Don't you wish there were a better, faster way to protect your system against viruses? Viruses are evolving so quickly that daily virus definition updates and weekly scans no longer find viruses soon enough in an on-demand operating environment. Systems need to provide real-time protection with minimal run-time performance impact. People often accidentally open objects containing viruses that can cause millions of dollars in lost business. An ideal virus scanner would protect systems in real-time by preventing the opening of such objects. Can this be achieved? Yes! IBM i5/OS V5R3 now provides scan enablement for real-time virus protection. All you need to do is to purchase a virus scanner that takes advantage of this new enablement.
Viruses Can't Get on My iSeries System!
Many would like to believe that their iSeries systems are completely secure against viruses. This is not a realistic assumption. With today's viruses, all it takes is a connection to a network for viruses to find their way in. Many practices provide an ideal breeding ground for viruses: sharing files or directories in an insecure manner, not filling security holes, or mapping a network drive. Viruses found in the Integrated File System (IFS) do not affect the i5/OS itself. Instead, these viruses are propagated throughout the network to any PCs that access the IFS, which acts as a host.
Traditional Virus Protection
The traditional virus protection solution in the industry is to perform daily virus definition updates along with weekly virus scans using a native virus scanner. If there is no native virus scanner available, then oftentimes, one system's native virus scanner is used to perform virus scans of remote systems over the network. Neither solution is ideal. The network virus scans create even more problems: They are slow, use up valuable network resources, and can potentially give hackers access to the data flowing across the network. In addition, network virus scans can encounter unique operating system characteristics, such as those found in the i5/OS IFS, that could cause them to go into infinite loops. For example, a symbolic link like /QOpenSys/QOpenSys, which points to /QOpenSys, can cause looping. Traditional virus protection is no longer good enough in an on-demand operating environment, which requires 24x7 real-time virus protection.
What Is V5R3 Scan Enablement?
To ensure a robust, high-performance solution, V5R3 provides system values to set up a scanning security policy. It also provides scan program open and close exit-point management facilities, and object scan attribute and object scan status information are used to indicate when and how scanning should occur. These key components are all built into the operating system.
A real-time enabled virus scanner and *TYPE2 directories are all that is required to take advantage of this enablement. (For more information on *TYPE2 directories, check out the V5R3 iSeries Information Center. Go to Files and File Systems > Integrated File System > Convert Directories from *TYPE1 to *TYPE2). It should be noted that this scan enablement can be used for more than just virus scanning. You could use it to track the behavior of certain users by recording the date and time of when they access certain stream files.
What Is "Real-Time" Virus Protection, and How Does It Work?
Real-time virus protection is the concept of scanning an object for a virus at the time the object is accessed. (See Figure 1.) For example, assume that a real-time enabled virus scanner has been installed on your V5R3 system and all the appropriate system values are set. You then attempt to open a stream file that contains a virus. The open request flows through the IFS. Using the stream file's object scan attribute, scan status information, and the system scanning policies, the system determines that a scan of the stream file is required. It then gives control to the virus scanner program registered with the open exit-point. The virus scanner program scans the stream file and finds the virus. It then returns control to the system and notifies it that a virus was found. With this information, the system marks the stream file as having failed a scan and then returns control to you with a failed open request. The virus infection and propagation has been stopped immediately! Once a stream file has been marked as failing a scan, it cannot be re-accessed until it has been scanned successfully, perhaps due to new virus scanner code that can fix the virus.
Performing on-access scanning means new virus scanner updates will be used immediately on the next access of a stream file in order to defend against new viruses. There is no need to wait for the weekly virus scan. This is how virus protection needs to work and can work on your V5R3 system.
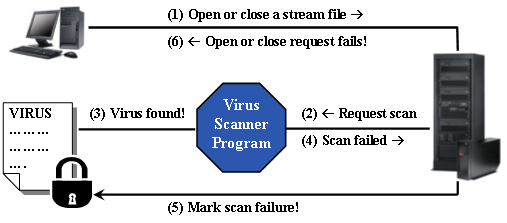
Figure 1: This is how real-time virus scanning works when a PC accesses the i5/OS IFS. (Click images to enlarge.)
Scan Enablement Details
A number of key features provided in V5R3 enable a robust, high-performance real-time virus protection solution:
- System scanning policies
- Two scan-related exit-points for open and close
- Object scan attribute and scan status information
Changing these features requires the user to have all object (*ALLOBJ) and security administrator (*SECADM) special authorities.
First, the available system scanning policies can be controlled via two new system values: scan file systems (QSCANFS) and scan file systems control (QSCANFSCTL), as shown in Figure 2. The first system value allows you to turn scanning on or off for stream files in the "root" (/), QOpenSys, and user-defined file systems. It should be noted that these are the only three file systems that provide real-time scan enablement. The second system value provides options that let you determine how and when you want scanning to occur on your system. For example, the "scan accesses through file server only" option (*FSVRONLY) indicates that only accesses through the file servers, like the Network File System (NFS), will be scanned.
