Magical Macro Changes
In the past, macros haven't been PC5250's fastest feature, but that's changing with V5R1. Macro performance has always been affected by how PC5250's macro recording function works. In the macro playback files (*.MAC), PC5250 stores all activities that occurred while the macro was recording, including think time. However, when you play back a macro, you usually don't want to replay the think time. In earlier versions of PC5250, the only way to eliminate the think time playback was to open each macro and manually delete the wait commands.
Figure 1 shows the V5R1 PC5250 Record Macro/Script dialog where you can customize the macro wait-time parameters that are used when a macro is recorded.
Figure 1: Now you can make your PC5250 macros run faster by selecting the proper user wait-time parameters.
In the Record User Wait Time section of this screen, there are three new options. To store actual wait time, choose the Actual radio button. To forego the wait-time storage and allow the commands to execute instantly in sequence, choose the None radio button. To request a constant wait time of 25 ms (milliseconds) be used for all wait-time commands, choose the Fixed radio button. At present, there is no way to change the constant other than to modify the macro script file (*.MAC). However, if you use the None radio button, you'll get faster macro playback time without the need to edit the macro, thus significantly improving your macro's performance. Also, remember that there are multiple methods available to begin recording a macro. The easiest method is to select the Start keystroke recording icon (i.e., the red arrow) from the toolbar. You can also record a macro from the menu bar by selecting the Start Recording Macro function from the Actions drop-down list.
The ability to prevent the storage of hidden data fields in PC5250 macros is another cool macro function. For example, you may want to start recording a macro at the sign-on screen where you entered your user password. In earlier PC5250 releases, the password would have been written as unprotected data into your macro file as you record your keystrokes, leaving the password in full view of anyone who could display the macro. V5R1 PC5250 allows you to enter a parameter in your workstation profile (.ws file) that prevents the recording and storage of data in a hidden field, such as a password prompt. To activate the hidden field protection option in your macros, enter the following line into your workstation profile under the [Keyboard] stanza:
HideNonDisplayDataOnRecord=Yes
When the macro is played, all the data except for that in the hidden fields will be re-displayed. The user will be prompted to enter the hidden data using input screens, as shown in Figure 2.
Figure 2: A new configuration setting stops PC5250 from storing hidden fields, such as passwords, in a macro.
You may have instances in which you won't want users to record macros. You can use two methods to block recording. The quick method involves removing the Start Recording Macro selection from the Actions menu bar drop-down list by using the menu bar customization program, which can be found in the IBM Client Access Express Emulator Folder. Once this item has been removed from the menu bar (even though the icon may still be on the toolbar), the Start keystroke recording icon will not work. A second method involves removing the Start keystroke recording icon from the tool bar, which can be deleted by right-clicking on the icon and then selecting the Delete Item option from the pop-up menu. For security purposes, you can remove the PCSCMENU.EXE program from the Client Access emulator directory; this will prevent users from re-adding the Start Recording Macro item into the menu bar options. Of course, there is another way to do this, and that is through the new PC5250 policy support that IBM added in Client Access Express for Windows V5R1 PC5250.
Sensational Security Changes
Earlier versions of PC5250 had limited Microsoft policy support, which could be used to prevent or limit PC5250 code installation, display and printer session configuration, PC5250 usage by users or groups, and a number of other functions. In addition to existing Microsoft policy support in earlier versions of Express Client, the following new user prevention policies are now supported in V5R1 PC5250:
- Users cannot change the workstation profile (.WS file)
- Users cannot change the menu bar or toolbar
- Users cannot change the batch file setup
- Users cannot change the keyboard setup
- Users cannot change the mouse setup
- Users cannot execute a Java applet in a macro
- Users cannot run a macro
Windows policies are supported on a per-user or per-PC basis. The majority of the new policy support is limited to restricting function on a per-user basis. For more information on how to configure Windows Policy support to limit PC5250 functionality, see "Express Client's PC5250 Application Integration Enhancement."
V5R1 PC5250 has additional security changes. Earlier versions of Express Client supported Secure Sockets Layer (SSL) server authentication. This authentication scheme supports PC-to-server authentication, encrypting all data and requests between the PC and the server. Server authentication means that the PC can be assured that the server is what it claims to be. However, many customers would like to see the opposite authentication schema employed; that is, the Server being assured that the PC is what it claims to be, which is called client authentication. This is now supported by V5R1 Express Client and PC5250. Figure 3 shows the Connection screen that is displayed by selecting Communication from the menu bar and then selecting the Configure option. From the Configure PC5250 menu, click on the Properties button to display this screen. 
Figure 3: Client authentication, in which the server verifies the client's identity, has also been added to V5R1 PC5250.
If you chose to use client encryption, there are two methods available via the Connection screen to provide your certificate to the server. You can choose the Use default radio button, which allows you to use the default client certificate in the PC key database, or you can choose the Select certificate when connecting radio button, and you will be prompted to select a client certificate when you connect to the system. SSL communications between the client and the server are secured at one of two encryption levels: 56-bit or 128-bit. (Client and server encryption levels may vary by geography.)
Cool Cut-and-Paste Changes
In V5R1 PC5250, IBM enhanced the cut-and-paste function. In earlier versions, when you wanted to cut data from a Lotus 1-2-3 or Microsoft Excel spreadsheet and paste that data into your display session, PC5250 would not correctly paste tabulated text into PC5250 input-capable display fields (i.e., it would not keep the data in tabular format). Changes in V5R1 PC5250 GUI allow you to modify how cut and paste works.
