In 1998, IBM enhanced the PC5250 program to support the bypass sign-on option so that PC5250 users could automatically sign on to the AS/400 by using the default password contained in their Client Access for Windows 95/NT routers. In that implementation, the router password flowed to the AS/400 in the clear, meaning that, if you placed a line trace on your communications line, you could match an individual’s AS/400 user ID to its associated password by looking at what was transmitted over the “wire.” If the wire is an internal LAN, the security exposure is not large; however, if you are running over a TCP/IP network, this scenario could endanger your AS/400 security by allowing hackers to easily capture user IDs and passwords as they are transmitted. To combat this problem, IBM has programmed AS/400 Client Access Express for Windows (Express client) to use the Secure Sockets Layer (SSL) protocol to prevent information from being transmitted in the clear.
SSL provides a means of encrypting information so that hackers will not be able to snatch a user ID and password from the TCP/IP line flow. In this article, I’m going to look at SSL and how you implement it in your PC5250 sessions. I’ll define what SSL is, the software products required to run SSL, how you install it on your PC, and how you configure your Express client PCs to take advantage of this valuable feature. Please note, however, that I will only cover the basics of Express client PC5250 SSL here. To help you with some of the finer points of configuring PCs and the Express client for SSL, visit the AS/400 Information Center at publib.boulder.ibm.com/pubs/html/as400/infocenter.htm. Once you enter the Information Center, click on Client Access Express/Administering/Connection Administration/Secure Sockets Layers administration.
Okay, Just What Is SSL?
SSL is a popular security scheme that allows the PC client to do two things:
• Authenticate the identity of the computer you are attaching to
• Provide a method for encrypting all data and requests that pass between the client and the host server
It’s important to remember that an SSL-enabled session involves both authentication and encryption. Express client allows SSL communications with the AS/400 server at three levels of encryption (using 40-bit, 56-bit, and 128-bit encryption key technology). The encryption level you can use will vary depending on where your organization is geographically located. For example, IBM could ship 128-bit encryption to
Canada and the United States, while France, at least in the past, has only allowed a maximum of 40-bit encryption to be imported. The rest of Europe allowed 56-bit encryption.
In addition to the three levels of encryption, there are two types of authentication: server authentication (i.e., Are you really connecting to the server you think you are?) and client authentication (i.e., Is the client attaching to your AS/400 approved to access your server data?). Express client PC5250 supports server authentication. Server authentication is beneficial when you really need to establish the identity of the server you are talking to. For example, you probably want to ensure that, when you send your credit card number to
L.L. Bean, you are communicating with the L.L. Bean server and not some hacker’s
system.
How Does PC-AS/400 Encryption Work?
Encryption involves three keys: public, private, and negotiated. The public keys are provided to users who install SSL on their computers. Both public and private keys are used for encrypting and decrypting the data initially exchanged between the PC and the AS/400. Keys are exchanged via digital certificates. Data from the AS/400 is encrypted using the private key and anyone with the corresponding public key can decrypt the data sent from the server. Data sent from the PC is encrypted using the public key. This data can only be decrypted by the AS/400 that has the private key. This is called asymmetric (or public key) cryptography. Once the PC has authenticated that the server actually is who it claims to be and the two computers establish a session, the PC and the AS/400 negotiate a third key, which is then used for private communications throughout the rest of the conversation. When the negotiated key is used, this is call symmetric cryptography. Negotiated keys are required for each client and server connection and negotiated keys expire after 24 hours.
The public keys are provided via a digital certificate. A digital certificate validates the certificate’s owner. A “trusted” party (called a Certificate Authority) issues certificates for both the client and servers. Digital certificates can be obtained as follows:
• Purchased from well-known authorities such as Verisign and RSA
• Purchased from unknown authorities, i.e., those that are provided by authorities outside the generally accepted list provided by OS/400 or Client Access. (I wouldn’t recommend using these.)
• Created on your AS/400 by using the Digital Certificate Manager You can set up PC5250 to take advantage of SSL by doing the following:
• Setting up both your AS/400 and your PC to use SSL
• Providing digital certificates on both your AS/400 and PC
• Enabling your PC5250 configuration to use SSL
AS/400 Products to Order and Install
In order to use SSL in your Express client configurations, you must order and load the following AS/400 Licensed Program Products (LPP) on your AS/400:
• IBM Cryptographic Access Provider for AS/400 (5769-ACn; where n=1, 2,
3)—The n designation specifies the encryption level you are supporting. 1 = 40-bit encryption, 2 = 56-bit encryption, and 3 = 128-bit encryption. The encryption level you can order and install depends on what export controls are in force for encryption technology in your geographic area.
