Is there a difference between services available in a private cloud and those available in a public cloud?
Editor's note: This article is excerpted from chapter 5 of IBM Cloud Platform Primer.
A key distinction between Infrastructure as a Service (IaaS) and Platform as a Service (PaaS) is the type of service offered by each segment. With IaaS, consumers usually work with virtualized servers, which they can configure themselves, whereas with PaaS, the consumer uses and works with services that are created and maintained by the cloud service provider. Figure 1 captures the basic differences between IaaS and PaaS.
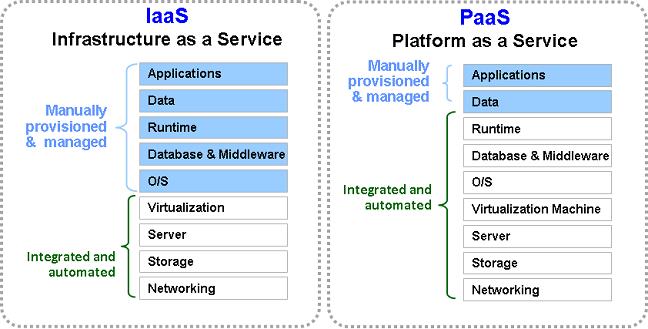
Figure 5.1: Difference between IaaS and PaaS
When PaaS is discussed, it is often construed to be in the private cloud domain. But in fact these services are increasingly available on public clouds. Is there a difference between services available in a private cloud and those available in a public cloud? From a cloud-service consumer perspective, it shouldn’t matter, although if the consumer is an enterprise client, questions of security and workload isolation come up. But from the cloud-service provider perspective, many things need to be addressed.
Recently, we’ve been hearing a lot about public PaaS platforms such as Heroku, Bluemix, and Azure. They all run on some infrastructure, the services for which are provided by hosting providers such as Rackspace, SoftLayer, and Amazon Web Services. This chapter touches upon IaaS, using IBM’s SoftLayer to explain the concepts. References to other products illustrate the fact that there is quite a bit of commonality between cloud hosting providers.
Characteristics of a Public Cloud
In its broadest definition, a public cloud is a set of computing resources set up based upon a cloud computing model in which a service provider makes resources publicly available over the Internet. There are basically three types of resources—compute, storage, and network—which may be offered free on a trial basis, for a fixed monthly fee, or on a pay-as-you-go model. IaaS providers host hardware, middleware, servers, storage, and other infrastructure components for their users. IaaS providers can also host users’ applications and handle tasks such as system maintenance and backup. In addition to the three cloud service models, NIST has defined four deployment models, shown in Figure 2. These deployment models are classified according to where the service is running and what kind of access is provided.
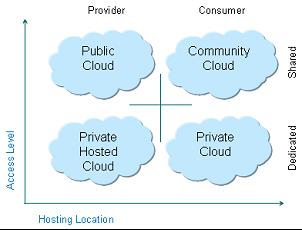
Figure 5.2: Cloud deployment models
Enterprises have security concerns, which I discuss in a later section. Notwithstanding those concerns, the many benefits to public cloud computing include
- All resources are readily available for clients to start quick deployments.
- Clients pay only for resources that are consumed.
- Resources can be rapidly scaled based on need.
- All services are delivered in a consistent manner.
Figure 3 shows a cloud network topology. It depicts the cloud environment as accessible from the Internet over a public or external network. The routing switch, or cloud gateway, uses the internal network to communicate with cloud resources. These resources, which can be virtual machines or bare-metal servers, are accessible via various ports within the cloud. If one were to add more details to this figure, one could show the cloud load balancers, which route traffic to different instances in the cloud; caching instances; database instances; and other cloud block storage components.
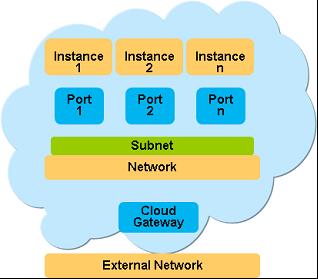
Figure 5.3: Public cloud network topology
Cloud service models are also defined by the ownership and degree of customization allowed, which translate into cost, control, and elasticity. Those metrics determine whether the cloud services are fully managed or unmanaged and how much can be done in-house versus what can be outsourced.
Managed vs. Unmanaged Services
Cloud services typically come in one of two forms: managed and unmanaged. Managed services offer support for every task and problem related to the resources hosted by the provider. With unmanaged services, the provider will replace failed hardware components but does not support software installations or patch upgrades. Some cloud providers offer both managed services and unmanaged services, but with support for backup and restore services.
An enterprise’s in-house expertise, consumption appetite, and costs will dictate which option it chooses. While some clients choose unmanaged servers, apply their own security configuration, and use the servers for rapidly deploying development and test environments, others may have a fully managed infrastructure for rolling out their production topology. Table 5.1 lists some of the features of both managed and unmanaged services.
|
Managed Services |
Unmanaged Services |
|
Operating system deployment and management |
Operating system deployment |
|
Client is given controlled access to operating system |
Client is given complete control over operating system |
|
Monitoring and notification |
Unrestricted access to servers and any software the client needs installed |
|
Maintenance and routine patching |
Initially cheaper to sign up because there is no management or maintenance support |
|
Backup and restore services |
Client is responsible for backing up components |
|
Disaster recovery and storage services |
Client is responsible for storage and recovery |
|
Security services |
Client is responsible for installing security patches |
|
OS-based service-level agreements |
Hypervisor-only or infrastructure-only service-level agreements |
Table 5.1: Managed versus unmanaged cloud services
Unmanaged servers are less expensive and give you greater freedom to control your servers, whereas managed servers mandate the use of certain processes and tools for control. With unmanaged servers, one also inherits the risks of misconfigurations and the responsibility of dealing with application failures. Managed cloud services usually come with a more long-term agreement between the cloud service consumer and the cloud service provider. So, while both types of services have their advantages and disadvantages, the key is to understand your own organization’s skill set and needs and choose appropriately.
