Temporary Files May Cause Permanent Printing Problems
General protection faults (GPFs), page faults, and stack faults that occur when printing are often caused by garbage on the hard drive. Problems include leftover temp files, lost allocation units, cross-linked files, and defragmentation. Therefore, before pursuing a defect in one of the Client Access/400 printer emulators, it is best to clean up the hard drive. This up-front work may resolve the problem and relieve you from having to deal with PTFs, Service Packs, printer drivers, traces, and so on.
Following are the steps to take to clean up your hard drive. When Using Windows 95/98 or Windows NT
1. Close all applications.
2. Click on the Windows 95 or Windows NT Start button, select Programs and MS-DOS Prompt.
3. At the DOS prompt, type SET to find out the name of the TEMP directory. For example, it might say TEMP=C:WINDOWS TEMP or TEMP=C:DOS.
4. Bring up the Windows Explorer, and check the temp directory for any leftover temp files or temp folders. Anything in the TEMP folder is, by default, a temporary file. If you find any, delete them by selecting all of them and then selecting File/Delete on the menu bar (or by pressing the Delete key on your keyboard).
5. From inside Windows Explorer, right-click on the hard drive and select Properties from the pop-up menu.
6. From the Properties dialog box for the hard drive, click on the Tools tab and then click on the Check Now button. This process brings up the ScanDisk utility, which scans the hard drive for lost allocation units and cross-linked files. Select which hard drives you wish to scan, select the type of test you wish to run (usually, a standard test is sufficient), make sure that Automatically fix errors is checked, and click on the Start button. Go back to your hard drive properties again when the program finishes.
7. From the Properties dialog box for the hard drive, click on the Tools tab and then click on the Defragment Now button. This process brings up the Disk Defragmenter utility, which improves the performance of your hard drive. You can use the Select Drive button to choose which hard drive to defragment (it is recommended that you defragment all of your hard drives at this point). Once a hard drive has been selected, click on the Start button to defragment that hard drive.
8. If running the ScanDisk utility reveals any problems, reinstall Client Access/400 for Windows 95/NT (including PC5250) and the Windows 95 or Windows NT printer driver.
When Using Windows 3.1 or Windows for Workgroups 3.11
1. Exit Windows 3.1 or Windows for Workgroups 3.11.
2. At the DOS prompt, type SET to find out the name of the TEMP directory. For example, it might say TEMP=C:WINDOWSTEMP or TEMP=C:DOS.
3. Type CD followed by the temp directory name (for example, CD C:WINDOWS TEMP or CD C:DOS).
4. Go to the temp directory and type DIR*.TMP to check for any leftover temp files. If you find any, type DEL *.TMP.
5. Type either SCANDISK or CHKDSK /F to scan the hard drive for lost allocation units and cross-linked files.
6. Type DEFRAG C: /F /R /H /SE /B to defragment the hard drive. Note: This command automatically reboots the PC when finished.
7. If you do not have SCANDISK, CHKDSK, or DEFRAG, obtain a third-party utility such as Norton Disk Doctor to ensure that the hard drive is cleaned up.
8. If running SCANDISK, CHKDSK, or a third-party utility reveals any problems, reinstall Client Access for Windows 3.1 (including RUMBA/400 or PC5250) and the Windows printer driver.
Note: In either case, you may need to reinstall the operating system to replace important modules that may have been damaged.
— Shannon O’Donnell Associate Technical Editor Midrange Computing
TCP/IP Printer Address Problems
When you add a printer to your TCP/IP network, one of the parameters you have to add in your Domain Name System (DNS) server configuration is the IP address for that printer. If you give that printer device a new IP address at some future time, you may be in for an unexpected surprise. Your AS/400 may continue to use the old IP address instead of your new one. This is because the AS/400 caches the DNS information for a period of time, determined by the DNS server, of up to 24 hours. If you need to use this device with the new address, you have only two choices: You can wait until the DNS server cache time expires and resets itself, or you can IPL the AS/400.
— Shannon O’Donnell Associate Technical Editor Midrange Computing
Microsoft’s Visual Basic (VB) is the premier tool for corporate Windows development. Unfortunately, Version 5, the version in widespread use, has had a troubled existence since its rollout just over a year ago. During that short span, Microsoft has released three Service Packs (what we in the midrange world call PTFs), each with dire warnings about neglecting to download and install them. Fortunately, the final service pack, Service Pack 3, includes all the functionality of the preceding two (plus bug fixes for problems introduced by the preceding two). You can download SP 3 from Microsoft’s Web site at www.microsoft.com/ msdownload/vstudio/sp97/vb.asp. Be warned, though: It’s over 15 MB!
