Within the iSeries Information Center, you can access Web-based tools that use cutting-edge technology. One of these advanced tools is the OS/400 system value finder. This finder allows you to search for system values in order to solve your system management problems. The system values have had major developments since V5R1, and these developments are documented in the Information Center.
Finders
Finders are interactive programs that locate specific information within a data set. To do this, the finders work like a search engine, but they only search through information that is specific to the finder as opposed to searching the entire Information Center. These finders allow users to specify a variety of searches. For example, a finder might allow a user to search on a keyword or to display a specific category of information.
Finders reside with the documentation to assist you in locating the information that is specific to your needs. Finders quickly locate documentation that is relevant to your search criteria and help you access it quickly. The OS/400 system value finder, for example, searches through over 100 system values to find information specific to one system value.
System Values
System values are pieces of information that affect the operating environment of the entire iSeries system. System values are not objects on the system. Rather, system values contain control information that affects system operation. You can use system values to change the system in order to define the working environment. For example, system time, auditing level, language characteristics, and certain security features are all set by system values. With the system values, you are able to configure your systems for secure, optimal performance.
Prior to V5R1, system values were only accessed via the character-based (green-screen) interface. To view or edit system values, you needed to open the Change System Value screen by specifying the Change System Value (CHGSYSVAL) command. Figure 1 shows the Change System Value screen.
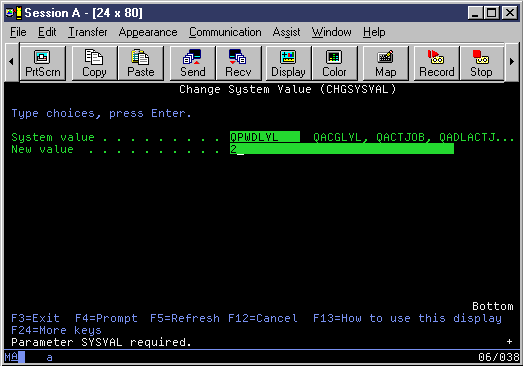
Figure 1: Before V5R1, managing system value settings required using the CHGSYSVAL command in the character-based interface.
On the Change System Value screen, you must specify the name of the system value as well as the new value. For example, if you want to change the password level from short passwords to long passwords, you have to know that the name of the system value is QPWDLVL, as shown in Figure 1. In addition, you need to know the possible values for the system value that you are changing, specified on the screen as New value. In this example, you need to know that 0 represents short passwords and 2 represents long passwords. The character-based help provides details about each system value and its possible values.
The character-based system value names and possible values are not as descriptive as the iSeries Navigator interface, making them harder to remember and manage. Therefore, iSeries Navigator's (formerly known as Operations Navigator) graphical user interface (GUI) provides support for system values in V5R1 via a friendly, easy-to-use interface. Now, you do not need to remember character-based names for each system value; instead, you can view all of the system values and their settings through the GUI. This makes managing system values fast and easy. To access system values in iSeries Navigator, use the path that is highlighted in Figure 2.
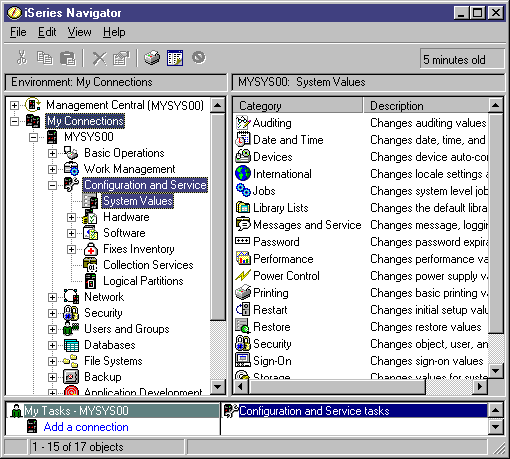
Figure 2: Use this path in iSeries Navigator to manage system values.
To access the password system values in iSeries Navigator, select a system ->Configuration and Service -> System Values -> Password. This will open the Password System Values dialog shown in Figure 3. From the General tab on the Password System Values dialog, select "Long passwords using an unlimited character set (2)." Then, simply click OK to change the password level. Because the GUI uses descriptive language, managing system values is easy. Just point and click.
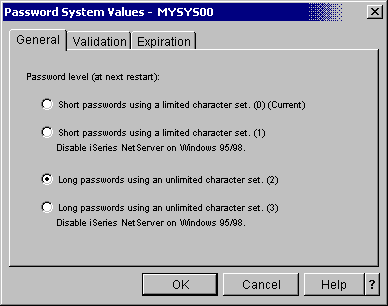
Figure 3: The iSeries Navigator Password dialog allows you to control password values.
