Are you sure you're properly securing your IP applications?
If your IBM i is running TCP/IP, you have a problem. While the availability of IP applications is a blessing in that it gives your company an easy way to access your systems based on a set of defined standards, it also gives hackers an easy way to get into your systems and data using defined standards. Utilizing secure IP connectivity for your Telnet, FTP, and HTTP connectivity can help to curb the problem, but what about all of those other IP applications?
Often, the worst part of the issue can be getting a handle on exactly what applications you have running over TCP/IP. While you can display currently active IP connections using the NETSTAT command, that command gives only a snapshot of what's currently happening. The ideal would be a way to capture that activity on a timed basis to monitor TCP/IP traffic. By stringing together a few IBM APIs, we can do exactly that. In this article, we'll explore a utility to monitor IP traffic as well as learn exactly how to control traffic on restricted ports.
Monitoring TCP/IP Traffic
The command to dump IP network status data is DMPIPSTS. The source for this command can be found here. The parameters for this command are shown below:
|
Dump IP Net Stat Data (DMPIPSTS) Parameters |
|||
|
Keyword |
Description |
Choices |
Notes |
|
OUTFMT |
Output format |
*OUTFILE, *STMF, *PRINT |
Optional |
|
OUTFILE |
Output File |
Qualified object name |
Optional |
|
|
Qualifier 1: Output File |
Name |
|
|
|
Qualifier 2: Library |
Name, *LIBL, *CURLIB |
|
|
OUTMBR |
Output member |
Character value, *FIRST |
Optional |
|
ADDRPL |
Add or Replace Records |
*ADD, *REPLACE |
Optional |
|
STMF |
Output Stream File |
Character value |
Optional |
|
STMFTYPE |
Stream File Type |
*TXT, *CSV |
|
The first parameter on this command identifies the destination for the data using one of the following three special values:
- *OUTFILE—This value identifies that the output should be sent to the physical file identified on the OUTFILE parameter and the member identified on the OUTMBR parameter. The "Add or Replace Records" parameter is also used to identify whether or not to clear the destination file prior to adding new records.
- *STMF—This value specifies that the output should be sent to the stream file identified on the Output Stream File parameter (STMF). The Stream File Type parameter (STMFTYPE) identifies the format of the output stream file as one of the following values: *CSV (the output is sent to a comma-delimited text format) or *TXT (the output is sent as a flat text file format).
- *PRINT—This value defines that the output should be sent to a spooled file. When this option is used, multiple spooled files are created as a result of the number of columns of output.
Data Generated
The data generated by this command contains local and remote connection data along with associated job data for each IP network connection available at the time the command is executed. Below is a list of the columns generated by this command:
|
File Layout for the Output of the DMPIPSTS Command |
||||
|
Field Name |
Description |
Data Type |
Length |
Dec Plc |
|
IPCRMTADR |
Remote System IP Address |
CHAR |
15 |
|
|
IPCRMTPORT |
Remote System Port # |
DECIMAL |
10 |
0 |
|
IPCRMTNAME |
Remote System Host Name |
CHAR |
256 |
|
|
IPCRMTSVNM |
Remote Service Name |
CHAR |
32 |
|
|
IPCRMTSVDS |
Remote Service Desc |
CHAR |
50 |
|
|
IPCLOCADR |
Local System IP Address |
CHAR |
15 |
|
|
IPCLOCPORT |
Local System Port # |
DECIMAL |
10 |
0 |
|
IPCLOCNAME |
Local System Host Name |
CHAR |
256 |
|
|
IPCLOCSVNM |
Local Service Name |
CHAR |
32 |
|
|
IPCLOCSVDS |
Local Service Description |
CHAR |
50 |
|
|
IPCCNNSTT |
Connection Status |
CHAR |
15 |
|
|
IPCCNOPNTP |
Connection Open Type |
CHAR |
15 |
|
|
IPCNETCNTP |
Connection Type |
CHAR |
10 |
|
|
IPCBYTIN |
Bytes In |
DECIMAL |
20 |
0 |
|
IPCBYTOUT |
Bytes Out |
DECIMAL |
20 |
0 |
|
IPCIDLTIME |
Idle Time (hhhhhmmss) |
DECIMAL |
9 |
0 |
|
IPCJOBNAM |
Connection Job Name |
CHAR |
10 |
|
|
IPCJOBUSR |
Connection Job User |
CHAR |
10 |
|
|
IPCJOBNBR |
Connection Job Number |
CHAR |
6 |
|
|
IPCCURRUSR |
Current User Profile |
CHAR |
10 |
|
|
IPCRUNUSER |
Run User |
CHAR |
10 |
|
|
IPCRUNTMS |
Run Timestamp |
TIMESTMP |
10 |
|
The same output is generated whether you select *PRINT, *OUTFILE, or *STMF output. The main difference between the three options is that the *OUTFILE option allows you to indicate that you want to add the output to an existing physical file. This option gives you the ability to capture data over a period of time at given intervals. The command below shows how you would do this;
DMPIPSTS OUTFMT(*OUTFILE) OUTFILE(MYLIB/IPSTATUS)
OUTMBR(*FIRST) ADDRPL(*ADD)
This command will add current IP status data to the file IPSTATUS in library MYLIB.