After you download this Service Pack, running the file will find and update your VB installation. If you’re unsure what version of VB you are currently on, click on the Help-About icon from within the VB environment. It should say Visual Basic 5 (SP 3). If you have a lower SP level, or no service level at all, you may want to download the latest Service Pack upgrade as soon as possible.
— Drew Dekreon
Help for Those Who Want to Escape from It All
To write functional, well-behaved CL programs, it is necessary to monitor for escape messages sent to CL commands. But trying to remember the message IDs of all those escape messages is impossible.
Tell me again: What is the CPF message for end-of-file with Receive File (RCVF)? What is the message for an object not found with Check Object (CHKOBJ)?
With Version 4 Release 1 of OS/400, you don’t need to consult hopelessly obsolete manuals or plagiarize other programs or run the command from a command line to determine which escape messages need to be monitored. Simply prompt a command, move the cursor to the top line (where the command name is), and press F1. Roll through the help text, and you will find every escape message that applies to that command.
— Mark Strong BeautiControl Cosmetics
Let’s Make a Date for the End of Month
Q: Is there a way to get an End of Month date from a date data type in RPG ILE? — Alex Fishbein
A: Here’s a three-line solution (Figure 1) that ought to do the trick. This code will add a month, then subtract the *DAYS part, giving you the End of Month date.
— Barbara Morris IBM Toronto Lab, RPG Compiler Development
API Really Means “Apply Patch Immediately”
The AS/400’s HTTP server provides an excellent way to gather information from your customers and suppliers. To make this task easier, IBM provides several APIs that allow you to process data entered on a form on a Web page with the languages most familiar to AS/400 programmers, such as RPG and COBOL. Unfortunately, if you have upgraded to V4R1 or higher, you have probably discovered that the API QtmhCvtDb (Convert to Database) no longer processes form data correctly.
QtmhCvtDb is used in conjunction with another API, QtmhStdIn (Standard Input), to map data entered into a Web page form to fields in a physical file. Figure 2 shows the code for a simple form that allows a customer to enter name and address information in order to be added to a mailing list that is stored in a physical file. (For this example, Name and Address serve as the name and address.) Clicking on the Process Form button initiates a call to the CGI program TESTRPG001. (This is specified as the action on the form tag.)
A call to QtmhStdIn retrieves the data from the standard input buffer of the HTTP server and returns the following string to the CGI program:
name=Anyone&address=Anywhere
The API QtmhCvtDb is then called to map the data entered into the corresponding fields of a physical file. At this point, the physical file field “name” should have a value of “Anyone” and the field “address” should have a value of “Anywhere”.
Unfortunately, QtmhCvtDb contains a bug that causes corruption of the data entered in the last form element. If the last form element has a size of one, the data entered is lost entirely; if the form element has a size other than one, the value of the address is returned as a string containing the data entered followed by garbage. Therefore, in this example, address is returned as “Anywhere” plus 32 indecipherable characters that do not look very nice on a mailing label!
Fortunately, there is a simple way to overcome this obstacle. Simply add the following line of code as the last element of the HTML table:
This code causes the corrupted data to be parsed into the hidden field, where it no longer poses a problem. Until a PTF is announced to correct the situation, using this method provides a simple fix.
— David Mayle
Head ’em Up, Move ’em Out!
I created a command called Change Column Heading (CHGCOLHDG), which allows you to easily change the column heading or text description for a previously created file. The example shown in Figure 3 is the equivalent to the following DDS keywords and parameters:
COLHDG(‘THIS’ ‘IS’ ‘FIELDA’)
TEXT(‘THIS IS FIELDA’)
The CHGCOLHDG command accomplishes this task by using Query Manager queries and SQL to execute a LABEL ON SQL statement. Every machine since Version 2 Release 1 of OS/400 has Query Manager, so everyone should be able to take advantage of this command.
The CHGCOLHDG utility consists of three objects: command CHGCOLHDG, CL program PL0001C, and RPG IV program PL000R1. You can download source code for these objects at www.midrangecomputing.com/99/03.