Since the system values are now available in iSeries Navigator, the OS/400 system value finder helps system administrators transition from the character-based interface to the iSeries Navigator interface. The old character-based interface uses strings such as QSECURITY and QPWDLVL; the GUI uses the corresponding phrases "security level" or "password level," which are easier to remember. In addition, it uses descriptive words for the possible values. The OS/400 system value finder matches the old terminology with the new to make the transition between interfaces easy for system administrators.
OS/400 System Value Finder
The OS/400 system value finder is an interactive Web-based tool that allows the user to search for a specific system value or to display a list of system values by category. This new technology replaces pages after pages of hard-copy documentation. Users no longer have to page through books to find details about a specific system value. Now, they can simply use the OS/400 system value finder to obtain the documentation they are looking for. (See Figure 4.)
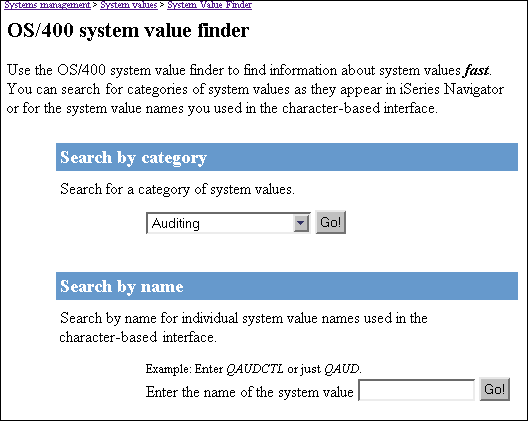
Figure 4: The OS/400 system value finder in the iSeries Information Center provides an easy way to find information quickly about system values.
To provide optimal performance, the finder is built using JavaScript code. When a search is performed, the finder only searches the system value database in order to provide search results that are specific to the search-specified text.
This finder is unique in that it serves two types of users. As you can see in Figure 4, you can perform searches either by category or by name. This makes it useful to users who are familiar either with the new iSeries Navigator names or with the character-based names.
The users familiar with the character-based interface are able to type the character-based name for the system value into the finder. For example, you can specify QSECURITY, QDBFSTCCOL, or just a portion of the character-based name (QDBF). Once the system value is found, a page is displayed that contains information needed to transition you to the new iSeries Navigator interface. This page provides a description of the system value and the character-based name, as well as the new iSeries Navigator name. In addition, it points out where to find the system value in the iSeries Navigator interface.
The users unfamiliar with the character-based names will be able to display a category of system values. iSeries Navigator divides the system values into 17 categories: Auditing, Date and Time, Devices, International, Jobs, Library Lists, Messages and Service, Password, Performance, Power Control, Printing, Restart, Restore, Security, Sign-on, Storage, and System Control. When a category is selected from the finder, a list of all the system values associated with that category is displayed. This list includes the iSeries Navigator name as well as the character-based name.
From either search method, you will ultimately view a Web page that is specific to a particular system value. This page contains detailed information that will assist you in setting the system value to a value that is specific to your company's needs. A Quick Reference section is also provided for each system value. This section lists the most frequently needed information. It includes the character-based name, the default value, whether or not it can be locked, when changes to the system value take effect, what authority is needed to change it, and possible values. In addition, this page contains information about how the system value works, how it affects your operating system, and whether or not it has any impacts on other functions or system values.
The OS/400 system value finder provides you with one way of determining where the problem lies between you and your systems--even if you are just unfamiliar with the new iSeries Navigator interface and need help moving from the character-based interface to the iSeries Navigator interface. To take advantage of this valuable information, use the OS/400 system value finder.
What's New for V5R2
V5R2 shows exciting enhancements for system values. You now have more control of the security system values. This enhancement allows you to specify whether or not a security system value can be changed. In addition, new system values were added to iSeries Navigator to further customize your iSeries server, and existing system values were modified to offer more options. Finally, a new category, Restore, was added to the 16 pre-existing categories.