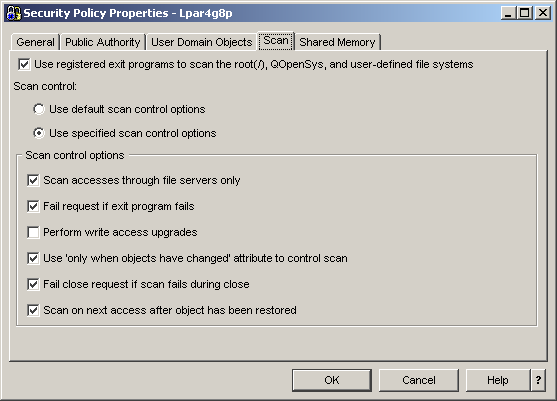
Figure 2: This screen shot shows the new V5R3 scan system values as viewed through iSeries Navigator (Security > Policies > Security Policy).
Next, V5R3 also provides two new scan-related exit-points: Integrated File System scan on open exit program (QIBM_QP0L_SCAN_OPEN) and Integrated File System scan on close exit program (QIBM_QP0L_SCAN_CLOSE). (See Figure 3.) These exit-points provide the link from the system to a virus scanner program during open and close file processing. Associated with every registered scan open or close exit program (virus scanner program) is...
- The user profile used when executing the virus scanner program
- A scan key used to identify a particular virus scanner application
- A scan key signature associated with the scan key
The scan key signature is a key attribute used by the virus scanner program to indicate the level of virus scanning that it provides. For example, assume there is a virus scan program registered with the QIBM_QP0L_SCAN_OPEN exit-point. It has a scan key signature value of UPD_05282004. The virus scanner application then automatically downloads virus definition updates. In order to inform the system of the new level of virus scanning provided, it updates its scan key signature value to UPD_05312004 using the Change Scan Signature (QP0LCHSG) API. The system can now use this information to determine if a stream file needs to be re-scanned because of the new level of virus scanning provided.
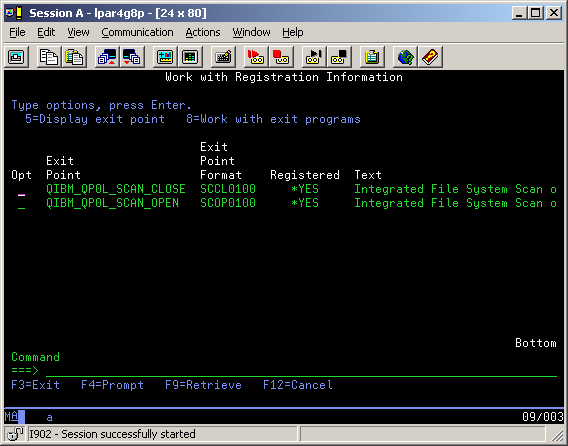
Figure 3: This screen shot shows the two new V5R3 scan related exit-points, which can be displayed using the following command: WRKREGINF FORMAT(SC*).
The final new key feature provided is the object scan attribute and scan status information (Figure 4). i5/OS controls the object scan status information, as opposed to the object scan attribute, which you control. The scan attribute determines whether or not a stream file object should be scanned, if necessary. You can choose to never scan an object by setting its attribute value to "No." Or you can choose to set the attribute value to "only when object has changed" (*CHGONLY). If you want the object to always be scanned if it has been changed or if there are virus scan program or definition updates, you can set the attribute value to "Yes." Note that the actual use of the scan object attribute is tied directly to the QSCANFSCTL system value. For instance, if the system value's "scan on next access after object has been restored" option (equivalent to *NOPOSTRST) is specified, then an object with a scan attribute value of "No" will be scanned once on the next access after the object is restored. In addition, for a scan object attribute of "only when object has changed" to apply, the system value must have the "use only when objects have changed attribute to control scan" option (*USEOCOATR) specified; otherwise, it is treated the same as "Yes."
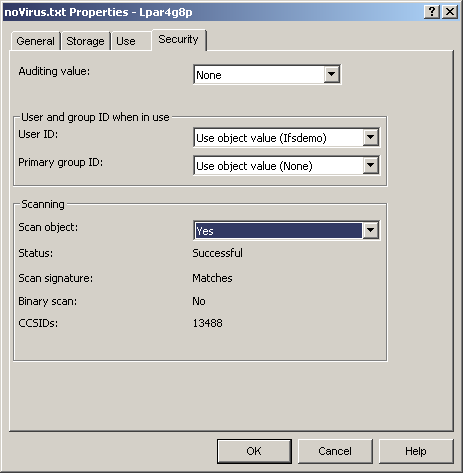
Figure 4: The new i5/OS V5R3 object scan attribute and scan status information can be viewed through iSeries Navigator (Right-click > Properties > Security tab).