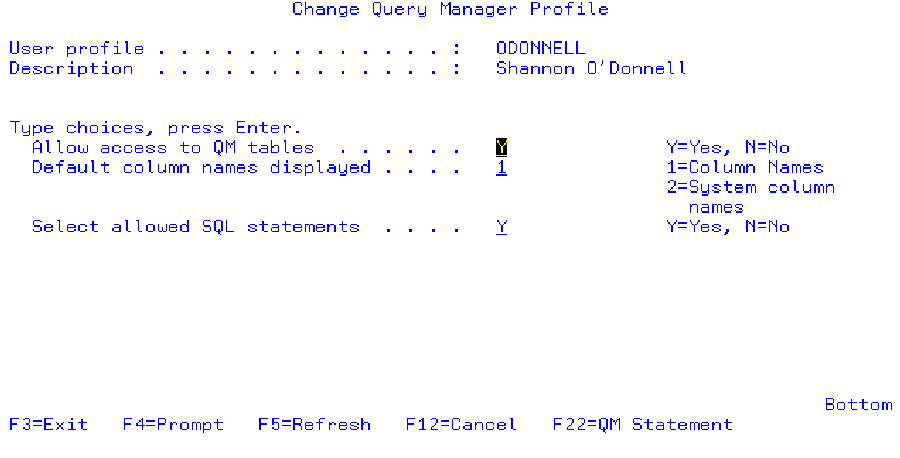
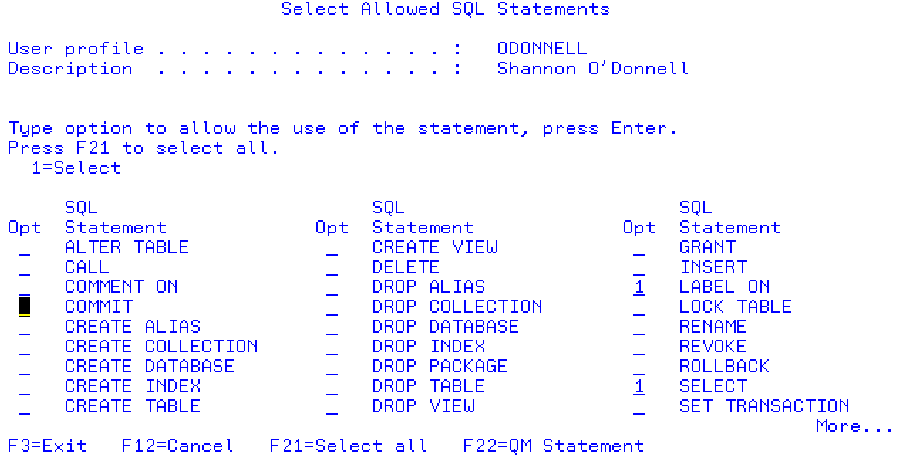
You must have authority to use LABEL ON in QM. To ensure that you have the required authority, type in the command Start Query Manager (STRQM) on a command line and press Enter. This will start the DB2 Query Manager for AS/400 menu. Now, select option 10, Work with Query Manager Profiles. Find your user profile on the next panel and enter a 2 beside it to change it. Next, use the roll keys to scroll forward three screens, and you’ll see a panel like the one shown in Figure 4. Enter a Y at Select allowed SQL statements. Press the Enter key, and you will see a panel like the one shown in Figure 5. On this panel, enter a 1 on the LABEL ON entry line and press the Enter key.
This command is easier to use than Change Physical File (CHGPF) because you can embed this command in a CL program or execute it from a command line. Also, you do not need to hunt down the original DDS that created the file. This command provides an
easy method to change file text and column headings, and, best of all, you don’t need to know SQL!
— Paul Ladouceur
Editor’s note: Be aware that failure to change the DDS from which a file was built may cause problems later. If someone rebuilds the file from the DDS, the changes you’ve made with CHGCOLHDG will be lost.
I’m Sorta Partial to My Key
The code fragment in Figure 6 is an RPG IV example of a DOW loop that executes while part of a field is equal to a “key” or predetermined literal. I use it to load to a subfile part numbers or customer numbers that begin with a specific character sequence. The comparison can be made to a variable that a user enters.
— Jeff Kinzer Porter Cable Corp.
ODBC Has Your Number
One of the hardest things about client/server programming on the AS/400 is finding your ODBC job. The Work with Active Jobs (WRKACTJOB) command will list all of the jobs running in the QSERVER subsystem, which is where all ODBC prestart jobs run. If your shop is like mine, you have many ODBC users cluttering up the screen, and the user is always displayed as QUSER! To find the logged in user profile, you have to display the job log of each QSERVER job until you see the user profile you want to debug. This is a time-wasting pain in the posterior, to say the least.
Enter the most useful stored procedure in the world! Stored procedure RETJOBI eliminates the need to search for a particular ODBC job! As you can see in Figure 7, the code for this procedure is only four lines long. It begins with the declaration of a CL variable to hold the job number, and then it executes a call to the Retrieve Job Attributes (RTVJOBA) command to return the number of the job currently running. Once you wrap this command by issuing a CREATE PROCEDURE statement in your ODBC program, you will be able to call it as a stored procedure and see your job number.
I have found this technique so useful that this procedure is called from every program in my shop, and the job number is then posted on each screen in the application. This way, my operators can tell me their job number when they have a problem, and I can use the Display Job Log (DSPJOBLOG) or the Work with Jobs (WRKJOB) command to see why they are having problems.