Restore Category
Now, you can view and edit system values through the new Restore category to control or change the overall operation of your server. The Restore category is new, but its individual system values already existed. The table in Figure 5 identifies the system values associated with the new Restore category.
| Name in iSeries Navigator | Name in Character-Based Interface | Description of System Value |
| Convert objects during restore | QFRCCVNRST | Specifies which objects are converted before being restored |
| Allow restore of security-sensitive objects | QALWOBJRST | Specifies the objects to be restored and identifies whether or not they can be restored while installing software fixes |
| Verify object signatures during restore | QVFYOBJRST | Specifies whether objects without signatures and/or objects with signatures that are not valid are restored |
Figure 5: The Restore system values allow you to manage restore operations.
In addition to the Restore category being new, this category also provides additional features and enhancements from previous releases. There are three main changes when restoring objects. First of all, if an object fails to be converted, it will not be restored on the system. Second, the Convert objects during restore (QFRCCVNRST) system value provides more options. Third, the Force object conversion parameter does not override the Convert objects during restore (QFRCCVNRST) system value unless Force object conversion is set to *YES *ALL, which is the most strict state.
New Lock Function for Security-Related System Values
Most security system values can be changed only by a user with Security Administrator (*SECADM) and All Object (*ALLOBJ) special authorities. To prevent even these users from changing these system values during normal operation, Start System Service Tools (STRSST) and Dedicated Service Tools (DST) provide an option to lock these security-related system values so users may not change their settings.
In addition, this function prevents programs that are running with adopted authorities from being able to change these values and change them back. Only a service tools user ID with the appropriate service tools privilege running SST or DST can lock or unlock these system values.
Each security-related system value that is affected by this new function is shown with a lock icon next to it in the iSeries Navigator interface. The lock is either open (changes allowed) or closed (no changes allowed), as shown in Figure 6.
![]()
Figure 6: This closed lock icon identifies which security-related system values cannot be changed.
New and Changed System Values for V5R2
Many system values are either new or changed for V5R2. To identify the system value changes for V5R2, see the table in Figure 7.
| New System Values | ||
| Name in iSeries Navigator | Name in Character-Based Interface | Description |
| Allow background database statistics collection | QDBFSTCCOL | Specifies the types of database file statistics collection requests that are allowed to be processed in the background. |
| Detach printer output after jobs have ended | QSPLFACN | Specifies whether or not spooled files are kept with a job or detached from the job. |
| Changed System Values | ||
| Name in iSeries Navigator | Name in Character- Based Interface | Description |
| Security-related system values | QALWOBJRST QALWUSRDMN QAUDCTL QAUDENACN QAUDFRCLVL QAUDLVL QAUTOCFG QAUTORMT QAUTOVRT QCRTAUT QCRTOBJAUD QDEVRCYACN QDSPSGNINF QDSCJOBITV QINACTMSGQ QLMTDEVSSN QLMTSECOFR QMAXSGNACN QMAXSIGN QPWDEXPITV QPWDLMTAJC QPWDLMTCHR QPWDLMTREP QPWDLVL QPWDMAXLEN QPWDMINLEN QPWDPOSDIF QPWDRQDDGT QPWDRQDDIF QPWDVLDPGM QRETSVRSEC QRMTSIGN QRMTSRVATR QSECURITY QSHRMEMCTL QUSEADPAUT QVFYOBJRST | Added a locking option to prevent these system values from being changed |
| Pass-through devices and Telnet | QAUTOVRT | Added a new value: Run registered exit programs |
| Force conversion on restore | QFRCCVNRST | Increased number of options and moved from the System Control category to the Restore category. |
| Server authentication interval | QSVRAUTITV | Removed from iSeries Navigator |
As you can see, there are many new and changed system values--all of which can help improve the performance of your systems.
With the OS/400 system value finder and the enhancements in V5R2, you are able to diagnose where you are losing touch with your systems. Each system values topic in the Information Center contains information about managing your systems through the system values' settings. You can use the OS/400 system value finder to find information about a specific system value or a category of system values. Either way, the OS/400 system value finder will keep you and your systems on track.
Additional Finders
The OS/400 system value finder is just one of many finders that the iSeries Information Center offers. The following are other finders that you can access through the iSeries Information Center:
API finder--Allows you to search IBM's application programming interfaces
CL command finder--Allows you to search for control language commands
Journal code finder--Allows you to search for journal codes and entry types
IPL system reference code (SRC) finder--Allows you to search for a SRC, which is useful when you have an error during an IPL
Connie Scholtes is a software developer for IBM. She has been the lead information designer for system values since 2000. This includes documenting the online help in iSeries Navigator as well as delivering documentation in the iSeries Information Center. If you have any questions or comments for Connie, you can reach her at











 Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online