT) command.
The Simple Approach
The simplest way to change an IBM-supplied command is to change the command itself in QSYS. For example, suppose you often use the Work with Output Queues (WRKOUTQ) command to display the contents of output queue qprint. WRKOUTQ's outq parameter defaults to *all, which takes a long time to process and is not what you want.
You can change WRKOUTQ's default for the OUTQ parameter so that QPRINT is assumed if no value is entered. This change would allow you to work with QPRINT by typing WRKOUTQ and pressing Enter. Here's how to change the default:
CHGCMDDFT CMD(QSYS/WRKOUTQ) NEWDFT('OUTQ(QPRINT)')
This method works, but it has one serious disadvantage. When you upgrade to a new release of i5/OS, or sometimes even when you apply certain PTFs, you will lose your new default values and the system will not alert you to it. If this is not a problem for you, it is OK to change QSYS commands directly. If it is a problem, read the learned approach section.
The Learned Approach
A safer approach to changing command defaults is by first making a copy of the original QSYS command and then changing the copy, not the original. Here is the process:
1. Create a user library where you can place your copies of QSYS objects. You might name it ALTQSY, for Alternative QSYS:CRTLIB LIB(ALTQSYS) TEXT('Alternative QSYS')
2. Place this library ahead of QSYS in the system portion of the library list. This change guarantees that your copies of the objects will be used instead of the QSYS originals:WRKSYSVAL SYSVAL(QSYSLIBL)
Select option 2. Insert ALTQSYS before QSYS.
3. Copy the QSYS command you want to change into ALTQSYS: CRTDUPOBJ OBJ(WRKOUTQ) OBJTYPE(*CMD) FROMLIB(QSYS) +
TOLIB(ALTQSYS)
CHGCMDDFT CMD(ALTQSYS/WRKOUTQ) +
NEWDFT('OUTQ(QPRINT)')
When you update to a new release, you will need to clear the ALTQSYS library, copy the commands from QSYS, and reapply the changes.
Document all the changes you make to command parameters in a CL program. For each command with changed defaults, include the section of code shown below into the CL program.
DLTCMD CMD(ALTSYS/xxx)
MONMSG MSGID(CPF0000)
CRTDUPOBJ OBJ(xxx) FROMLIB(QSYS) OBJTYPE(*CMD) +
TOLIB(ALTQSYS)
CHGCMDDFT CMD(ALTQSYS/xxx) NEWDFT(...)
The xxx represents the name of the command you have changed. When you upgrade your system to a new release or apply PTFs that might change the definition of the original QSYS commands, you should compile this CL program and execute it.
First, it deletes the command in ALTQSYS and creates a new one from QSYS. The copy of the command in the ALTQSYS command will always reflect the latest changes made by IBM (such as added parameters). Finally, it changes the default value in the ALTQSYS copy.
The Command Prompter
Most i5/OS commands have parameters to fine-tune the purpose of the command or the task to be performed by the command. For instance, the Display Message (DSPMSG) command uses a parameter to determine what messages to display. If parameters didn't exist, you would need a different command for each message queue, which would be impractical.
Invoking the Command Prompter
The command prompter can be activated by keying in the name of the command at the command line and pressing F4 instead of Enter. When you do this, the system presents the prompt panel for that command. For example, you can invoke the prompter for the Change Library List (CHGLIBL) command shown in Figure 6 by entering the following command:
CHGLIBL ... press F4:
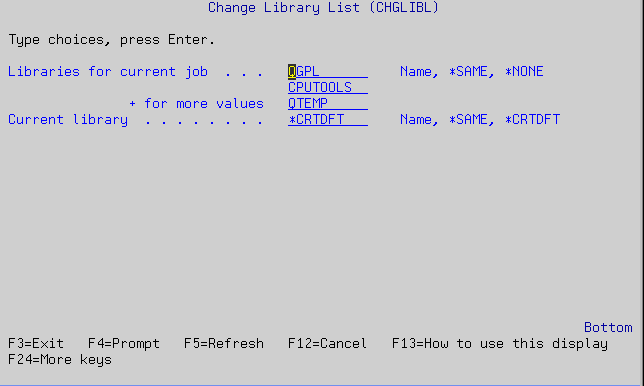
Figure 5: Invoke the prompter for the Change Library List (CHGLIBL) command.
You also can invoke the command prompter by typing a question mark (?) immediately followed by the command name at the command line and pressing the Enter key:
?CHGLIBL
Command Parameters
In the previous illustration, the CHGLIBL command has two parameters. The first parameter (Libraries for current job) is a list, while the second parameter (Current library) is a normal parameter.
The command prompter gives you input fields so you can change the values of the parameters. On the right side of the screen, it shows you what values are acceptable. For example, the first parameter allows entry of a Name, *SAME, or *NONE. The second parameter allows a Name, *SAME, or *CRTDFT.
The command parameter names are not shown unless you press F11 or change your user profile with USROPT(*CLKWD). The first parameter has a keyword of LIBL, and the second parameter's keyword is CURLIB.
Changing Parameter Values
Simple parameters, like CURLIB, are easy to change by typing over the old value (which shows *CRTDFT in the example). List parameters, like LIBL, are more difficult. If you only need to replace one element in the list for another, proceed as you would with a simple parameter: Type over the old value and press Enter.
If you want to remove one of the elements of the list, blank it out and press Enter. Optionally, you can type a less-than (<) character and at least one space and then press Enter. Both methods yield the same result.
If you want to insert a new element to the list, somewhere in the middle, type a greater-than (>) symbol and at least one space in the input field before what you want to insert and then press Enter. The command prompter will present a different panel where you can type one or more new elements. When you are done inserting, press Enter. The system returns to the command prompter with the new values already inserted.
If you want to add a new element at the bottom of the list, type a plus (+) sign and at least one space on any of the elements of the list and press Enter. The system will present a different panel to let you type the new elements to be inserted. When you are done, press Enter again, and the system will take you back to the command prompter, with the new values already appended at the end of the list.
Sometimes you need to type more characters than will fit in the input field provided by the prompter. This happens when you are entering a CL program and one of the parameters is an expression rather than a variable name. To lengthen the input field, type an ampersand (&) and at least one space and press Enter. The command prompter will lengthen the input field to the next higher length it provides.
Although the process of lengthening a parameter's input field can be repeated several times (until the input field reaches its maximum length of 512 spaces), it doesn't guarantee that the command prompter is going to accept that many characters. For example, the Display User Profile (DSPUSRPRF) command expects a user profile name in the USRPRF parameter. Because it is a name, it can be up to 10 characters long. You can lengthen the input field to 32 characters and even type 32 characters in the input field. When you press Enter, however, the prompter will reject your input because it is too long.
Further Reading
IBM's New User's Guide
IBM's System Operator's Guide
IBM's CL Reference
MC Press' The AS/400 Owner's Manual
MC Press' IBM i5/iSeries Primer, Fourth Edition

















 Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online