When generating output to *STMF, you have the option of generating the output as a fixed-format text file or as a comma-delimited *CSV file. Figure 1 below shows a sample of the data as displayed in Microsoft Excel.
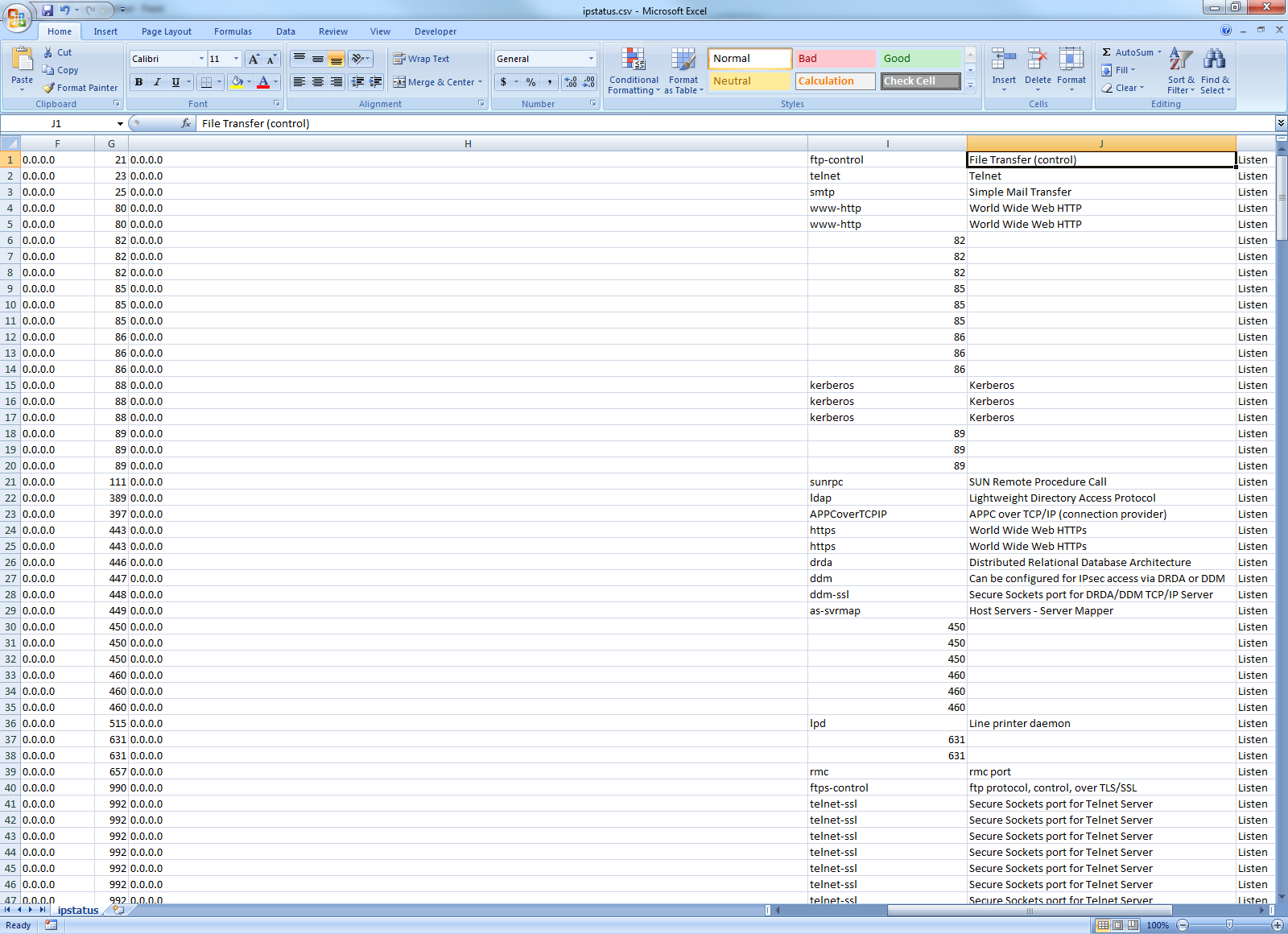
Figure 1: This is a sample of output generated to a comma delimited file.
To generate a file like the one shown above, the command below would be executed:
DMPIPSTS OUTFMT(*STMF) STMF('/home/reports/ipstatus.csv')
STMFTYPE(*CSV)
Knowledge Is Power
The key to securing your TCP/IP connectivity is knowing what IP traffic you're using. Because the output includes a timestamp indicating when the output was generated, you have the ability to also identify how long connectivity to a given port was connected and the IP address of the client that connected to that port. The output also identifies the user who started the job that is servicing the IP request locally. This can be a big help in ensuring that unnecessary (or even rogue) applications aren't leaving IP ports open on your system. Securing traffic for standard applications like Telnet, HTTP, or FTP is only half the battle. Identifying all of the "other" traffic is as important as, or maybe even more important than, implementing SSL on all of those standard applications. Now you have the utility to help you do that.
















 Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online