Please note that ODBC job names are QZDASOINIT for Windows 95/NT and QZDAINIT for Windows 3.x. jobs. To display the job log of a Windows 95/NT ODBC job, you would type DSPJOBLOG xxxxxx/ QUSER/QZDASOINIT, where xxxxxx is the job number returned by the stored procedure.
To prepare the RETJOBI command for execution, use the Create Bound CL Program (CRTBNDCL) command to create an executable version of the RETJOBI program in your QSYS library. Be aware, however, that, when you upgrade to the next release of OS/400, you may lose what you had in QSYS. Perhaps a better approach might be to put the object in QGPL. Next, execute the following statement from an interactive SQL session:
CREATE PROCEDURE QSYS/RETJOBI (INOUT :job CHAR(6)) EXTERNAL NAME QSYS/RETJOBI
SIMPLE CALL;
Once the create procedure statement has been executed, DB2 knows what arguments the procedure will accept and their data type. You are now ready to execute code like that shown in Figure 8 to find your job number.
This code was written using VB 5.0. For the code to work, create a VB form inside the program with a command button labeled Command_1. When the user clicks Command_1, the VB code executes and displays the user’s AS/400 job number. When you enter this code into VB, be sure to do the following:
1. Activate the following VB Project References in the program: the Microsoft ActiveX Data Objects 2.0 library and the Microsoft ActiveX Data Objects Recordset 2.0 library. Project references are activated in VB 5.0 by clicking Project from the VB dropdown menu and then clicking References. Find these entries and place a check mark next to them. If they are missing from your VB references, download and install the Microsoft Data Access Software Development Kit (SDK) and the Microsoft Data Access Components Version 2.0 from the Microsoft Universal Data Access Web site at www.microsoft.com/data/download.htm. This download fixes problems with the earlier releases, adds connection pooling, and provides better parameter object support. I don’t recommend running this code without the new components.
2. Replace the “AS/400” literal in the CON1.OPEN line with the name of your ODBC data source name. Also in that line, replace the “HOWARD” literal with a valid AS/400 user name for your system, and replace the “PASSWORD” literal with the password for that user.
Once these changes are in place, you can retrieve your AS/400 job number at will. — Howard Arner
Identify That Trigger-happy Program
Q: Is it possible for a trigger program to determine what program caused it to fire? — Don Johnson
Lebanon, PA
A: The ILE procedure RtvTgrCaller shown in Figure 9 will do the trick. This module can be bound into your trigger program or, much better, added to a service program, which must be compiled with ACTGRP(*CALLER).
Procedure RtvPgmCaller, which can be found on the MC Web site (www.midrange computing.com/mc/99/03), returns a 277-byte character variable (Figure
10) containing four pieces of information: the name of the program that fired the trigger, the type of program, the name of the module, and the name of the procedure. Look at the code fragment in Figure 9 for an example of how to call this procedure.
This procedure relies on some convenient OS/400 and DB2 behavior, which makes it vulnerable to any changes IBM makes in DB2/400. However, short of IBM supplying an API or adding the name of the trigger program to the trigger buffer, in my opinion, this is about as good as it’s going to get.
— Derek Butland
C d1 adddur 1:*m tempd
C extrct tempd:*days days
C tempd subdur days:*days tempd
Figure 1: Here’s a handy method to determine the date of the last day of the month.
QtmhCvtDb API Fix
Name Address
Figure 2: Use this HTML form to allow entry of a name and an address.
CHGCOLHDG FILE1(TEST1) FIELD(fieldA) +
TEXT(THIS IS FIELDA) HDG1(THIS) +
HDG2(IS) HDG3(FIELDA)
Figure 3: CHGCOLHDG allows you to change column headings and text descriptions.
Figure 4: Enter a Y in the STRQM Select allowed SQL statements field.
 |
 |
Cmd1.Parameters.Append Prm1
'execute the command
Cmd1.Execute
'show user the job number
MsgBox "Your job number is: " & Cmd1.Parameters("job").Value
'Release the command and the connection
Set Cmd1 = Nothing
Set Con1 = Nothing
Figure 8: This VB code connects to an AS/400 and executes the RETJOBI procedure.
/COPY QRPGLESRC,PROTOTYPES
D PgmName S 10A
D dsTrgCaller DS
D dsPgmName 10A
D dsPgmType 1A
D dsModName 10A
D dsPrcName 256A
......
* To just get program name...
C EVAL PgmName = RtvTrgCaller
C
* OR, to get all the information...
C EVAL dsTrgCaller = RtvTrgCaller
Figure 9: This program example uses RtvTrgCaller to find the name of a trigger program.
Positions Length Description
1-10 10 Program name 11-11 1 Program type 12-21 10 Module name 22-277 256 Procedure name
Figure 10: The RtvPgmCaller procedure returns information about the caller in a 277-byte data structure.











 Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online