• IBM HTTP Server for AS/400 (5769-DG1)
• TCP/IP Connectivity Utilities for AS/400 (5769-TC1)
• Digital Certificate Manager (DCM), Option 34 of OS/400 (5769-SS1)
• IBM Client Access Express (5769-XE1)
• IBM Client Encryption (5769-CEn; where n=1, 2, 3) Configuring Express Client to Use SSL
Once these products are ordered and installed on your AS/400, there are three steps you must complete to enable your Express client users to use SSL security:
1. Set up your AS/400 to create, manage, register, and administer digital certificates to applications and users. Digital certificates are assigned through the Digital Certificate Manager, which runs under the IBM HTTP Server for AS/400. The DCM creates the Certificate Authority and manages system certificates on your AS/400. In addition, the DCM administers certificates for any AS/400-based applications (such as the Express client servers) that need certificates to establish an SSL session with a client. Configure the IBM HTTP Server and the Digital Certificate Manager on your AS/400 so that these applications can administer your SSL setup.
2. Configure the Express client servers on your AS/400 to use SSL. There are multiple AS/400-based Client Access Express application servers—including the Telnet server (which is used for PC5250 connections), the database and file servers, and the sign- on server—that provide services to Express client users. Each of these AS/400 servers that you want to configure for SSL usage must also be assigned a digital certificate from the Digital Certificate Manger.
3. On each Express client PC that uses SSL, you must install the SSL component of Express client and download a certificate authority file from your Certificate Authority on the AS/400. If you’re using a well-known Certificate Authority, such as Verisign, then a download of a certificate authority file is not required since this file is shipped along with Client Access Express.
Because of space limitations, I cannot go into detail on each of these steps but, fortunately, I don’t need to. The AS/400 Information Center Web site contains detailed instructions for performing these three necessary tasks. To find instructions for getting started with digital certificates, click on the Internet and Secure Networks/Digital certificate management drop-down at the AS/400 Information Center (publib.boulder.ibm. com/pubs/html/as400/infocenter.htm). To find the instructions for configuring your Express client servers and desktops to use SSL, click on the Internet and Secure Networks/Securing applications with SSL drop-down on the site.
There is one thing to remember when you’re working with certificates. For ease of use, ordering, and administration, all digital certificate administration and assignment must be performed through your AS/400. When you install the Express client SSL component, that installation must be performed from your AS/400, not from your Express client CDROM or from a prior installation on your network or on a PC. You will need to use the AS/400’s Digital Certificate Manager whenever you are working with AS/400-assigned certificates.
Downloading Your Own Certificates to a PC
If you use a well-known Certificate Authority (Verisign, Thawte, etc.) to provide your server certificates, you do not need to do anything except install SSL support on both the PC and the AS/400. The well-known Certificate Authorities certificates are shipped in the default Client Access Express key database and with the AS/400 Digital Certificate Manager.
However, you can also create your own certificates by using the AS/400 Digital Certificate Manager. These certificates will be stored on your AS/400. (Information on creating your own Digital Certificates can also be found at the AS/400 Information Center Web site under the Internet and Secure Networks/Digital Certificate Management/Using Digital Certificates drop-down.) Once your certificates are created, you can download the public certificates to your PCs by using a new tool provided by the Client Access development team, the AS/400 Certificate Authority Downloader utility (CwbCoSSL), which can be downloaded at the Client Access Download Web site at www.as400.ibm.com/clientaccess/cadownld.htm. The CwbCoSSL program (see Figure 1) automates the process of downloading your custom certificates to the Client Access
Express key database, which contains your digital certificate. The following is the default key database file for Express client:
C:Program FilesIBMClient AccessCWBSSLFD.KDB
The name of this database can be viewed or changed via the Client Access Properties page (Figure 2). The CwbCoSSL utility requires Client Access Express Service Pack SF55256 or above. Please read the cwbcossl.txt file for more information. The file is packaged in the self-extracting Zip file that comes with the download.