The object scan status information includes scan status, scan signatures different, binary scan, coded character set identifier (CCSID) 1 scan, and CCSID 2 scan. An object's scan status indicates whether a scan of the object is required (*REQUIRED), was successful (*SUCCESS), has failed (*FAILURE), is pending a conversion to *TYPE2 directories (*PENDINGCONVERSION), or is not required (*NOTREQUIRED). The binary scan, CCSID 1 scan, and CCSID 2 scan object scan status information indicate the most recent information about how the object was scanned. This is critical because viruses can be detected in binary or in a particular CCSID. The final piece of object scan status information indicates whether the object's scan signature matches its associated global scan signature. If the scan signatures match, the object has been scanned using the latest level of virus scanning available on the system. If they don't match, the object has not been scanned using the latest level of virus scanning available. Note that date and time stamps are not used to determine when scanning is required. This status information is cleared if an object's data or CCSID is changed.
Putting It All Together
A few examples should help you see how V5R3 provides this important real-time virus protection. Scans are performed only when necessary, not on every access, which makes this solution high-performing and scalable. Additionally, i5/OS and the virus scanner work together to ensure scanning always occurs if required according to the system setup, which makes this solution robust.
Assume your system is set up for real-time virus protection and you open a stream file whose scan object attribute is set to "Yes." It gets scanned successfully on the open. The next time you open the same stream file, it will get scanned only if one of the following has occurred since the last access:
- A new level of virus scanning has become available; e.g. new virus definitions
- The object's data or CCSID has been changed
- The object is being accessed in a new way (i.e., different CCSID)
If any of these has occurred, the virus scanner program has the potential to find a virus in the stream file, so a virus scan must be performed. Therefore, if you open a stream file that gets scanned successfully and 1,000 other users open the same stream file in the same way and nothing has changed, your system will only incur the cost of the scan performed on your first open. The system avoids 1,000 extra useless virus scans for the other users!
A scan object attribute of "only when object has changed" can be used to optimize scanning even further. This attribute is designed for stream files that should not be change often or that have come from a trusted source such as i5/OS. Re-scanning such objects just because the level of virus scanning available on the system has been updated is not necessary if the stream files can be guaranteed to not contain a virus. However, if a stream file has been updated, someone may have introduced a virus, so a re-scan would be required. All V5R3 and licensed program stream files built in the IBM Rochester laboratory have this attribute setting.
Unique Scan-Enablement Features
A number of unique features are provided with this enablement. First, you can choose to perform virus scanning during a Save Object (SAV) command to ensure that you are not saving viruses in your weekly backups. In contrast, a Restore Object (RST) command does not perform virus scanning. Instead, you can use the QSCANFSCTL system value to determine whether or not all stream file objects should be scanned at least once after being restored to ensure all such objects restored to your system do not contain a virus, regardless of the scan attribute.
The QSCANFSCTL system value can also be used to perform virus scans only for accesses that come through the file servers, like the NFS. Since many viruses are written to run on Windows, this gives PCs protection when they access data in the IFS, which may be hosting a PC virus. Such viruses cannot execute on the i5/OS, so performing virus scans of native accesses may be unnecessary.
Finally, independent auxiliary storage pools (ASPs) store and maintain their own unique level of virus scanning. This allows an independent ASP to be varied-on to different systems without incurring the penalty of having to re-scan all stream files on that independent ASP, provided the level of scanning on the independent ASP matches that of the system to which it has been varied-on.
How Do I Get "Real-Time" Virus Scan Protection?
To protect your system with real-time virus scanning, you need to upgrade to i5/OS V5R3. Also, the "root" (/), QOpenSys, and user-defined file systems must be completely converted to *TYPE2 directories. Then--and here's the key--you need to purchase a real-time enabled virus scanner application that uses this new V5R3 enablement. One application currently available is StandGuard Anti-Virus from Bytware, Inc.
For more information on V5R3 scan enablement check out the V5R3 iSeries Information Center (Files and File Systems > Integrated File System > Concepts > Scanning Support).
Protect Yourself
The i5/OS is raising the bar for virus protection. However, businesses operating in a heterogeneous environment need real-time virus protection in more operating systems than the i5/OS. Today, some systems are not protected at all, and many others implement the traditional weekly virus protection, which is like having a security guard protecting your business once a week. Moving to real-time virus protection is like having security guards behind every door 24x7. Good luck and enjoy the next generation of virus protection!
Richard Theis is an IBM software engineer on the i5/OS Integrated File System team. His primary focus is the "root" (/), QOpenSys, and user-defined file systems. He can be contacted at



















 More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment.
More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment. TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now.
TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now. Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works.
Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works. Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include:
Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include: Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online