Figure 4 shows the Edit Options menu where you can set Tab character processing preferences. To get to this menu , select the Edit menu bar item, then select Preferences, then select Edit Options, then click on the Paste data to fields radio button. When PC5250 encounters a tab character, it will paste the text character in the next unprotected field. Now your spreadsheet data will be pasted into the display in the format you want.
Figure 4: New paste options allow you to correctly copy Excel spreadsheet data and paste it into PC5250 screen fields.
Improvements to spreadsheet cut-and-paste compatibility are not the only cut-and-paste modifications in V5R1. IBM customers have long wanted the ability to copy text from a Lotus WordPro or Microsoft Word document and paste it into a PC5250 display. However, in the past, formatting differences caused problems when trying to paste document data to a 5250 display: PC5250 processes displays by fields or multiple lines; a document editor processes a document as one line, and PC5250 will not convert a single line into multiple fields (i.e., lines). Because of this difference, when earlier versions of PC5250 went to copy the field onto its screen, the program truncated the line and did not wrap the data from one line to the next on the display. Now you can tell PC5250 to treat text data as if it were from a document editor rather than from another PC5250 session. To set PC5250 to wrap data onto the next field, add the following statement to the [Edit] stanza in your workstation profile (.ws file):
PasteLineWrap=Yes
This process is the only way to add line-wrap capability as PC5250 does not provide a GUI for this function.
Marvelous Miscellaneous Changes
While IBM has made it easy for you to have only one workstation profile per display emulation session per system, it would be helpful to use that same workstation profile to connect to all of your iSeries boxes. This was not previously possible because the PC5250 configuration menu requires a system to be specified. With the V5R1 Express Client, using Operations Navigator and a new feature of PC5250, IBM has made the system parameter of the PC5250 configuration file a variable. To use this feature, first create a workstation profile called CWB_TEMP.WS and place it in the EmulatorPrivate subdirectory under your Express Client install directory. (This directory can be located either on your PC or on your server). Second, open the AS/400 Operations Navigator (see Figure 5), right-click on the system for which you want to start a PC5250 session, then select Display Emulator from the drop-down list.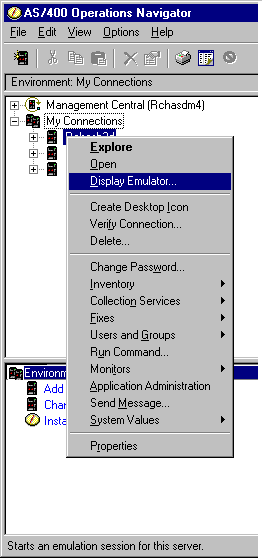
Figure 5: V5R1 Express Client and PC5250 let you use one default workstation profile for all your installations.
Express Client will look for the CWB_TEMP.WS file in the EmulatorPrivate directory and, if it finds the file, it will use that file to create the workstation profile to start, thereby allowing you to use the same workstation ID naming structure for all systems listed in Operations Navigator tree. If you have not created this CWB_TEMP.WS file, the Express Client will use its own default workstation profile, which will not provide a generic workstation ID for the system. Note that this option will work only if you have not used the Operations Navigator (Op Nav) method of starting a PC5250 session for that system before. If you used Op Nav to start PC5250 before you made this change, go to the iSeries Client Access Web page and read the information regarding the registry entry changes that you would need to modify to use your default workstation profile template.
Another GUI change worth mentioning is the ability to change the file storage settings. This change is for shops moving to Windows 2000 that would like to store default PC5250 files in the My Documents folder and for shops running PC5250 from a server (for example, using Windows Terminal Server) that would like to store PC5250 files on the server. To change the file storage settings from the default location to another location, select the Client Access Properties icon, which is located in the Client Access Express folder. Figure 6 shows the Client Access Properties screen that will be displayed. 
Figure 6: You can change the storage default for PC5250 files to the My Documents folder or to another user-defined location.
Click on the PC5250 tab. In the Path to PC5250 emulator files area, these three selections are available to command Express Client to change the default location for the storage of PC5250 files:
- Client Access installation directory
- My Documents
- User specified path
The default path for PC5250 files is the Emulator/Private directory, which is also the path used when the Client Access installation directory radio button is selected.
There is one more set of changes--for international users--to discuss. On the configure PC5250 screen, which is reached by selecting the Communication menu bar item, then selecting Configure, there are additional host code page options that you can select for Korean, Taiwanese, and Japanese configurations. A host code page is the default translation table that is used for mapping iSeries EBCDIC code to the appropriate ANSI graphic on the PC. In addition, the bestfit and margins options on the Page Setup for a Printer emulation session, which is accessed by selecting the File menu bar item, then Page Setup, now support double-byte character set (DBCS) printers.
Time's Up!
I've covered some of the significant changes in the V5R1 version of PC5250. I hope that you'll take advantage of at least a couple of these new features. Now, the coffee break is over; it's time to get back to work!
Becky Schmieding is a senior programmer at IBM Rochester. She is an IBM Certified Project Manager responsible for Client Access Express, including Operations Navigator and Management Central, iSeries Access for the Web, iSeries Integrated File Systems, iSeries NetServer, Host Servers, and the Java Toolbox at the IBM Rochester development organization. She is also responsible for the integration of other IBM software products onto the eServer iSeries.











 Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online