Setting Up Your Express Client Connections
After your Express client PC is ready for SSL, you can configure your PC so that each Express client connection between the PC and the AS/400 uses SSL. This is accomplished via the Operations Navigator properties for each system. (See Figure 3.) The Connections properties screen is accessed in Express client by right-clicking on the icon representing your AS/400, selecting Properties from the context menu that appears, and then selecting the Connections tab. On the Connections panel that appears, click on the Use Secure Sockets Layer (SSL) checkbox to indicate that each Express client connection to that AS/400 should be established under SSL. When using Operations Navigator, the left side of the panel will show any AS/400 systems that have been secured via SSL. Each AS/400 that is configured for SSL will have a lock displayed alongside its AS/400’s system icon.
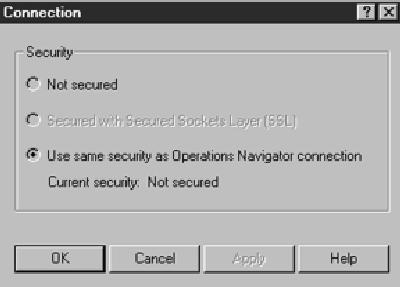
To use SSL inside PC5250, go to the PC5250 Configuration panel (which is accessed by clicking on the Configure option of the Communication pull-down menu on the PC5250 menu bar). After selecting your AS/400 System name, clicking on the Properties button next to the AS/400 System Name will allow you to select your PC5250 SSL security through PC5250’s Connection screen (see Figure 4). You have three SSL options that you can specify on this screen: Not secured, Secured with Secured Sockets Layer (SSL), or Use same security as your Operations Navigator connection. The SSL setting you choose will override the setting you defined in your Operations Navigator connection for this AS/400. For example, if Operations Navigator has no security for this system, you can override that setting and specify that your PC5250 session run with SSL security. The default is to use the Operations Navigator SSL setting, as specified in the Use Secure Sockets Layer (SSL) check box described above.
Please note that there is very little performance degradation when using SSL in a display emulation session. This is logical because there is only a very small amount of data that flows between the PC and the AS/400 during an emulation session. However, there could be a larger performance degradation with PC5250 printer emulation if the print output is large.
And That’s It
As you can see, configuring your Express client and PC5250 setups to use SSL isn’t that difficult if you just know the ropes. By installing the correct products on your AS/400 and using the techniques and references in this article, you can easily start encrypting your Express client sessions for SSL today.
Related Materials
AS/400 Information Center Starting Point: publib.boulder.ibm.com/pubs/html/as400/infocenter.htm Client Access Download Web site: www.as400.ibm.com/clientaccess/cadownld.htm
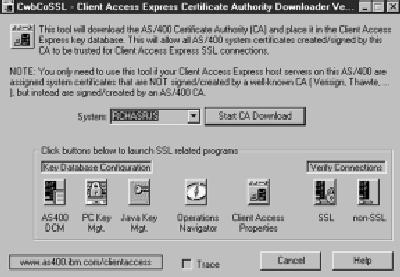
Figure 1: The cwbcossl utility automates the process of downloading custom digital certificates to the Client Access Express key database.
Figure 2: The default encryption key database file can be changed by using the Client Access Properties page.
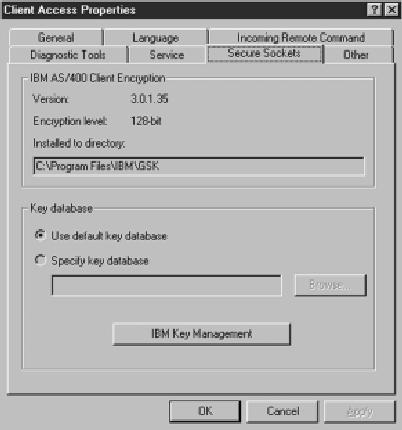
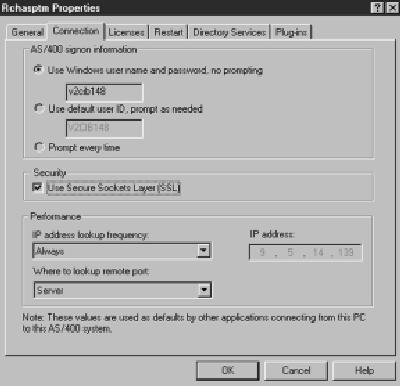
Figure 3: Using OpsNav, you can configure your PC so that each Express client connection between the PC and the AS/400 uses SSL.
Figure 4: Specify whether your Express client PC5250 session uses SSL with the Connection panel inside the Configure PC5250 panel.




















 More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment.
More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment. TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now.
TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now. Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works.
Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works. Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include:
Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include: Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online