Note: As a common practice, enterprises tend to opt for managed services for their production environments and choose unmanaged services for non-production environments.
Workload Isolation and Security
Workload isolation involves placing workloads in the cloud such that the resources they use do not adversely affect other applications running in the same cloud. In contrast, security deals with keeping applications, especially the data, private and secure from other applications in the cloud.
In addition to providing workload security, cloud service providers are often faced with demonstrating workload isolation. While workloads might share common pools of resources under normal circumstances, they need to be isolated from each other so that problems in one workload do not affect other workloads. Similarly, sensitive data in one workload should not be visible in any shape or form to other workloads. Isolated workloads each get their own set of dedicated resources.
Other levels of isolation include network isolation, isolation of management networks, data network isolation, and isolation of IP storage networks. Isolation can be physical or logical. Physical segmentation of networks, allowing only authorized administrators access to networks, and using non-routable networks are some of the ways of keeping each client’s environment separate from other clients’ environments. While cloud service providers strive to provide these various levels of isolation, the inherent isolation provided by cloud containers is one of the main reasons that the use of container technology is increasing. I discuss containers later in this chapter.
Note: Physical isolation means the resources are running on separate hardware. Logical isolation uses hardware-management software to make a single set of hardware work like multiple, separate sets of hardware.
In a private cloud platform such as the PureApplication System, workload isolation is facilitated through cloud groups and smart placement algorithms. Cloud groups contain compute nodes and a reference locator, such as an IP group. Thus a cloud group has all the components needed to run virtual machines, as shown in Figure 4.
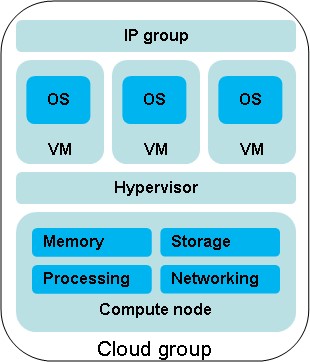
Figure 5.4: A cloud group in PureApplication System
Placement of the virtual machine instance is crucial to achieving workload isolation. When placing a new VM instance, the placement algorithm in PureApplication System selects the compute node based on effective capacity. Resources such as CPU, memory, data network bandwidth, and storage network bandwidth are used in the placement calculation. For more information about workload isolation in PureApplication System, see www.ibm.com/developerworks/cloud/library/cl-ps-aim1302-workisolation/.
In the public cloud, workload isolation is provided by the underlying cloud infrastructure. Along with placement constraints, a combination of networking and security technologies is used to isolate traffic.
You’ve likely heard it said that you should not trust a cloud service provider to protect your corporate assets. Indeed, security has become the most common inhibitor for enterprises that would like to adopt cloud computing, and rightfully so. Two facets of security—threats and compliance—dictate access controls. On one hand, enterprises are forced to address a growing number of mandates, including national regulations, local mandates, and industry standards. On the other hand, enterprises have to shield themselves from threats both external and internal. Enterprises must be constantly vigilant against threats ranging from cyber attacks and corporate espionage to disgruntled employee actions and careless internal breaches.
Even though many of the security concerns are not new, to gain the trust of organizations, cloud service providers must meet or exceed the security and privacy that’s available in traditional IT. Additionally, sensitive data such as credit card information stored on-premises should always be encrypted. Some cloud service providers offer encryption services within their cloud-based storage. Many third-party security products, such as CipherCloud and SecureCloud, monitor the data that’s stored in the cloud and prevent malicious data from penetrating the client’s system. A website being hosted in the cloud can use website protection services.
Once cloud security requirements are understood, we can use the Cloud Computing Reference Architecture with foundational security controls when designing, deploying, and consuming cloud services. The controls around security are
- cloud governance
- risk management and compliance
- security incident management
- identity and access management
- discovery, categorization, and protection of data and information assets
- virtual systems acquisition, development, and maintenance
- management of threats and vulnerabilities
- physical and personnel security
The need for privacy and security is why many enterprises start with a private or on-premises cloud that has such security controls. Once an enterprise has processes in place to protect virtualized environments from outside attacks, it can move into hybrid and public cloud solutions.
Virtualization is fundamental to cloud computing. But the proliferation of virtual images raises the risk of malicious attacks and exploitation of security flaws. Remember, the hypervisor is the traffic cop that controls multiple images of various resources. The hypervisor relies on the underlying operating system to manage and protect the applications and interfaces. It all boils down to protecting the integrity of customer data and ensuring a good customer experience. End users and customers are mainly concerned about the quality of service within a secure environment.
Note: From data breaches to shared technology vulnerabilities, the Cloud Security Alliance’s Top Threats Working Group has identified the top nine cloud computing threats, which it calls The Notorious Nine. You can download the report at cloudsecurityalliance.org/download/the-notorious-nine-cloud-computing-top-threats-in-2013/.
Editor's note: To find out more, read IBM Cloud Platform Primer.















 Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online